Project Proposal
Abstract
A hotel networking system is a complex communicator which provides the pathway for communication between individual systems within the hotel or for external systems. The implementation of the hotel networking system itself is a challenging task. A solution was required which provided scalability, reliability, controlled access and high bandwidth. Expansion needed to be done easily without the requirement for complex tools or complex skills. An always available network was needed to communicate with minimal downtime and in case of a failure, the system should have the means to dynamically recover itself and provide connectivity using alternate paths in minimum time. Since most of the users will be Wi-Fi oriented and majority would be using it to access the internet, content filtering and secure means were needed to provide a safe and wholesome experience with minimal impact from outside networks. With all these constraints, data needed to be exchanged at a speed and reliable rate to reduce delays and conserve time and money.
With time, the existing system implemented was in need to be upgraded to satisfy user requirements. Due to the increase in employees, different hierarchies were established and the need for an email server was recognized to officially communicate within the hotel organization. The rate of data to be stored on the server increased day by day where storing it in the server itself was no longer practical and degraded the server performance. Therefore, an external Network Attached Storage (NAS) was introduced with ability to support large volumes of storage and RAID configuration for reliability and integration to an open-source file share platform. CCTV footage stored previously on the Network Video Recorder (NVR) device is now integrated to the NAS to provide better capacity and redundancy. The existing firewall was reaching its capacity and needed to be upgraded to a newer firewall. This new firewall is able to provide services such as implementing a proxy server and generating more efficient usage reports and also provide a more structured approach to load balancing the network traffic. The physical security of the infrastructure was improved by the addition of Biometric and RFID enabled door locks which can authenticate only authorized personnel and provide logging information on entry and exits. Network security was also achieved by using the AAA model rather than basic user authentication where the administrator can decide which services and views can be accessed to which user according to the organization’s hierarchy.
Therefore, with reference to the above context, the solution provided is intended to fulfill necessary user requirements and also have the ability to accomplish future requirements without compromising user experience on the network.
Contents
- Introduction
- Analysis
- Network Design
- Technologies
- Forecasted problems and planned solutions
- Conclusion
1.Introduction
In the past a hotel/resort was just a place where people would need as a place to stay. The means of providing accommodation and meals were the main priorities of a hotel. But today the expectations of a customer regarding a hotel have just gone beyond the above mentioned. Many people today consider the availability of modern amenities like Wi-Fi and such. Not only customers but hotel management also benefit massively by modernization. Data sharing, remote management, surveillance and such services are a must in the hotel management area. This is where a properly implemented network comes into play. This network design is aimed at a hotel which provides these modern amenities to customers and makes use of automated technologies to provide services for operational activities. The solution we hope to implement makes use of the up-to-date technologies to provide a reliable, redundant and scalable network solution. One of the main aspects in this network is providing uninterrupted Wi-Fi access to both customers and even hotel staff. Here the separation of groups according to their Wi-Fi credentials is important as to provide varied access levels, bandwidth, lease times and such. This access must also be available throughout the hotel premises.
Because of these modern requirements to the hotel infrastructure, a large amount of data is passed between endpoints. Much of these data are needed to be stored on premise and backed up for safeguarding. The implementation of the NAS helps to be used as a large data storage combining multiple hard drives and also using RAID technologies to keep data redundant and low latency in access. Migration of the CCTV system to a server-based software NVR solution helps overcome limitations such as Disk capacity and lack of centralized management. Internal communication in the hotel premises has passed the age of telephone calls. The need for an efficient, recordable solution was needed controlled in a centralized manner. Introduction of an E-mail server with integration to existing Active Directory means that no much extra steps are needed to set up and use the service. All Emails are stored in an open-source server. The Active directory has been set up as a Disaster Recovery site using Azure Active Directory. This ensures that if the on-premise servers fail or get compromised, the DR site can be put to action and ensure the availability of users and groups. Addition of a proxy server with load balancing integrated using the firewall has the ability to provide users a low latency experience while providing a more granular level of control to the administrator about the network traffic. With the addition of these new devices to the infrastructure, attention was required for mechanisms to safeguard physical access to the devices and logical access to the data within the devices. Introduction of RFID and fingerprint enabled access registration mechanisms coupled with magnetic activated door locks installed at doors to the network room helps address the issue of physical access in addition to the CCTV system. Hardening network devices with AAA concept, filtering traffic using proxy rules and such addresses the issue logical access to data.
Following developments in the implementation to the infrastructure of the hotel networking system are able to solve existing requirements and meet new user expectations
2.Analysis
Analysis of the hotel networking system
The hotel networking system is a complex structure with many requirements to be fulfilled. Upon inspection and analysis, we have identified the following characteristics of a modern hotel networking system
- Most of the reservations are done online rather than physically being present at the hotel desk and since this is the go-to method for foreign customers, the Web server and its attributes must be always available.
- Due to the large spacious structure of a hotel, the devices are scattered in remote locations and appropriate wiring structure must be planned
- Constraints with regard to external interferences such as Electromagnetic interference and Radio frequency interference since there is a high density of light bulbs, electrical wiring, etc. running throughout the building.
- Majority of the users are to be connected using wireless means such as Wi-Fi, therefore access points have to be placed in substantial amounts and it must be strategically placed to eliminate dead zones and ensure complete end-to-end connectivity.
- Placement of Access points in outdoors due to amenities like outdoor pool and recreational areas and its resistance against natural elements.
- A considerable amount of network traffic will be destined towards the internet, therefore necessary means have to be implemented to ensure a safe, fast and reliable access for all users.
- There is a large number of users who are to be supplied and the users exist in different hierarchical levels, therefore all of the users must be satisfied without compromising user experience.
Identified Solutions
With regard to the aforementioned analysis on the hotel networking system, following are some solutions we have implemented.
- The internal wiring for the access points and desktop machines will be done inside conduits and wall trunking casings which provides protection from fires and also the majority of the wires used are Cat6 type which offer significantly lower levels of interference and near-end crosstalk with compared to cables types such as Cat5 or Cat5e.
- In order to select strategic positions for access point placement, we employed the services of the simulation software Cisco RF planner. This software had the ability to dynamically simulate effective area of an access point, areas of intersection of signals, areas of dead zones, etc. depending on the model and frequency of the access point over our floor plans.
- Due to the placement of underground cabling, we have used special non-corrosive metal GI pipes to insulate the wires underground against natural elements. These underground cabling is used to provide connectivity to adjoining building and outdoor access points.
- A Firewall of large capacity is implemented since majority users access the internet and that makes the whole network vulnerable to external attacks.
- Implementations of different domains to users, where their activities are controlled and internet bandwidth is distributed according to the hierarchy, where essential users and services are prioritized and all the users are satisfied while conserving bandwidth.
3. Network Design
Floor plans and diagrams
Topology diagram
Following is the topology diagram used for this implementation. Here we have used the Cisco three tier architecture. It provides many advantages such as scalability and resiliency. Since this network does not have the requirement for external LANs interconnecting to the core via distribution layer switches, the collapsed core variant of the Cisco three tier architecture is used. The collapsed core takes the functions of both the distribution and core layers, but the features like scalability, redundancy, etc. are not compromised.
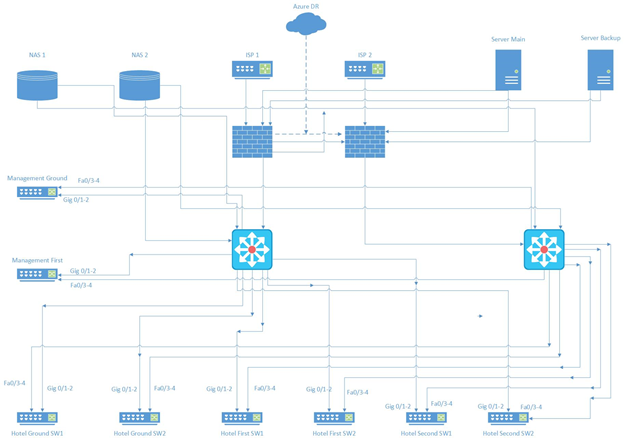
Devices diagram
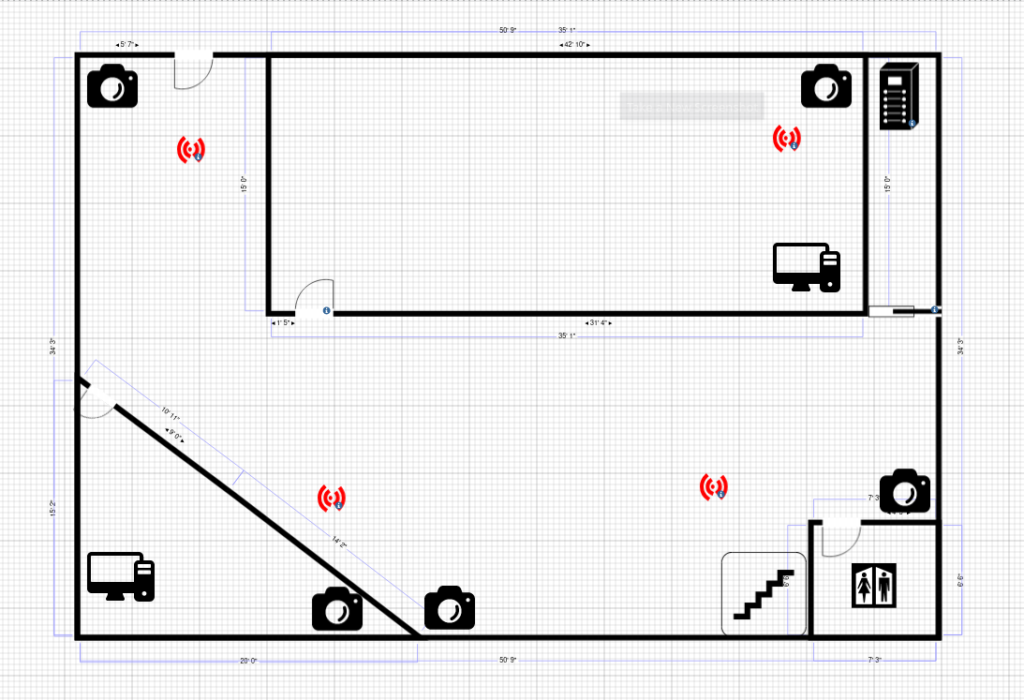
Ground Floor
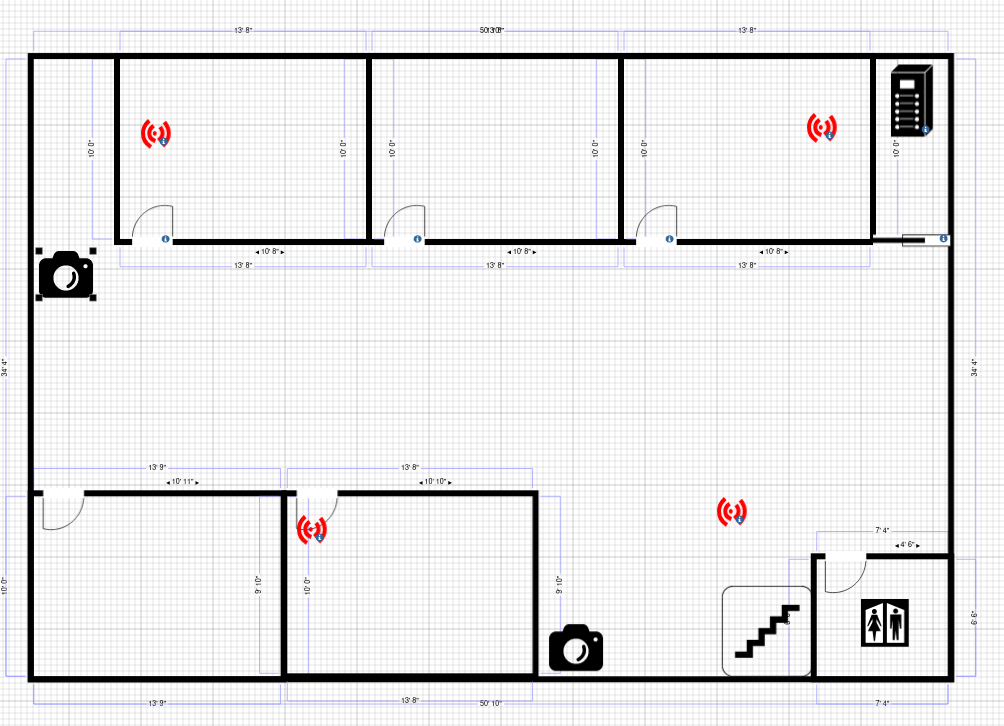
Floor 1
Floor 2
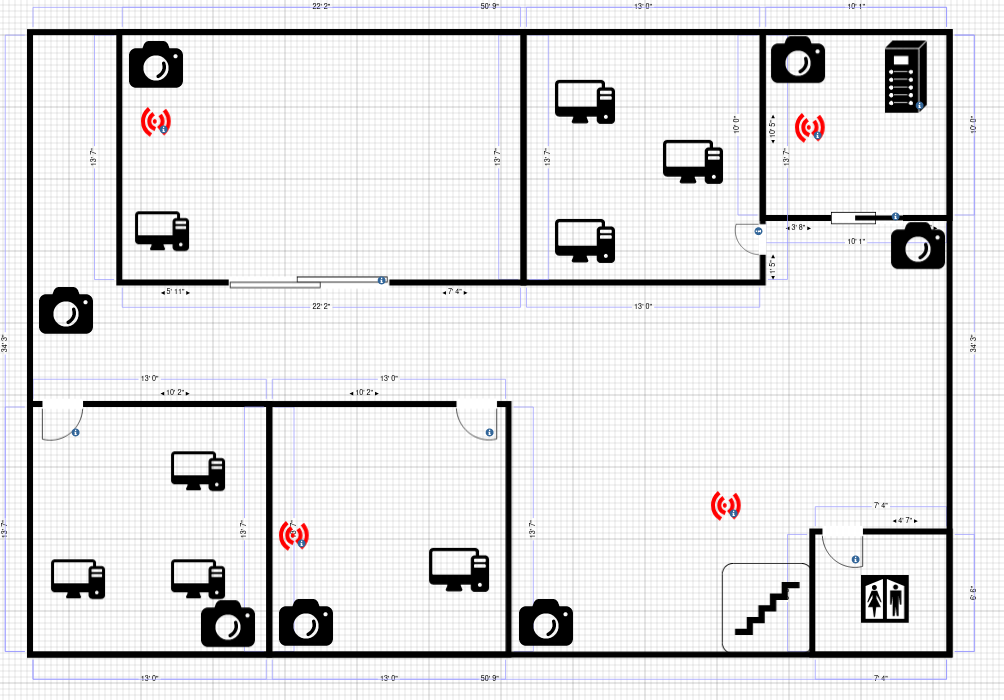
Access point diagram
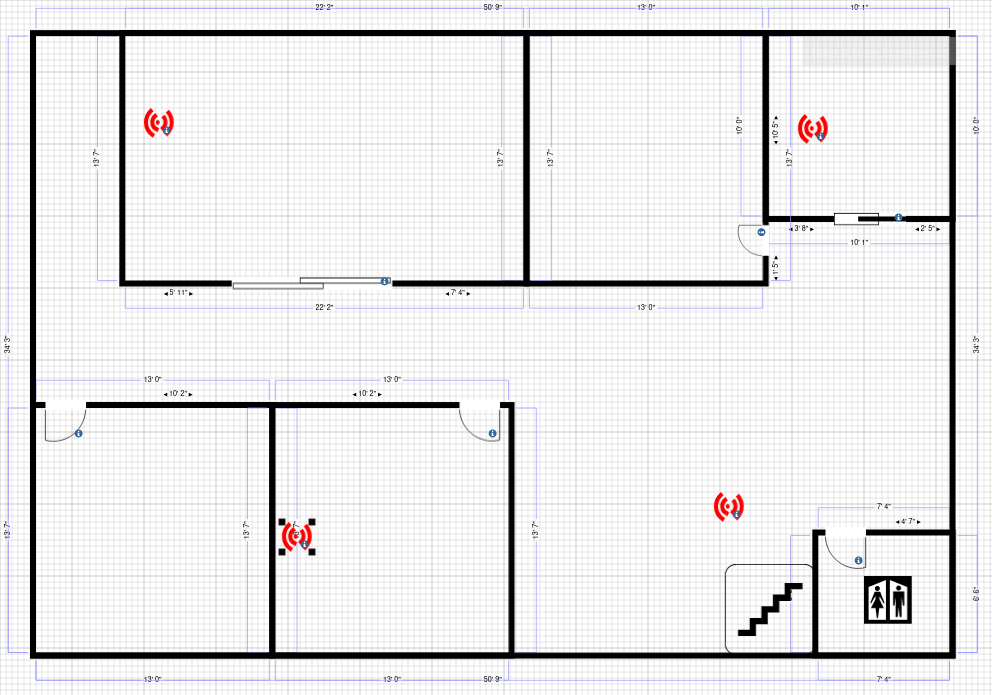
The placement of Access points was done strategically with the aid of the Cisco RF planner software.
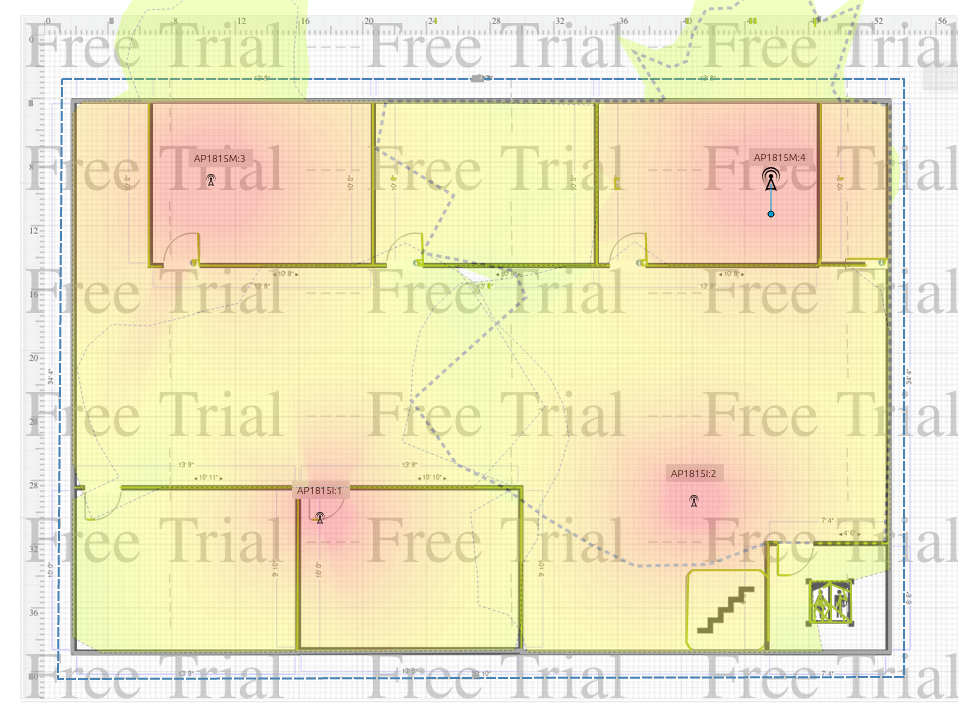
Ground floor
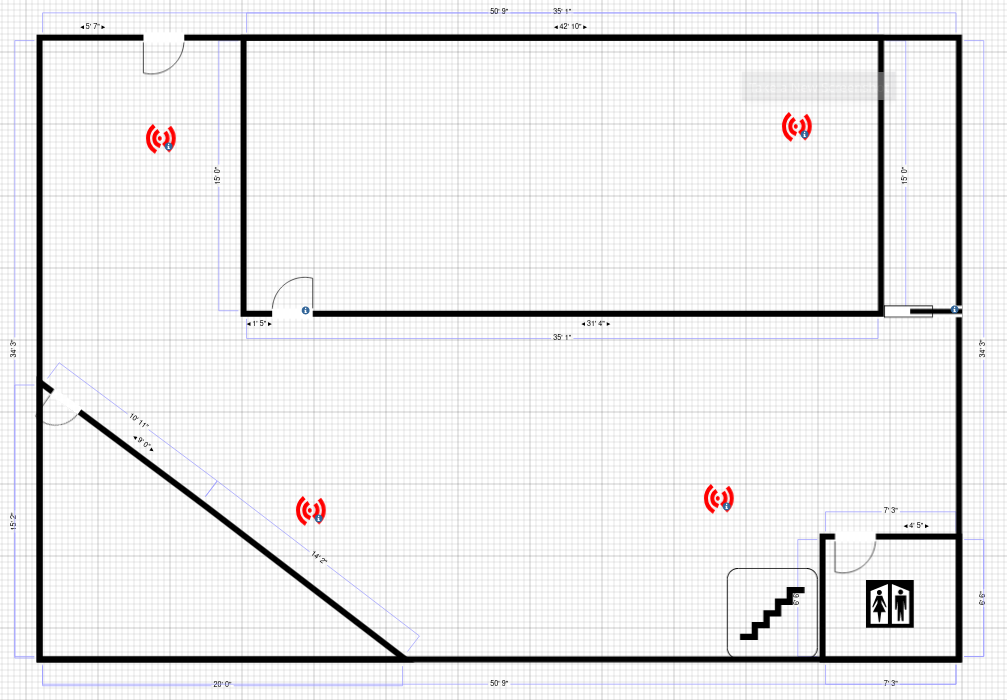
Floor 1
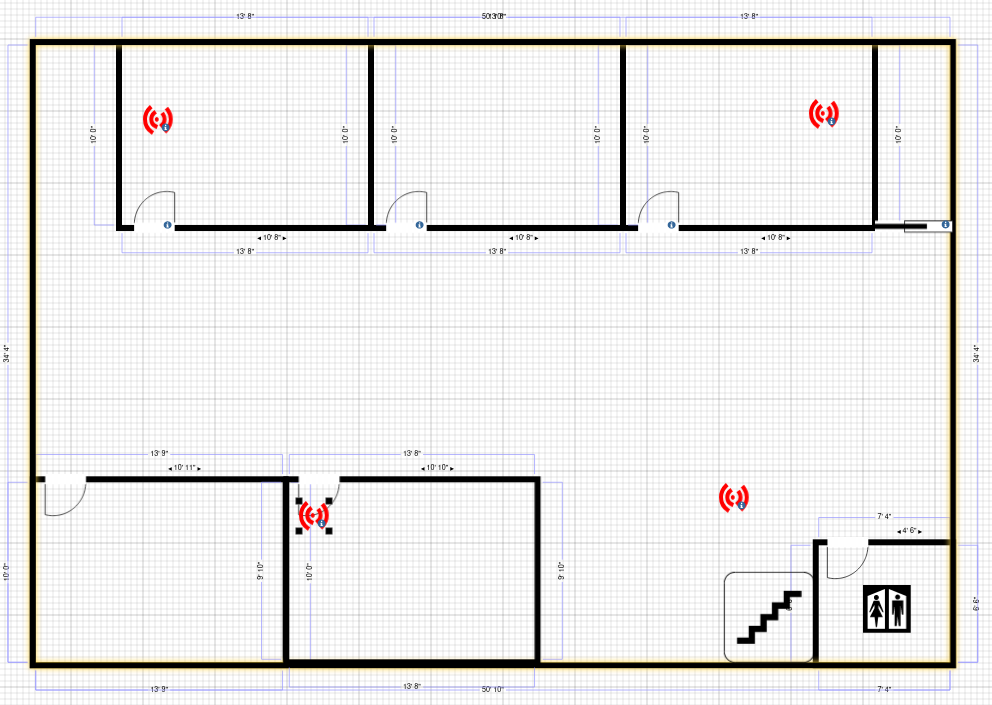
Floor 2
Server Rack Diagram
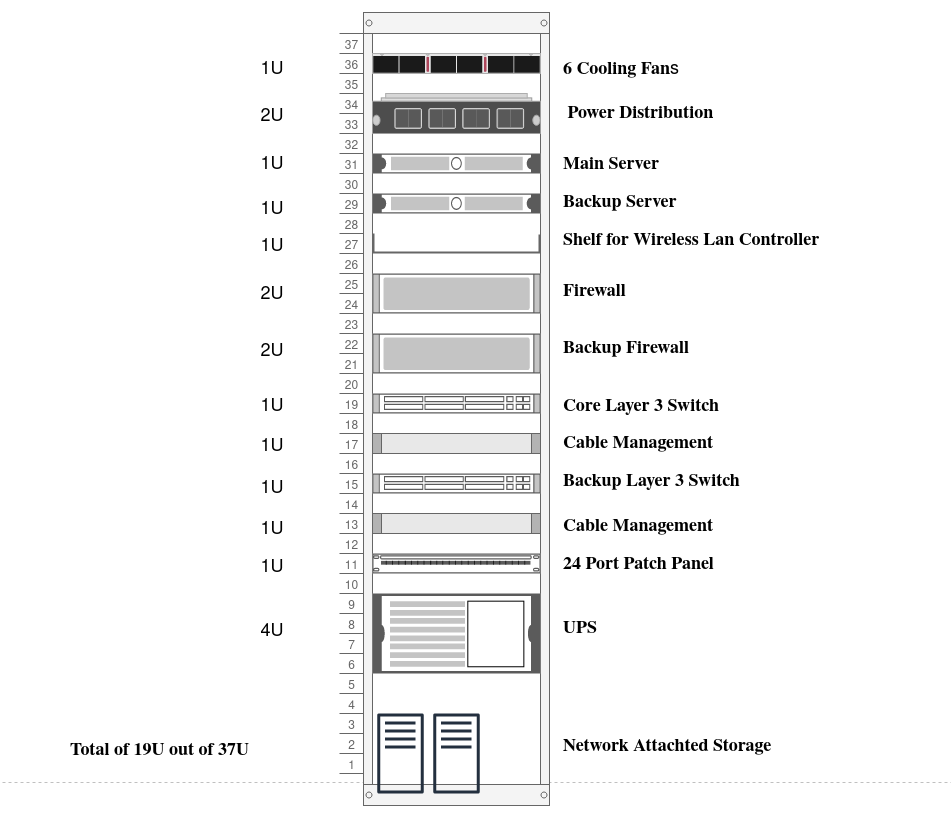
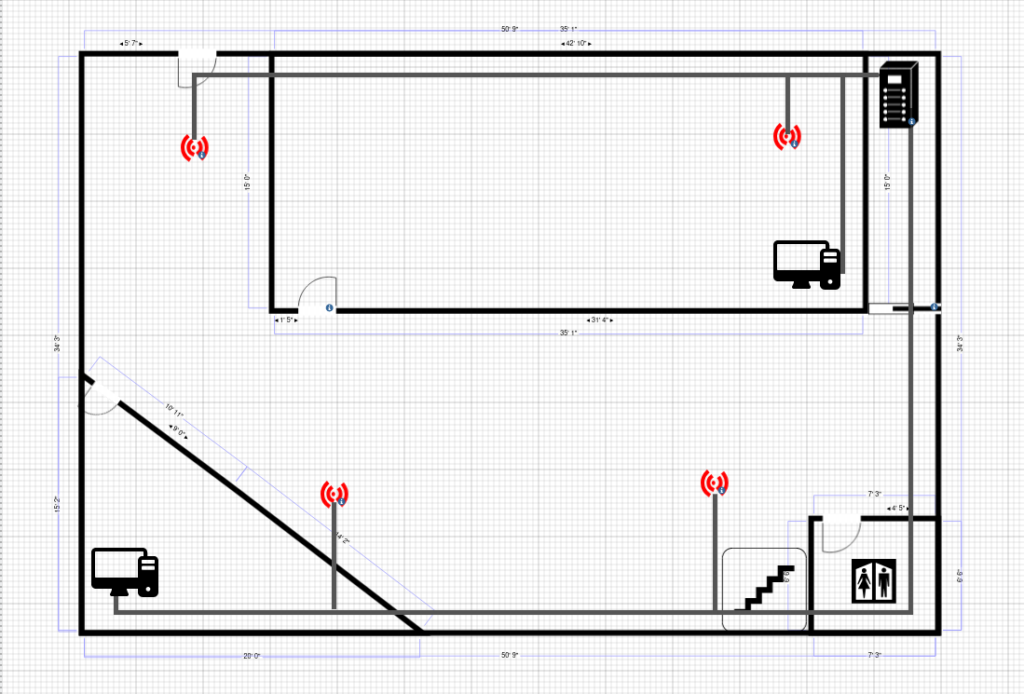
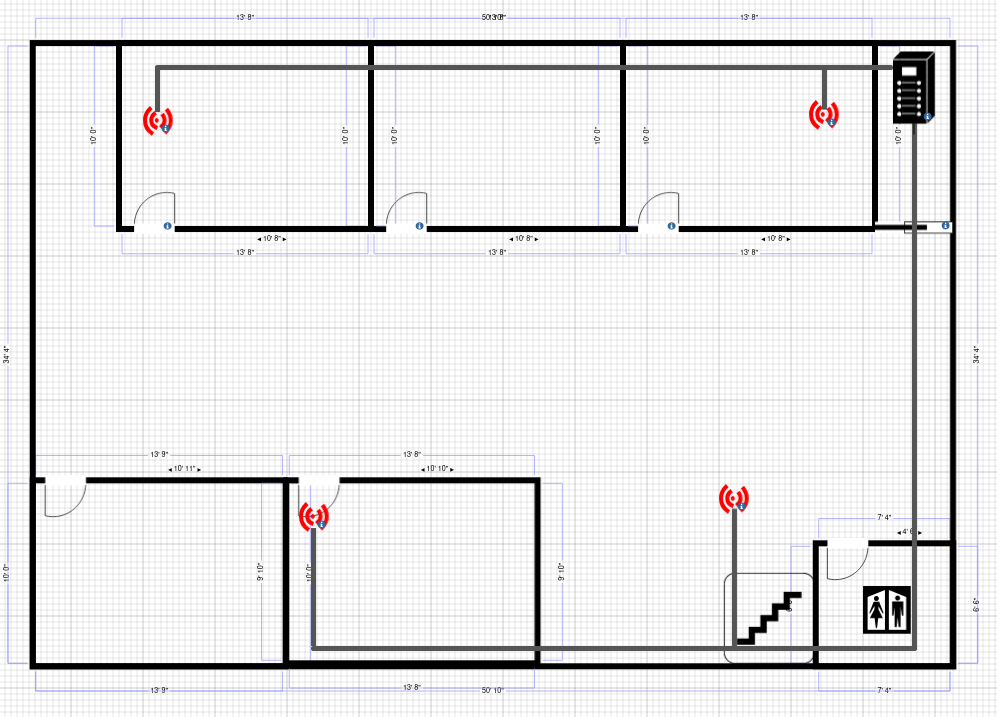
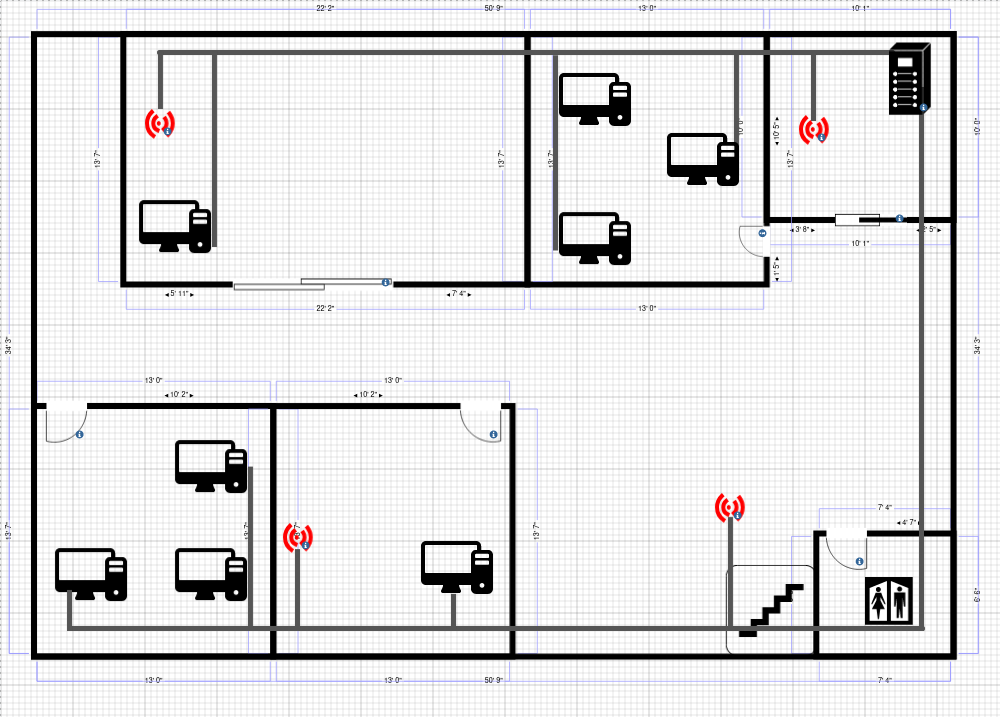
Network Cabling Diagram
Ground Floor
Floor 1
Floor 2
Virtualization Diagram
While generating considerable cost savings, virtualization can boost IT agility, flexibility, and scalability. Benefits of virtualization include higher workload mobility, improved resource performance and availability, automated processes, and easier management and lower ownership and operating costs for IT.
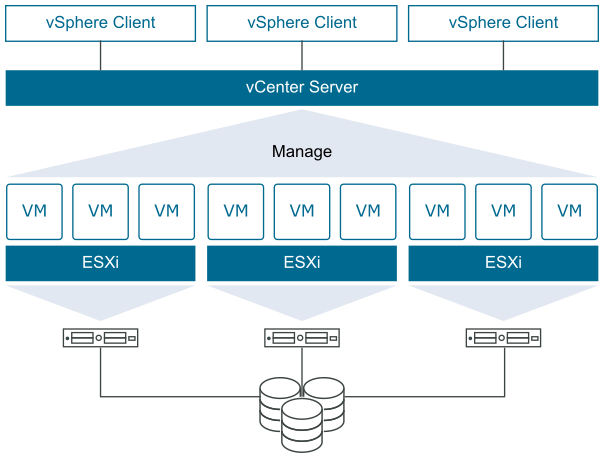
4.3.1 Pre-Requisites
• The Time must be sync in all ESXi Hosts.
• ESXI host 6.5 or later, or on a vCenter Server instance 7.0 or later.
• Client machine, ESXI host, the vCenter appliance use the same DNS server.
• FQDN for vCenter and it is reachable from the client machine which is used to deploy.
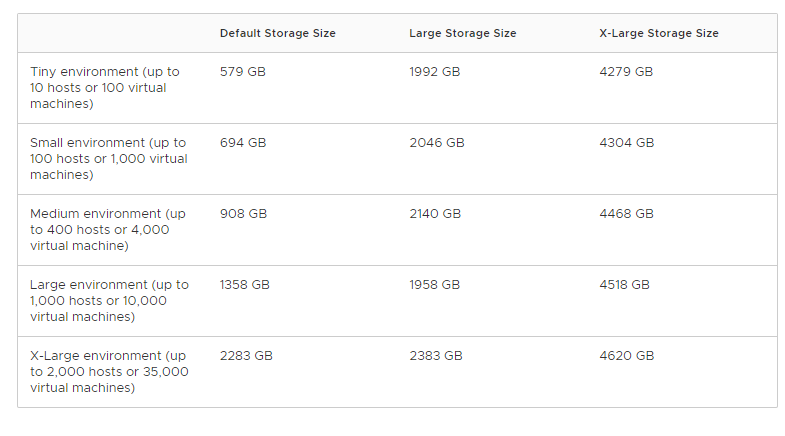
Storage Requirements for a vCenter Server Appliance
4.3.2 VMware ESXi 7.0
An enterprise-class, type-1 hypervisor called VMware ESXi was created by the company to deploy and run virtual machines. As a type-1 hypervisor, ESXi incorporates and includes essential OS elements like a kernel rather than being an installed software program on an operating system.
ESXI 1
ESXI 2
ESXI 3
4.3.3 VMware vCenter vSphere 7.0
The virtualization platform for VMware’s cloud computing is called vSphere. It contains the ability for vMotion to transfer several virtual machines at once from one host server to another, as well as enhanced versions of vCenter Configuration Manager and vCenter Application Discovery Manager.
We installed the vCenter and point server FQDN name to vcenter.ark.lk.
vCenter Client
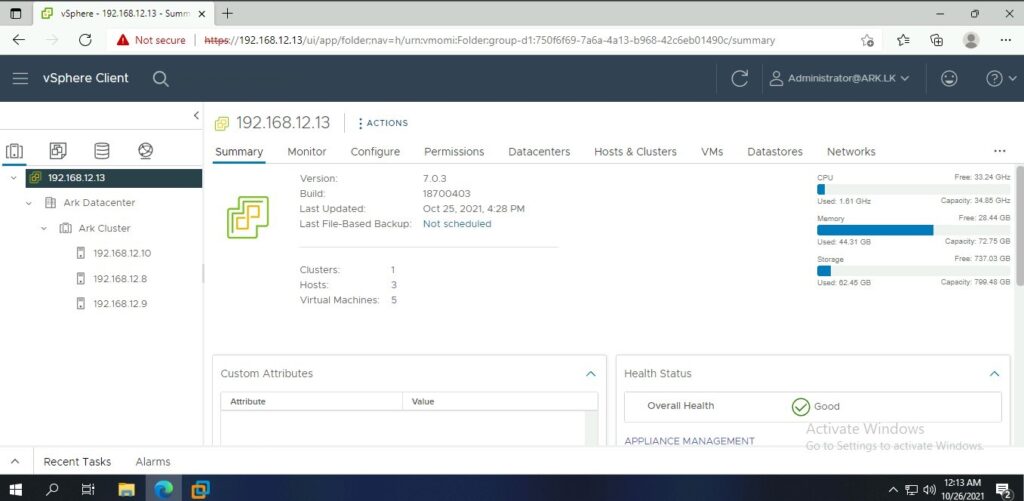
Ark Datacenter
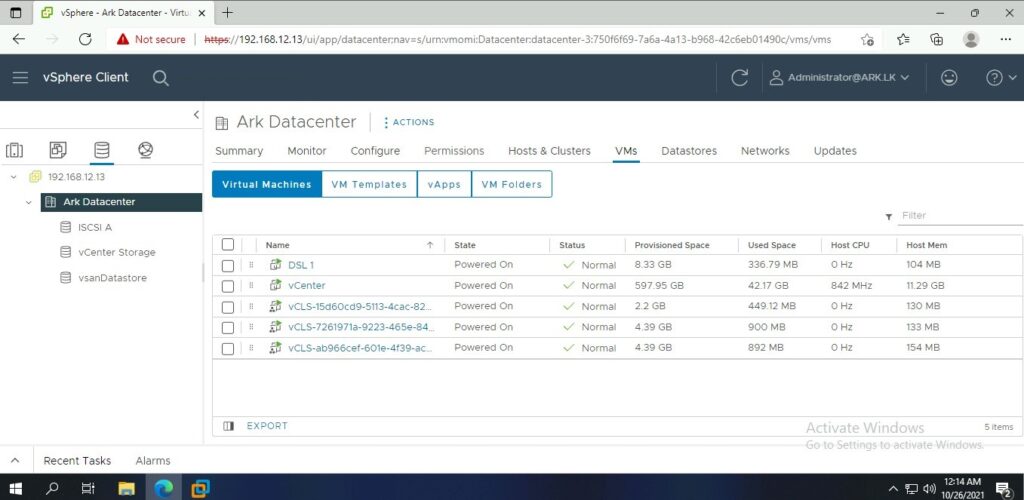
Ark Management Switch
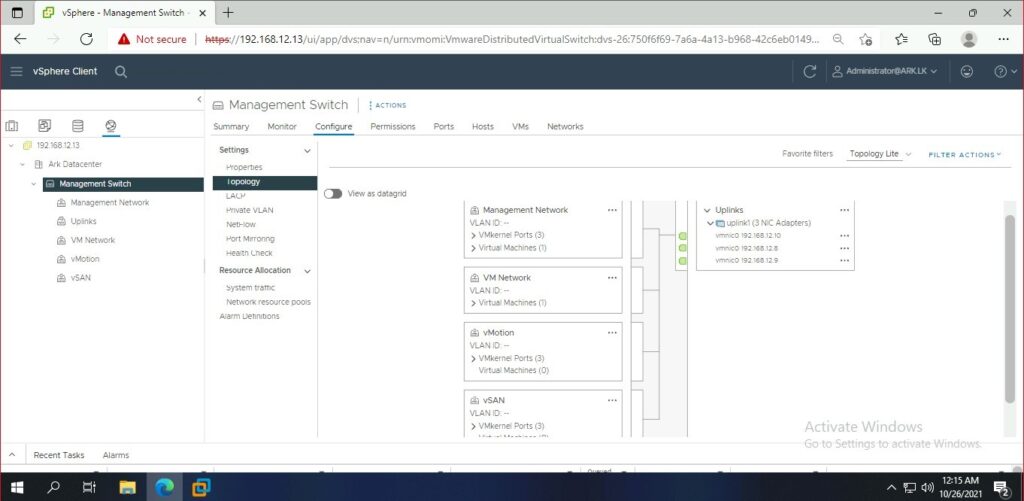
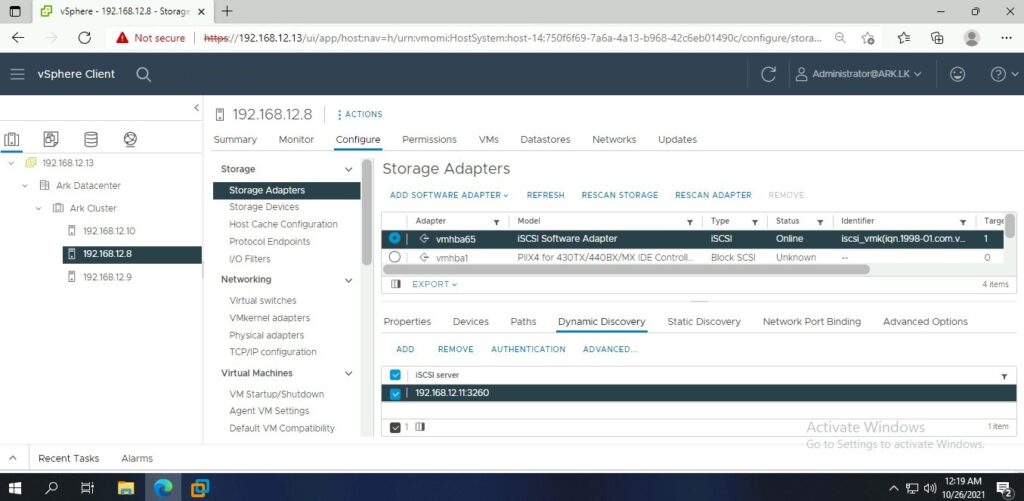
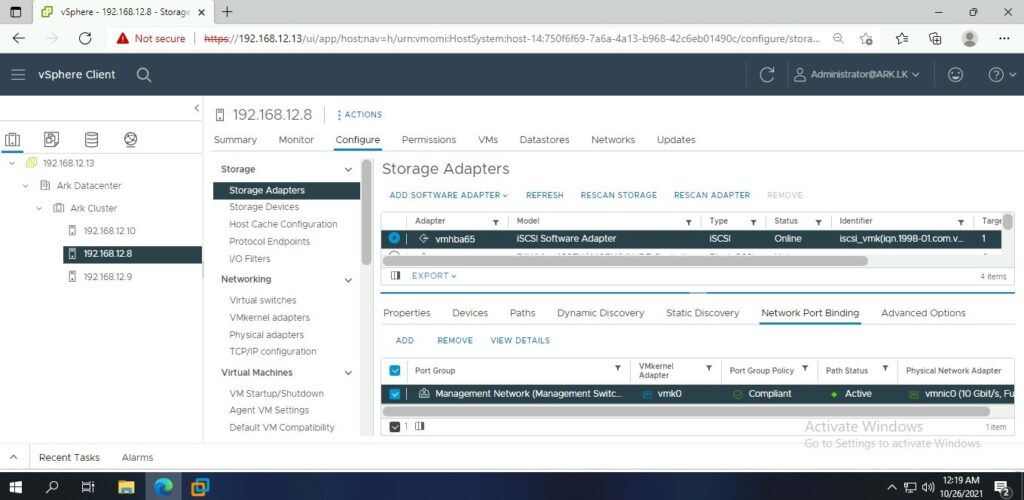
Ark ESXI 2 Storage Adapters
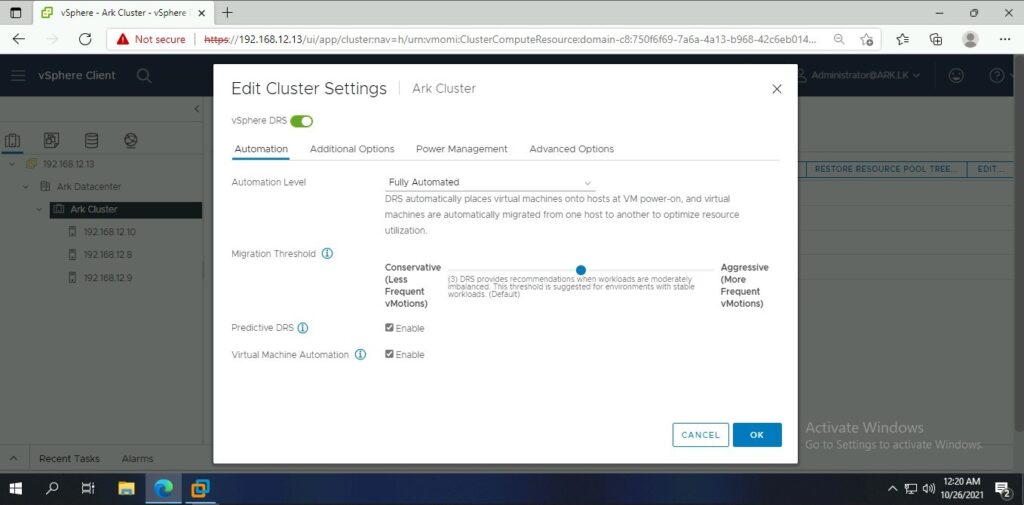
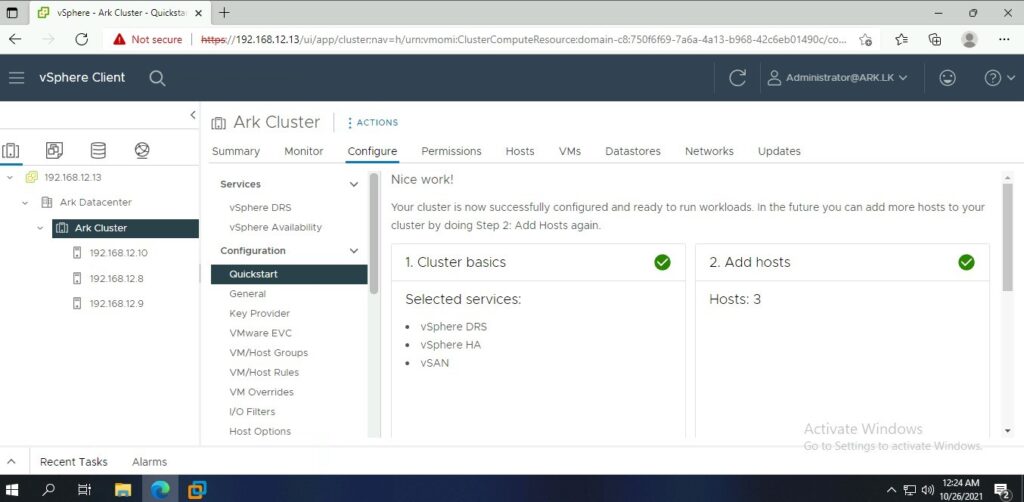
Ark Cluster Settings
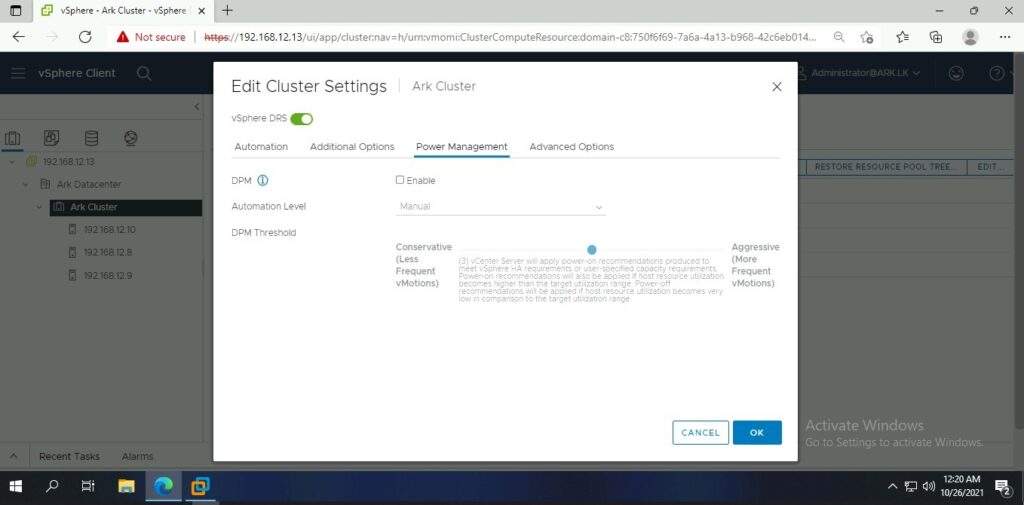
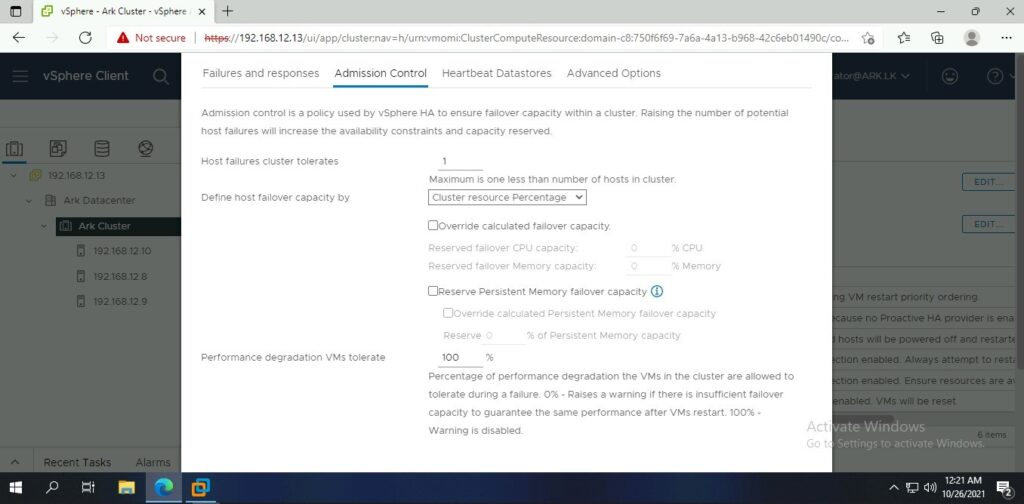
Ark Configuration
Ark Datastores
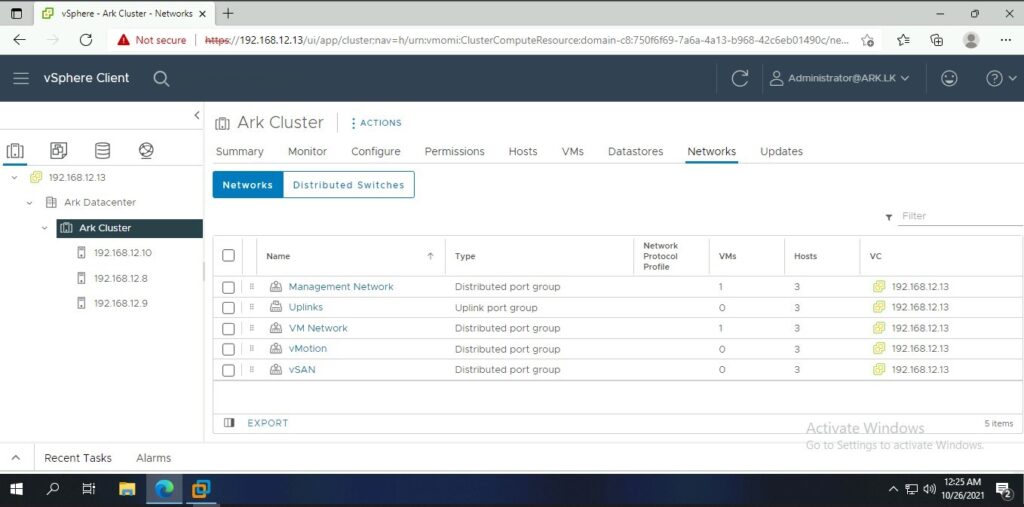
Ark Network
Ark VMs
vCenter Licenses
vSAN Clusters
vSphere Home
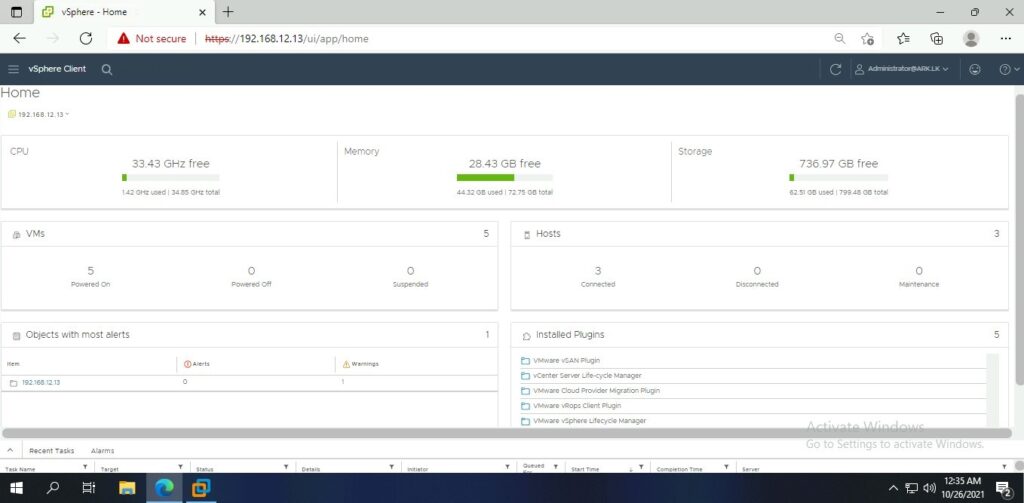
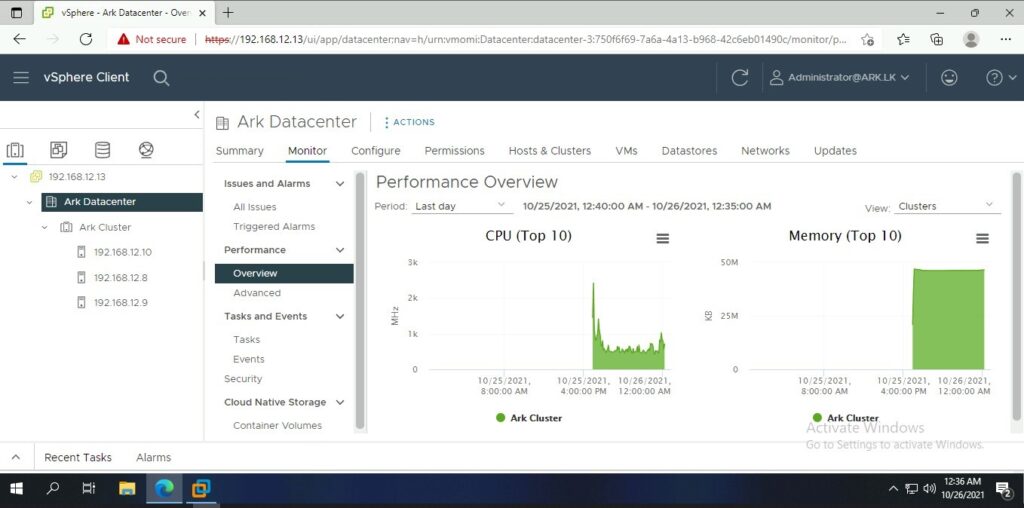
Ark Datacenter Performances
vSphere vMotion
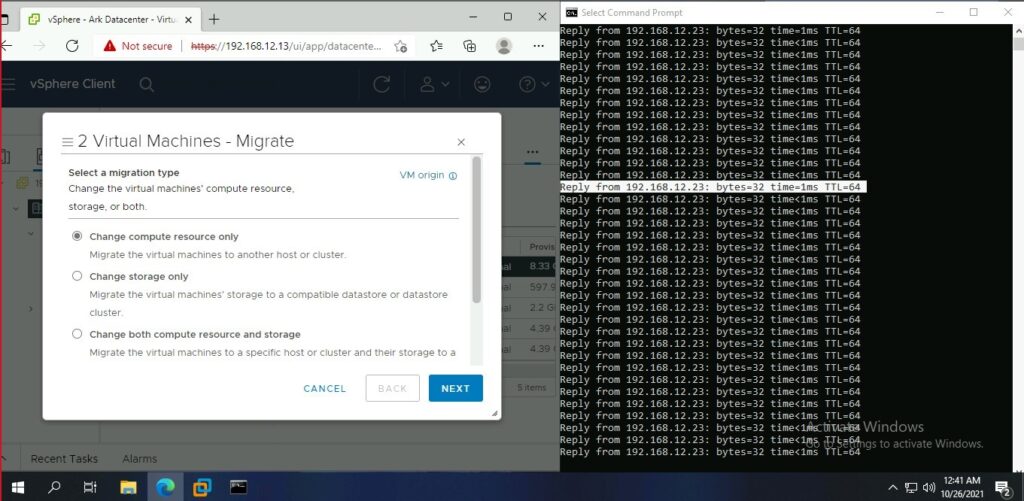
Migrating while a continuous ping.
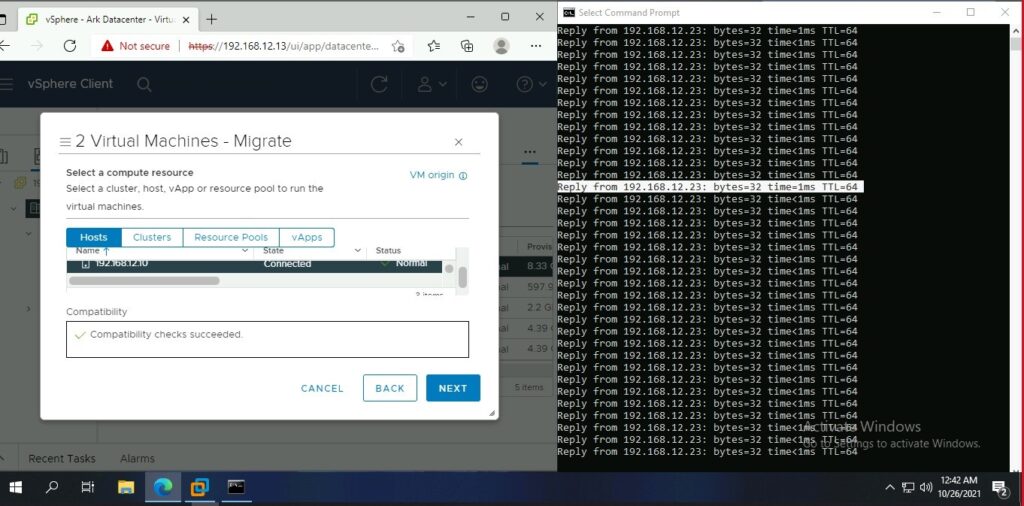
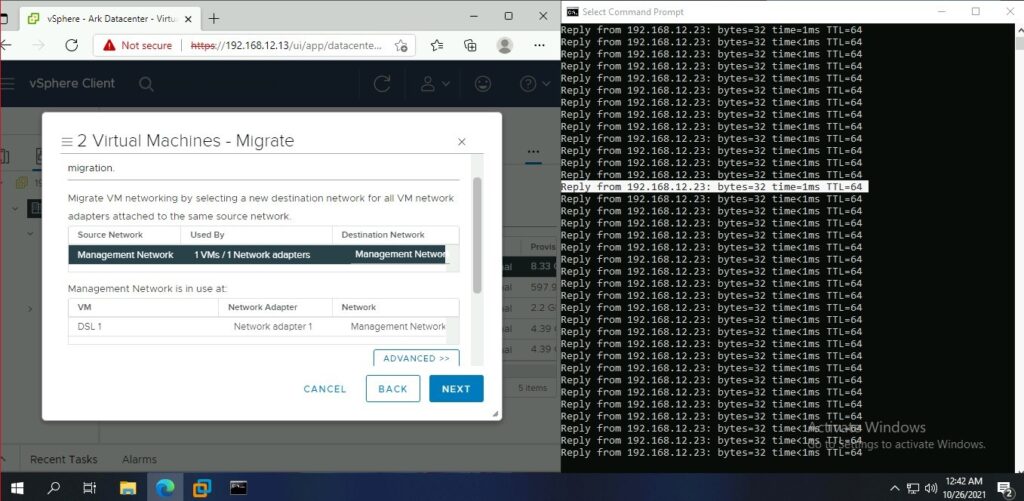
Backup Configuration
A quick, inexpensive, high-performance backup and replication solution is Altaro Backup. We eliminated waste and effort to provide you with an agile, streamlined solution that is simple to use, packed with features, and comes with exceptional 24/7 support as standard. efficient backup configuration. complete command over your backups.
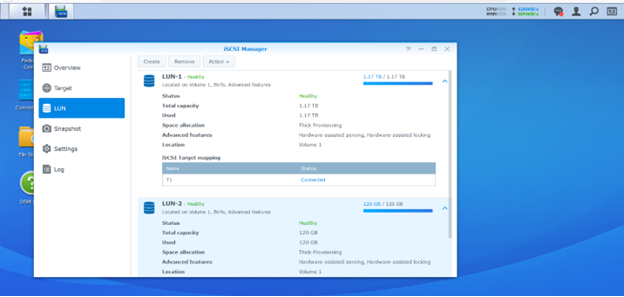
4.7 NAS Configuration
The file-level storage architecture known as network-attached storage (NAS) increases the accessibility of stored data to networked devices. Along with storage area networks (SAN) and direct-attached storage, NAS is one of the three basic storage topologies (DAS).
Raid 5 strikes a solid balance between performance and redundancy. With a minimum of three drives required, a single drive is locked away for holding all the necessary data to rebuild a storage medium in the case of a failure.
Protocol Usage
In this Implementation multiple protocols have been used. In addition to mandatory protocols like IP, TCP, HTTP, etc.; Following are the protocols used and their application in our implementation
| Protocol | Application |
| Spanning Tree Protocol (STP) | Prevent loops between main and backup L3 switches and also between the L3 and L2 switches. Since redundant loops are planned on this network, STP deals with remediation of network changes or failures |
| Protocol Aggregation Protocol(PAgP) | Creation of EtherChannel’s. This creates bundled ports on the network which is used as a redundant measure and also to increase bandwidth and load balance between the ether channeled cables |
| Hot Standby Router Protocol (HSRP) | Achieve redundancy between core switches. This is a Cisco proprietary protocol which is applied to each VLAN and also between the aggregated link from the core switches to the server |
| VLAN Trunking Protocol (VTP) | Share information regarding the VLANs created in the main L3 switch. The core L3 switches are configured as VTP servers and the L2 switches as VTP clients. The VTP information is entered in the main L3 switch |
| Network Time Protocol (NTP) | Time synchronization between core switches and access switches. This prevents the need to manually configure time and date on L2 switches. It saves time and also adds a layer of security for when logs are recorded regarding activity of the networking devices. |
| Simple Network Management Protocol (SNMP) | Monitoring of the network. The information obtained by the SNMP protocol is sent to a host containing client monitoring software. A common monitored sensor which was also used in this implementation was the SNMP system uptime sensor |
| NetFlow | NetFlow is a feature that was introduced on Cisco routers around 1996 that provides the ability to collect IP network traffic as it enters or exits an interface. By analyzing the data provided by NetFlow, a network administrator can determine things such as the source and destination of traffic, class of service, and the causes of congestion. |
| Internet Small Computer Systems Interface (ISCSI) | The SNIA dictionary defines Internet Small Computer Systems Interface (iSCSI) as a transport protocol that provides for the SCSI protocol to be carried over a TCP-based IP network, standardized by the Internet Engineering Task Force and described in RFC 3720. |
| Hyper Text Transfer Protocol Secure (HTTPs) | Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). It is used for secure communication over a computer network, and is widely used on the Internet. In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL). The protocol is therefore also referred to as HTTP over TLS, or HTTP over SSL. |
| Secure Shell and Transport Layer Security (SSH/TLS) | Secure Shell (SSH) is a cryptographic network protocol for operating network services securely over an unsecured network. Typical applications include remote command-line, login, and remote command execution, but any network service can be secured with SSH. Transport Layer Security (TLS), the successor of the now-deprecated Secure Sockets Layer (SSL), is a cryptographic protocol designed to provide communications security over a computer network. Several versions of the protocol are widely used in applications such as email, instant messaging, and voice over IP, but its use as the Security layer in HTTPS remains the most publicly visible. |
Bandwidth Allocation
- Departments – 80Mbps x 5
- Operational Devices – 50Mbps
- Directors and chairman – 65Mbps
- Camera and DVR – 10Mbps
- Guest Wi-Fi – 330Mbps
- Staff Wi-Fi – 100Mbps
Total Proposed Internet Bandwidth – 800Mbps (Primary Line)
200Mbps (Backup Line)
The traffic is to be load balanced among the primary and backup Internet Service Providers
Services in implementation
The following services and roles are implemented on this project. The majority of the services mentioned here are mandatory and reduces the manual configurations on the users
- ADDS
Provides centralized management of clients on the LAN to the network administrator. This includes creating users, adding users to groups and such. Necessary group policies and restrictions limit the actions of users in the domain which adds a layer of security and ensures that all users remain within their privileged levels. This hotel network has multiple groups of users with different user privileges within the LAN. Outside users like guests are also connected to the hotel network for activities like internet surfing. Therefore, the firewall is also integrated with the firewall which can provide restrictions and generate reports on different user activity
- DNS
Registration of users to the domain and also providing hostname resolvement for clients for web browsing is provided by the DNS service located within the server.
- DHCP
Since there a large no of devices in this network LAN and the probability where all of them are powered on is not high, IP addressing information, DNS information and default gateway is provided to the clients by the means of a DHCP service located within the user. This service is very important for the IP leasing of wirelessly connected devices since they have on-off nature of network activity and therefore assignment of static IPs is not feasible and can cost valuable time.
- WDS
The LAN has up to 65 PCs which are interconnected to the network, therefore during the initial startup, manually installing an operating system is quite time and labour intensive. Further downloading and updating of operating system software per device can cost the limited bandwidth in the network. WDS provides the means to distribute a common copy of operating system files or update packages to device in the LAN and even an external device upon permission of the Administrator
- AAA
AAA is implemented in this network to manage access control to networking system. A Windows based RADIUS server is implemented using the NPAS service in the main server. It is mainly used to authenticate wireless users who connect to the network on 802.1X technology and necessary EAP type for policy authentication using the various access points located within the premises. Furthermore, a wireless controller is implemented to manage and provide uninterrupted Wi-Fi access throughout the building domain. The authorization on the possible activities and privileges allowed for users and the accounting of the users connected wirelessly is done since the RADIUS server is connected to the Active Directory and accepts a user within the directory.
- Server Message Block (SMB)
The Server Message Block (SMB) is a network protocol that enables users to communicate with remote computers and servers — to use their resources or share, open, and edit files. It’s also referred to as the server/client protocol, as the server has a resource that it can share with the client.
Like any network file sharing protocol, SMB needs network ports to communicate with other systems. Originally, it used port 139 that allowed computers to communicate on the same network. But since Windows 2000, SMB uses port 445 and the TCP network protocol to “talk” to other computers over the internet.
- Proxy Server
A proxy server provides a gateway between users and the internet. It is a server, referred to as an âintermediary because it goes between end-users and the web pages they visit online.
When a computer connects to the internet, it uses an IP address. This is similar to your homes street address, telling incoming data where to go and marking outgoing data with a return address for other devices to authenticate. A proxy server is essentially a computer on the internet that has an IP address of its own.
- Mail Server
A mail server is the computerized equivalent of your friendly neighborhood mailman. Every email that is sent passes through a series of mail servers along its way to its intended recipient. Although it may seem like a message is sent instantly – zipping from one PC to another in the blink of an eye – the reality is that a complex series of transfers takes place. Without this series of mail servers, you would only be able to send emails to people whose email address domains matched your own – i.e., you could only send messages from one example.com account to another example.com account.
- Web Server
A web server is a computer that runs websites. It’s a computer program that distributes web pages as they are requisitioned. The basic objective of the web server is to store, process and deliver web pages to the users. This intercommunication is done using Hypertext Transfer Protocol (HTTP). These web pages are mostly static content that includes HTML documents, images, style sheets, test etc. Apart from HTTP, a web server also supports SMTP (Simple Mail transfer Protocol) and FTP (File Transfer Protocol) protocol for emailing and for file transfer and storage.
4. Technologies
VMWare vSphere Environment
- VMWare vSphere ESXI
VMware ESXi (formerly ESX) is an enterprise-class, type-1 hypervisor developed by VMware for deploying and serving virtual computers. As a type-1 hypervisor, ESXi is not a software application that is installed on an operating system (OS); instead, it includes and integrates vital OS components, such as a kernel.
After version 4.1 (released in 2010), VMware renamed ESX to ESXi. ESXi replaces Service Console (a rudimentary operating system) with a more closely integrated OS. ESX/ESXi is the primary component in the VMware Infrastructure software suite.
The name ESX originated as an abbreviation of Elastic Sky X. In September 2004, the replacement for ESX was internally called VMvisor, but later changed to ESXi (as the “i” in ESXi stood for “integrated”).
- VMWare vSphere vCenter
vCenter Server is the centralized management utility for VMware, and is used to manage virtual machines, multiple ESXi hosts, and all dependent components from a single centralized location.VMware vMotion and svMotion require the use of vCenter and ESXi hosts.
- vMotion (Live Migration)
Live migration (vMotion) in ESX allows a virtual machine to move between two different hosts. Live storage migration (Storage vMotion) enables live migration of virtual disks on the fly. During vMotion Live Migration (vLM) of the (RAM) memory of the VM is sent from the running VM to the new VM (the instance on another host that will become the running VM after the vLM). The content of memory is by its nature changing all the time. ESX uses a system where the content is sent to the other VM and then it will check what data is changed and send that, each time smaller blocks. At the last moment it will very briefly ‘freeze’ the existing VM, transfer the last changes in the RAM content and then start the new VM. The intended effect of this process is to minimize the time during which the VM is suspended; in a best case this will be the time of the final transfer plus the time required to start the new VM
- svMotion (Storage vMotion)
svMotion enables live migration of virtual disks and their home directories without any downtime. svMotion uses a mirror driver to copy virtual hard drives and/or the home directory from the source to destination datastores simultaneously, which keeps everything in sync until the svMotion operation is complete on the destination, at which point the source data is deleted. There is a performance impact from running svMotion â read IO from the source and write IO on the destination. This can be verified through esxtop.[6] If VAAI is enabled on the ESXi hosts and on the storage array, it will offload the svMotion migration operation to the array instead of going through the VMkernel, which increases the migration speed.
- VMWare vSAN
A virtual storage area network (virtual SAN, VSAN or vSAN) is a logical representation of a physical storage area network (SAN). A VSAN abstracts the storage-related operations from the physical storage layer, and provides shared storage access to the applications and virtual machines by combining the servers’ local storage over a network into a single or multiple storage pools. The use of VSANs allows the isolation of traffic within specific portions of the network. If a problem occurs in one VSAN, that problem can be handled with a minimum of disruption to the rest of the network. VSANs can also be configured separately and independently.
- VMWare vSphere DRS
VMware vSphere Distributed Resource Scheduler (DRS) is the resource scheduling and load balancing solution for vSphere. DRS works on a cluster of ESXi hosts and provides resource management capabilities like load balancing and virtual machine (VM) placement.
- VMWare vSphere DPM
VMware Distributed Power Management (DPM) is a pioneering new feature of VMware DRS that continuously monitors resource requirements in a VMware DRS cluster. When resource requirements of the cluster decrease during periods of low usage, VMware DPM consolidates workloads to reduce power consumption by the cluster.
5.Forecasted problems and solutions
When we are implementing our network design we have predicted some problems that we have to face in future. So we have decided to discover that problems and avoid them by giving solutions for that problems.
- Problem
How we adapt to forthcoming new technologies. Now days we have sufficient bandwidth for our local network. But when forecasting for ten years how we fulfill that?
- Solution
Since the wiring plan is a base requirement in the networking system and hotel building we cannot change its structure as it is required. So to provide solution for that problem we have decided to implement ether-channeled Cat 6e cables for local network in the hotel. So we don’t want to incur another cost to implement new wiring plans to get higher bandwidth and for hotel network plan.
- Problem
In future, when we implementing CCTV cameras sometimes, we have to face difficulties in getting power supply for the CCTV cameras. So how we avoid that?
- Solution
For that problem we have used a switch that supports Power on Ethernet (PoE) facility. So for that we have reserved some ports to avoid that problem. By using that we don’t have to give additional power externally. We can just supply Power over Ethernet cable and that will be a better solution for our problem.
- Problem
In period of ten years’ hotel business, operations can be expanded. That means requirement for workers, managers will increase. So we have to place new PC’s, and provide access to new users in management. How we fulfill it?
- Solution
To avoid these problems, we have selected switches which have extra ports. So we can manage additional workers. But if more employees recruited for the hotel and don’t have enough ports to provide access to the local network. To prevent from these problems, we have used modular switches.
6.Conclusion
After implementing the whole project, this project is quite bit costly but this project will help to do current communication, data transfer and day-today activities in easier way. Employees will be provided by both local and internet access from the hotel network and guests, customers will be provided by internet facility via Wi-Fi access. In the hotel premises places like car park, pool area also covered by WI-FI coverage. All the guests will be provided free WI-FI and Priority guests will be prioritized based on their priority and provides some higher bandwidth compared to normal guests. For security purposes and Server room will be well secured and to provide better security for the hotel building. Whole over the hotel premises we have planted CCTV camera to get better protection and for increase physical security. For network security we have selected Firewall.
The selection of devices for networking were foreseen and meticulously selected giving factors like reliability, high performance, security and after-sales services a high significance over the cost factor. The ISP and the technology for the leased line has been selected depending on factors like high bandwidth, always on, reliability, access technology depending on the location and twenty-four-hour assistance services.