As technology continues to advance, so do the threats to our online security. From cyberattacks to data breaches, it’s more important than ever to protect our digital assets. That’s where Digital Guardian comes in. In this blog, we’ll take a closer look at what Digital Guardian is, how it works, and why it’s an essential tool for anyone concerned about their digital security.
Table of Content
- What is Digital Guardian
- Technical Overivew
- Sales Benefits
- Features
- Dashboard
- Overview Configuration
- Conclusion
What is Digital Guardian?
Digital Guardian is a cybersecurity solution designed to protect against advanced threats to data and systems. The platform provides a comprehensive defense against data theft, unauthorized access, and other malicious activities. It uses a combination of next-gen endpoint protection, network visibility, and machine learning to provide real-time threat detection and response.
Technical Overview
Digital Guardian is designed to integrate with your existing security infrastructure and provide advanced protection at the endpoint. The platform uses a combination of signature-based and behavior-based analysis to detect and prevent threats in real-time. This approach allows Digital Guardian to protect against both known and unknown threats, keeping your systems and data secure.
In addition to endpoint protection, Digital Guardian also provides network visibility and control. This allows you to monitor and manage network activity, ensuring that only authorized users and devices have access to sensitive information. The platform integrates with your existing security tools and provides a centralized view of all network activity, giving you complete visibility and control over your security posture.
Sales Benefits
Digital Guardian offers a wide range of benefits for sales teams, including:
- Advanced Threat Protection: Digital Guardian provides advanced protection against data theft, unauthorized access, and other malicious activities, ensuring that your data is always secure.
- Increased Productivity: By automating many security processes, Digital Guardian frees up valuable time for your sales team, allowing them to focus on selling and growing your business.
- Improved Customer Trust: With Digital Guardian in place, your customers can trust that their data is secure, which can lead to increased loyalty and repeat business.
Features
Some of the key features of Digital Guardian include:
- Next-gen endpoint protection: Protects against advanced threats and malware, including ransomware and zero-day exploits.
- Network visibility and control: Provides complete visibility and control over network activity, ensuring that only authorized users and devices have access to sensitive information.
- Machine learning: Uses artificial intelligence to analyze and respond to threats in real-time, providing faster and more accurate threat detection.
- Integration with existing security tools: Integrates with your existing security infrastructure, providing a comprehensive view of your security posture.
Dashboard
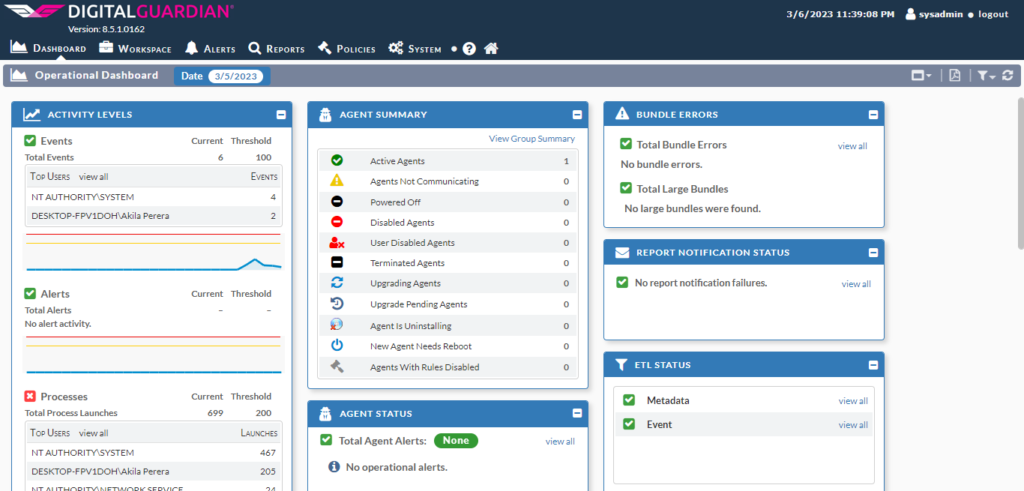
Digital guardian dashboard is designed to help organizations stay on top of potential cybersecurity threats and maintain a proactive approach to cybersecurity. By monitoring key metrics and providing real-time alerts, organizations can quickly respond to threats and take steps to protect their systems and data.
- Threat alerts: Displays any detected security incidents, including alerts from intrusion detection and prevention systems, firewalls, and other security tools.
- Vulnerability management: Displays the organization’s current vulnerability status, including a list of critical and high-risk vulnerabilities and any remediation efforts underway.
- Compliance monitoring: Displays whether the organization is meeting regulatory compliance requirements, such as HIPAA or PCI DSS.
- User behavior analytics: Displays any anomalous user behavior, such as users accessing systems they shouldn’t or logging in from unusual locations.
- Risk management: Displays the organization’s overall risk posture, including a list of high-risk assets and vulnerabilities.
- Asset inventory: Displays an up-to-date inventory of all IT assets, including hardware, software, and other resources.
- Incident response: Displays information about any ongoing security incidents, including the status of investigations and any mitigation efforts underway.
Login
Installing DG Agents on Endpoints
Typically we have to create agent using the resource file and deploy on to the packages.
Resources Files
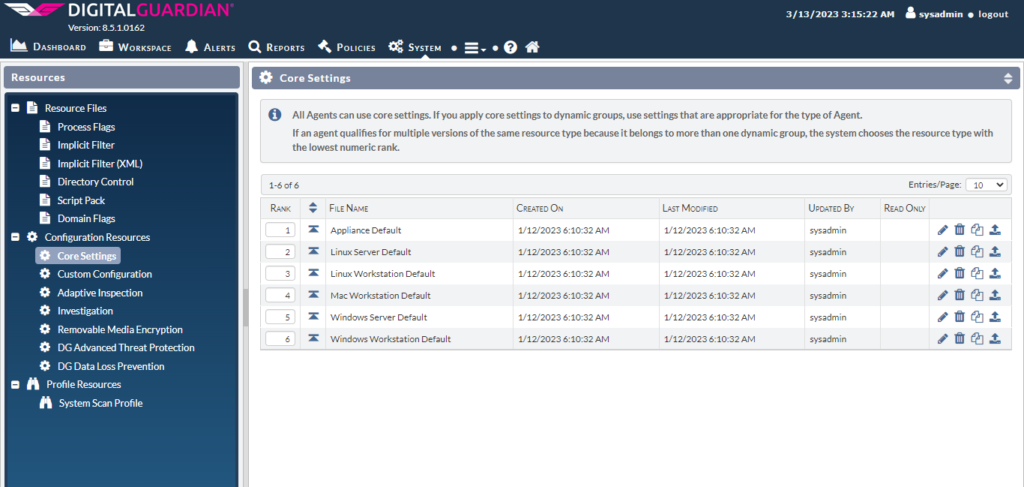
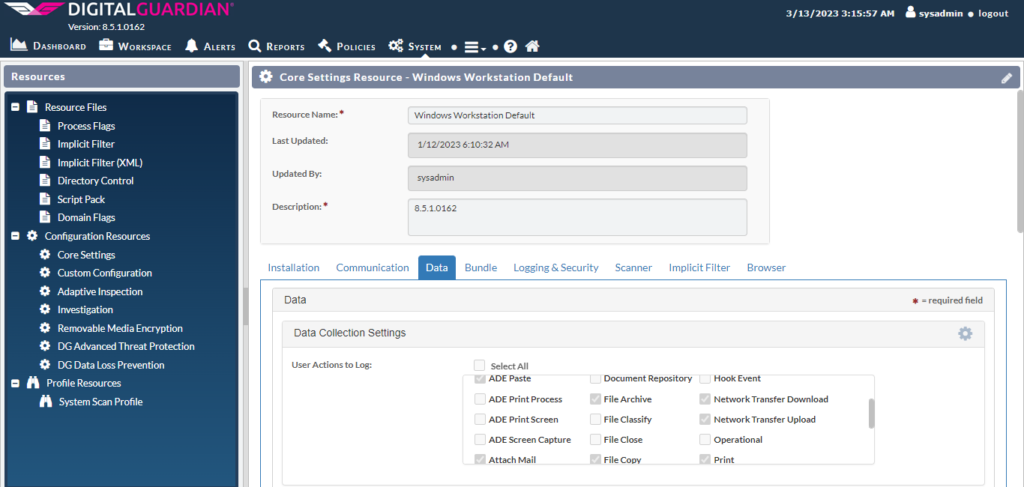
In this we can select and do the configuration.
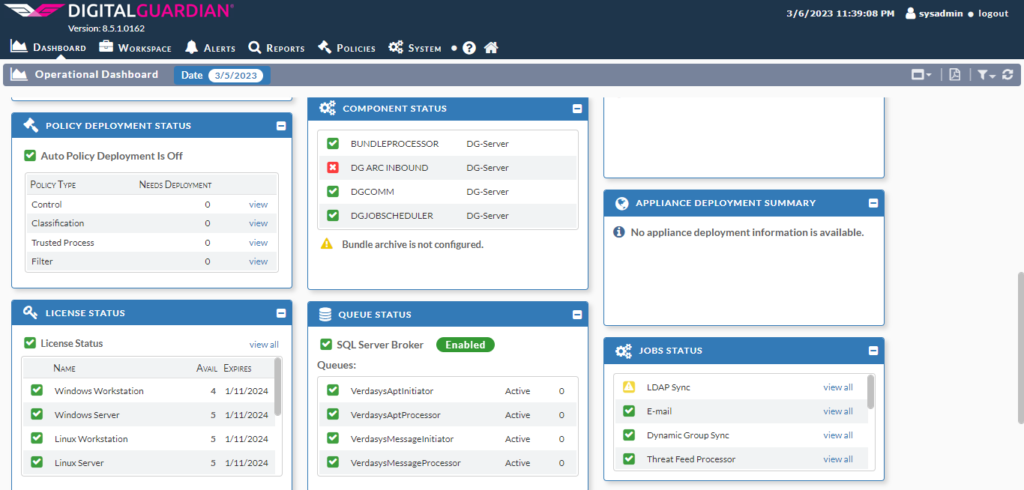
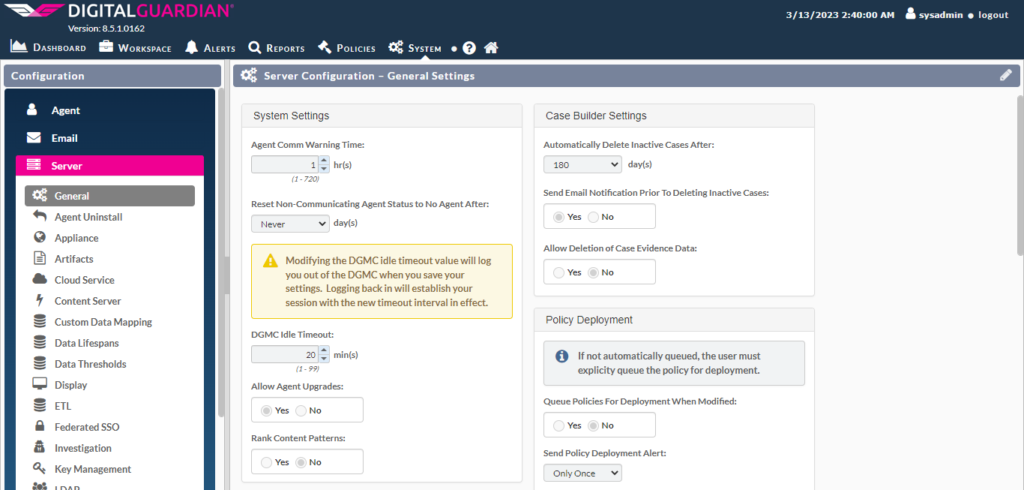
Server Configuration General Settings overview.
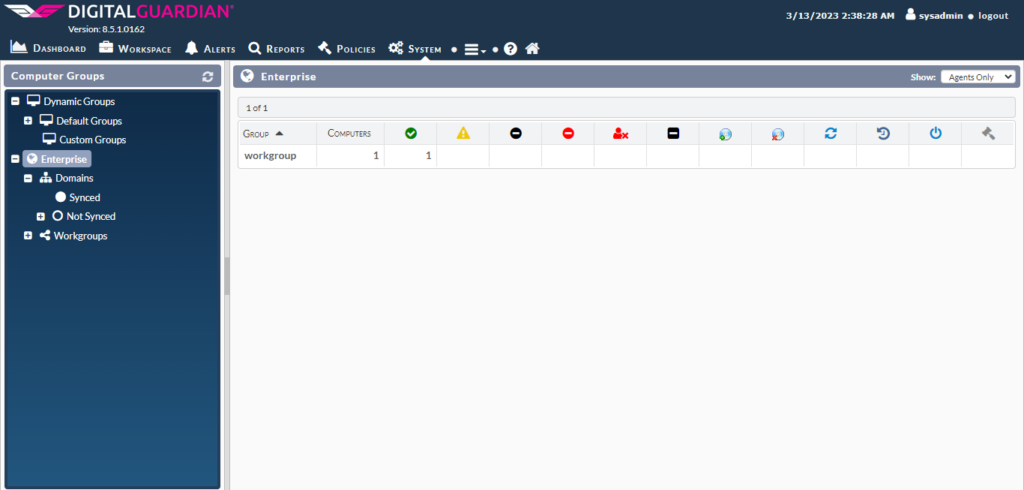
Configuring the Computers
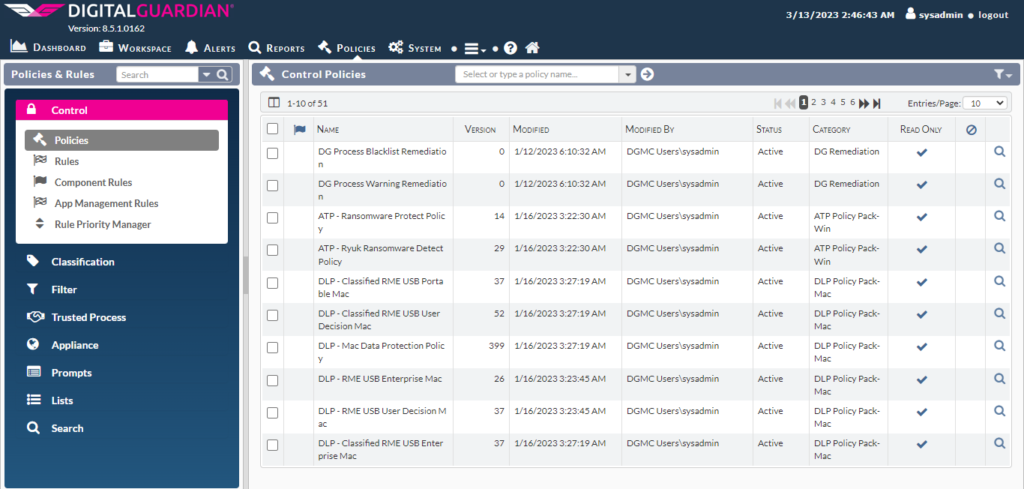
Configuring Control Policies
Digital Guardian’s control policies are designed to protect sensitive data and prevent data breaches by enforcing security policies and monitoring user activity. The dashboard in Digital Guardian provides an overview of the control policies that have been created and their associated rules.
Here are the steps to view the control policies in the dashboard:
- Log in to the Digital Guardian dashboard with your administrator credentials.
- From the main menu, click on “Policies” and then select “Control Policies”.
- You will see a list of control policies that have been created, along with their associated rules and descriptions.
- Click on a policy to view its rules in detail. You can see the conditions that are used to trigger the policy, the actions that are taken when the policy is triggered, and any exceptions or exclusions that have been defined.
- The dashboard also provides an overview of the policy activity, showing the number of incidents that have been triggered and the distribution of incidents by severity level.
The control policies in Digital Guardian are a powerful tool for securing sensitive data and preventing data breaches. By using the dashboard to monitor policy activity and adjust policies as needed, administrators can ensure that their organization’s data is protected and compliant with regulatory requirements.
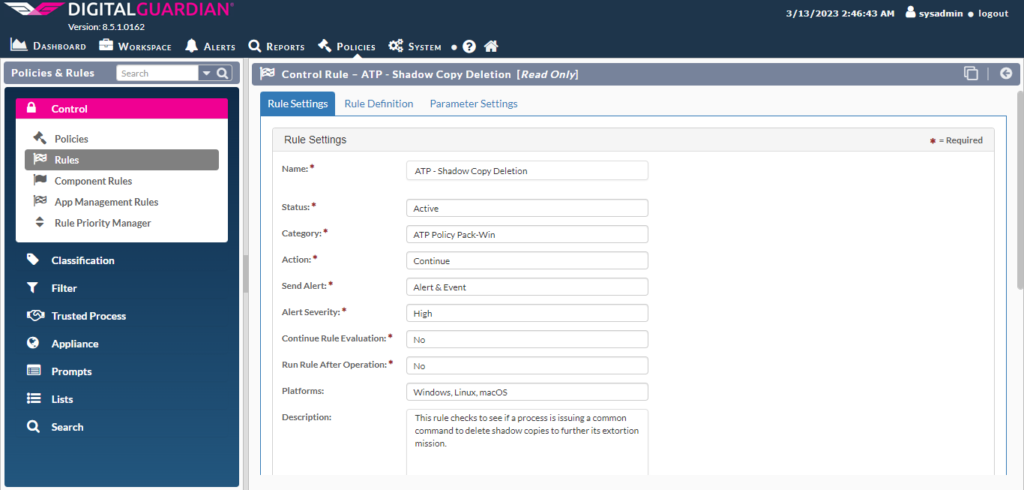
Configuring the Control Rules
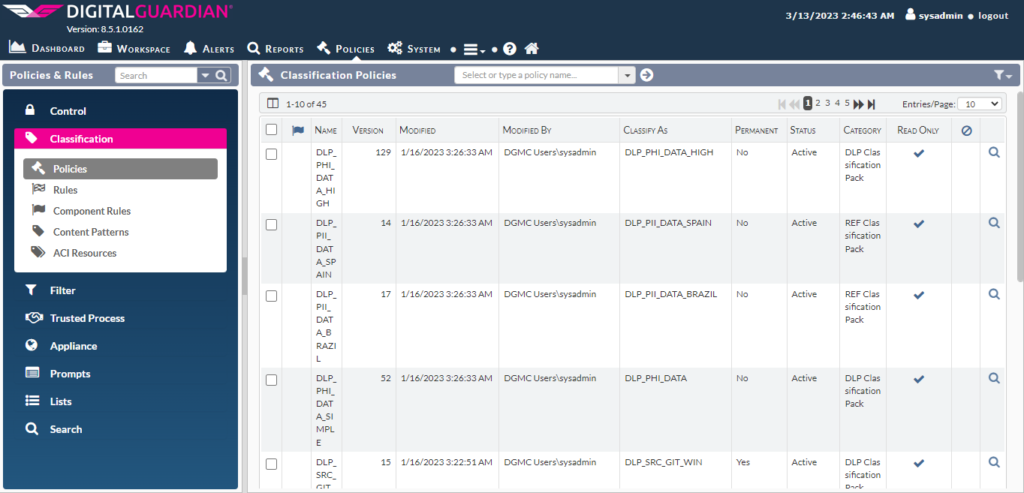
Configuring Classification Policies
Digital Guardian’s classification policies are used to identify and label sensitive data based on its level of sensitivity. The dashboard in Digital Guardian provides an overview of the classification policies that have been created and their associated rules.
Here are the steps to view the classification policies in the dashboard:
- Log in to the Digital Guardian dashboard with your administrator credentials.
- From the main menu, click on “Policies” and then select “Classification”.
- You will see a list of classification policies that have been created, along with their associated rules and descriptions.
- Click on a policy to view its rules in detail. You can see the conditions that are used to identify sensitive data and the actions that are taken when the policy is triggered.
- The dashboard also provides an overview of the classification activity, showing the number of files that have been classified and the distribution of classification labels.
The classification policies in Digital Guardian are a powerful tool for identifying and protecting sensitive data. By using the dashboard to monitor policy activity and adjust policies as needed, administrators can ensure that their organization’s data is secure and compliant with regulatory requirements.
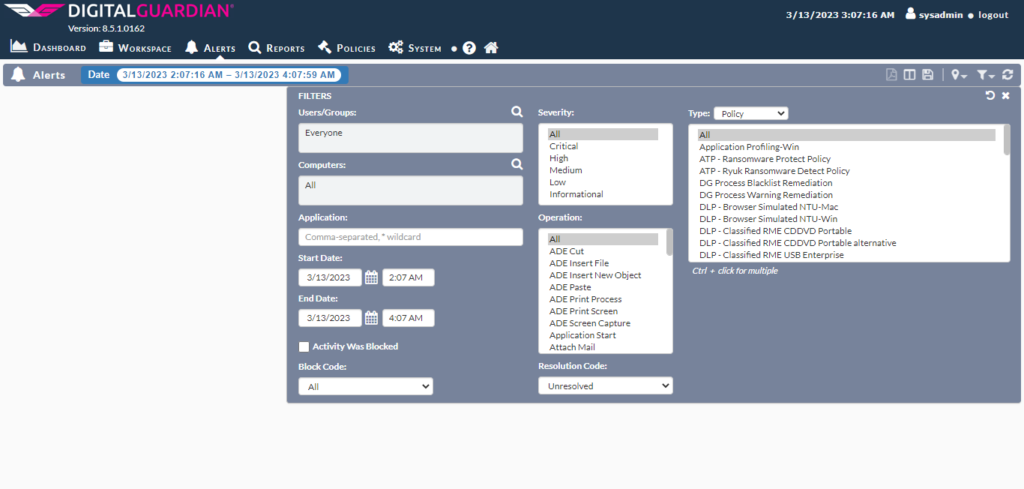
Setting up Alerts
Conclusion
In conclusion, Digital Guardian is an essential tool for anyone concerned about their digital security. With its advanced threat protection, increased productivity, and improved customer trust, it’s a powerful solution for sales teams and businesses of all sizes. So why wait? Protect your digital assets today with Digital Guardian!