Python based Packet Filtering Firewall
Description
Python based Packet Filtering Firewall Application.
There are several benefits of using a firewall in a network:
- Prevent the exposure of sensitive hosts, resources, and applications to untrusted users.
- Sanitize protocol flow, which prevents the exploitation of protocol flaws.
- Block malicious data from servers and clients.
- Reduce security management complexity by off-loading most of the network access control to a few firewalls in the network.
Firewalls also present some limitations:
- A misconfigured firewall can have serious consequences for the network, such as becoming a single point of failure.
- The data from many applications cannot be passed over firewalls securely.
- Users might proactively search for ways around the firewall to receive blocked material, which exposes the network to potential attack.
- Network performance can slow down.
- Unauthorized traffic can be tunneled or hidden as legitimate traffic through the firewall.
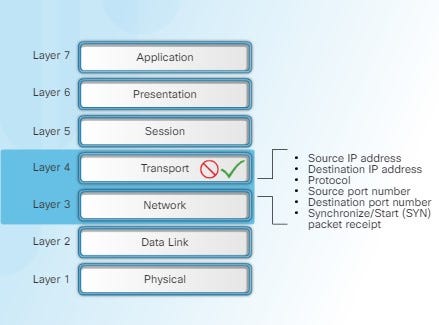
Packet filtering firewall — Typically a router with the capability to filter some packet content, such as Layer 3 and sometimes Layer 4 information.
Packet filtering firewalls are usually part of a router firewall, which permits or denies traffic based on Layer 3 and Layer 4 information. They are stateless firewalls that use a simple policy table look-up that filters traffic based on specific criteria.
For example, SMTP servers listen to port 25 by default. An administrator can configure the packet filtering firewall to block port 25 from a specific workstation to prevent it from broadcasting an email virus.
There are several advantages of using a packet filtering firewall:
- Packet filters implement simple permit or deny rule sets.
- Packet filters have a low impact on network performance.
- Packet filters are easy to implement, and are supported by most routers.
- Packet filters provide an initial degree of security at the network layer.
- Packet filters perform almost all the tasks of a high-end firewall at a much lower cost.
- Packet filters do not represent a complete firewall solution, but they are an important element of a firewall security policy.
There are several disadvantages of using a packet filtering firewall:
- Packet filters are susceptible to IP spoofing. Hackers can send arbitrary packets that meet ACL criteria and pass through the filter.
- Packet filters do not reliably filter fragmented packets. Because fragmented IP packets carry the TCP header in the first fragment and packet filters filter on TCP header information, all fragments after the first fragment are passed unconditionally. Decisions to use packet filters assume that the filter of the first fragment accurately enforces the policy.
- Packet filters use complex ACLs, which can be difficult to implement and maintain.
- Packet filters cannot dynamically filter certain services. For example, sessions that use dynamic port negotiations are difficult to filter without opening access to a whole range of ports.
- Packet filters are stateless. They examine each packet individually rather than in the context of the state of a connection.
Packet filtering is a firewall technique used to control network access by monitoring outgoing and incoming packets and allowing them to pass or halt based on the source and destination Internet Protocol (IP) addresses, protocols and ports
Firewalls are configured using simple if then rules. In a packet filtering firewall, a rule says: if a pattern based on packet source, destination, protocol, or service is a match THEN take the specified action. Since there are many rules involved, the order of the rules matters. A LOT!
Traffic is verified against a rules table in order, top to bottom. Therefore, you must be careful as to how you define your rules and in which order should you place them. Its best to begin very strict and lay off as you go down the table.
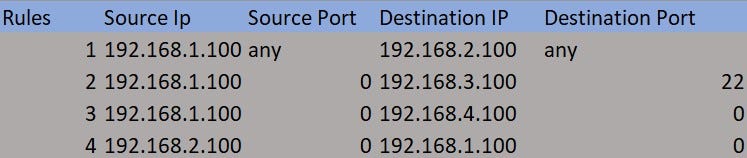
Rule Syntax
NOTE : By default all the traffic Denied!. Empty File makes DEFAULT DENY TRAFFIC.
Deny packet Based on Source 192.168.1.100:0 to Destination 192.168.2.100:0
Rule File
We’ll use a CSV file as our rules table.
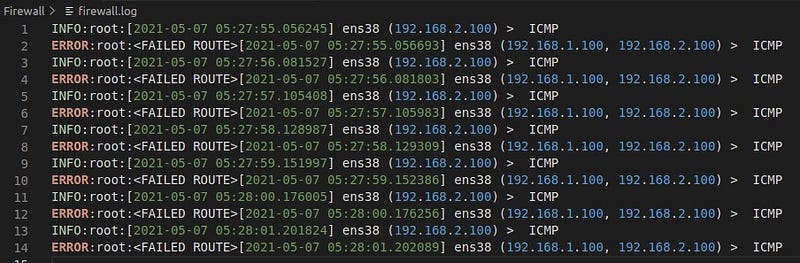
The logging feature documents how the firewall deals with traffic types. All the logs will be saved in a Log file
Allow Traffic Logs
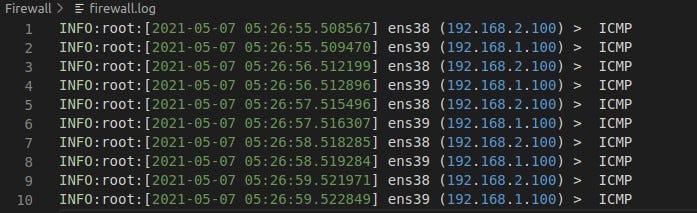
Deny Traffic Logs
Basically, This firewall auto detects the interfaces which has attached and then listen to each and every interfaces using the threading module. Interfaces are running on threads to receive and send traffic simultaneously.
EXAMPLE
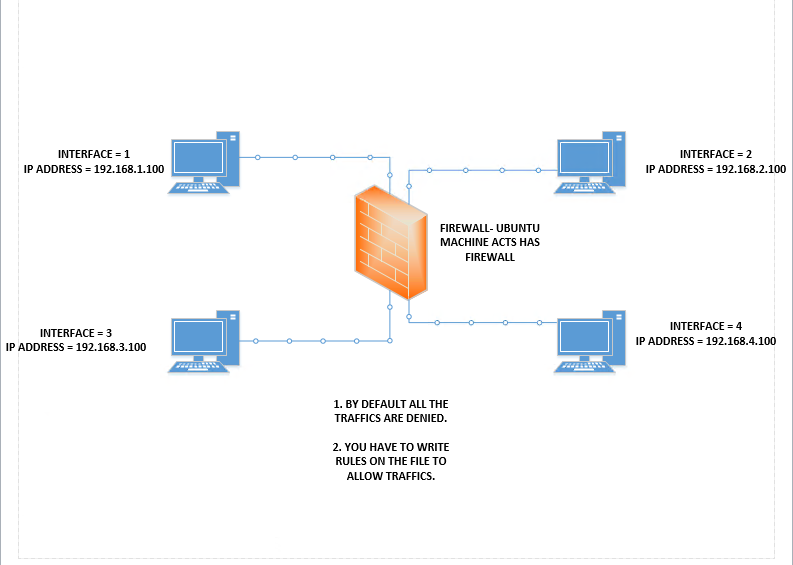
Machines used for testing : UBUNTU 20.10 — THE FIREWALL LISTEING IN INTERFACES
Interface 1 CENTOS CORE — 192.168.1.100 Static Ip Interface 2 CENTOS CORE — 192.168.2.100 Static Ip Interface 3 CENTOS CORE — 192.168.3.100 Static Ip Interface 4 CENTOS CORE — 192.168.4.100 Static Ip
I used UBUNTU 20.10 has my firewall and added 4 interfaces.The 4 interfaces are running on CENT OS LINUX with specified ip addresses.
If i ping from 192.168.1.100 to 192.168.2.100
The 192.168.1.100 sends a packet from interface 1 and the firewall(ubuntu) will unpack the ip header and check for the destination ip address and forward it to the specific Interface. I have disabled the default ip forwarding in my UBUNTU MACHINE using ‘sysctl -w net.all.forwarding = 0’. Furthermore, I tested by blocking the ip address from interface 1 (ip address) to interface 2 (ip address) icmp ping traffic and it successfully Denied.
Concept
- Runing the script is simple, you must have root privelages. Run the
main.pyfile to begin the firewall. - Requirements to run this Firewall.
– Python 3.9.2
— Ubuntu 20.10 Virtual Machine. — Extra Virtual Machines for testing. — Four Interfaces with IP configured.
3. Dependencies.
– pip3 install psutil
— pip3 install csv
— pip3 install threading
— pip3 install logging
— pip3 install datetime
Originally published at https://github.com.


2 comments
This is very helpful Thank you for sharing
My friend shared me this blog. Well Organized! I will be trying this technique with C.