Table of Content
- Introduction Microsoft Sentinel
- Gartner Quadrant For SIEM
- Key features of Microsoft Sentinel
- Microsoft Sentinel In Azure
- Configuration Guidelines
- Resource Group
- Deploy Log Analytics & Microsoft Sentinel
- Sentinel Agents for Data Collection
- Conclusion
Introduction
Microsoft Sentinel, also called Azure Sentinel, is a special computer program made by Microsoft. It helps organizations keep their computer systems safe from bad things. It collects and looks at a lot of information about security from different places, like computers and the internet. This program uses smart technology to find and warn about things that might be dangerous. It also helps experts investigate when something bad happens and gives them tools to fix the problem quickly. Microsoft Sentinel works well with other programs and can connect to many different types of information. It can handle a lot of information and can be used in different ways, either just in the cloud or a mix of cloud and regular computers. It’s a useful tool for keeping computers safe and finding and fixing problems.
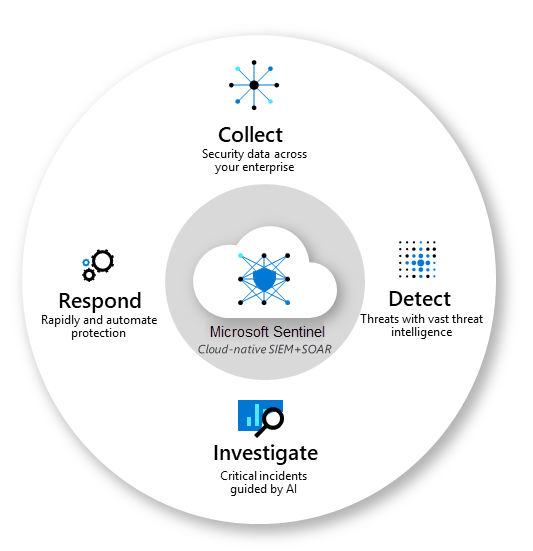
Microsoft Sentinel is a scalable, cloud-native solution that provides:
- Security information and event management (SIEM)
- Security orchestration, automation, and response (SOAR)
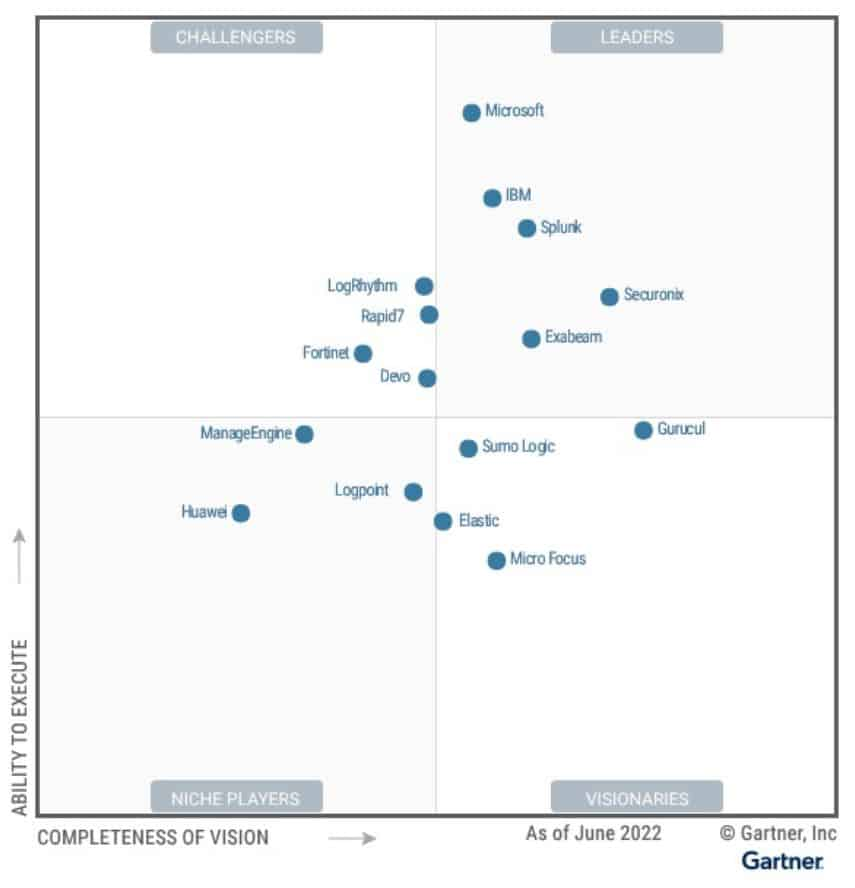
Gartner Quadrant For SIEM
Microsoft is named a Leader in the 2022 Gartner® Magic Quadrant™ for Security Information and Event.
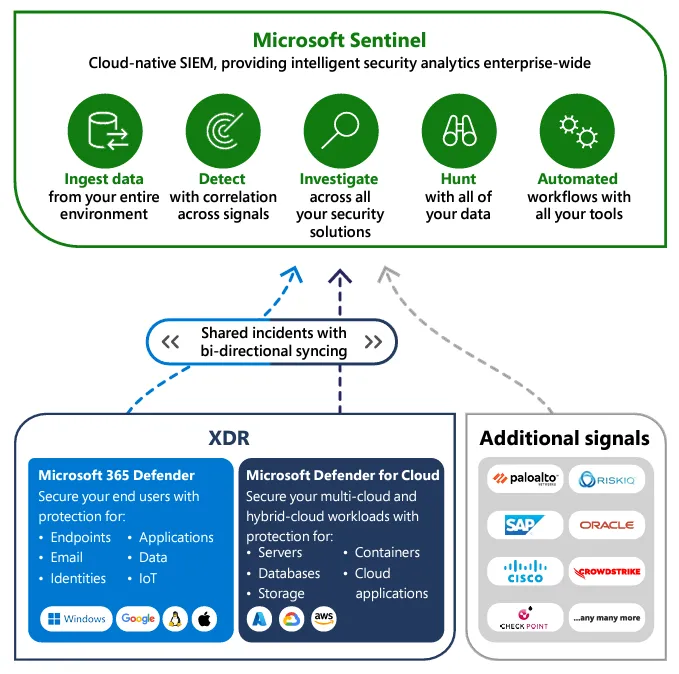
Microsoft Sentinel is a unified Security Operations (SecOps) platform that brings together SIEM with security orchestration, automation, and response (SOAR), user and entity behavior analytics (UEBA), and threat intelligence (TI)—enabling customers to stay ahead of evolving threats while responding quickly to attacks.
Key features of Microsoft Sentinel
- It works well with other Microsoft services and shows all security events in one place.
- It is made to work on the internet, so it can handle lots of security information and use cloud resources.
- It uses smart technology to find and warn about things that might be dangerous, even if they’re not known yet.
- It can automatically fix security problems and has tools to help experts investigate and solve issues quickly.
- It can find indicators of danger by looking at a lot of information and helps experts search for potential threats.
- It can connect with many different types of information sources to monitor security.
Microsoft Sentinel in Azure
Global prerequisites
- Active Azure Subscription. If you don’t have one, create a free account before you begin.
- Log Analytics workspace. Learn how to create a Log Analytics workspace. For more information about Log Analytics workspaces, see Designing your Azure Monitor Logs deployment. You may have a default of 30 days retention in the Log Analytics workspace used for Microsoft Sentinel. To make sure that you can use all Microsoft Sentinel functionality and features, raise the retention to 90 days. Configure data retention and archive policies in Azure Monitor Logs.
- Permissions:
- To enable Microsoft Sentinel, you need contributor permissions to the subscription in which the Microsoft Sentinel workspace resides.
- To use Microsoft Sentinel, you need either contributor or reader permissions on the resource group that the workspace belongs to.
- You might need other permissions to connect specific data sources.
- Microsoft Sentinel is a paid service. Review the pricing options and the Microsoft Sentinel pricing page.
- Review the full pre-deployment activities and prerequisites for deploying Microsoft Sentinel.
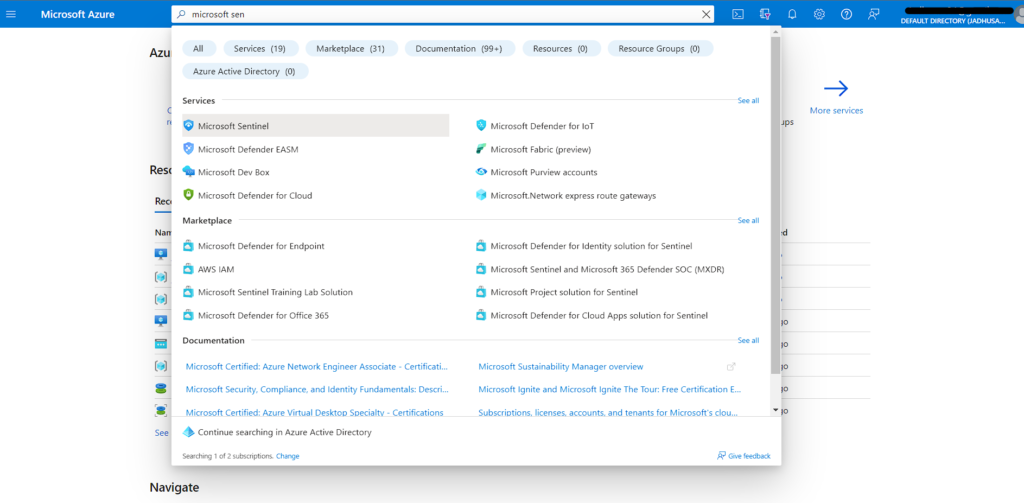
You can search for Microsoft Sentinel in Azure Portal
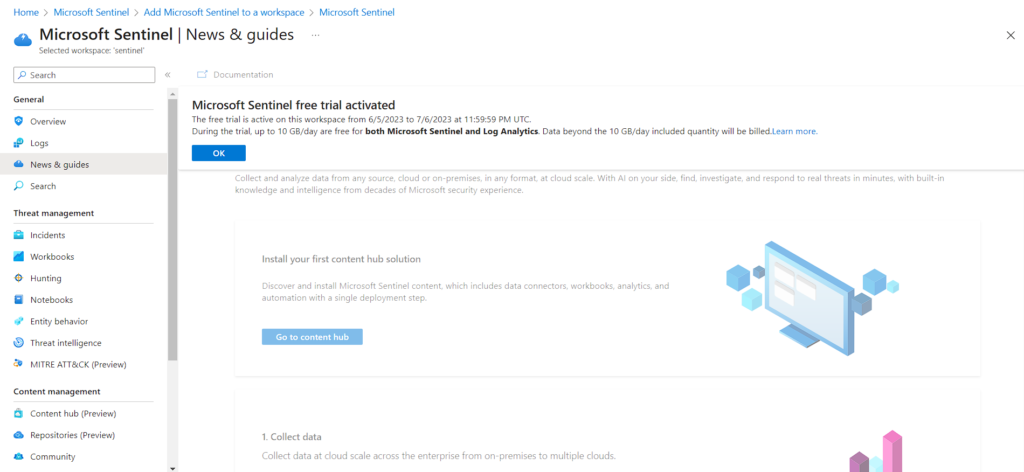
Microsoft Sentinel offers a 31-day free trial.
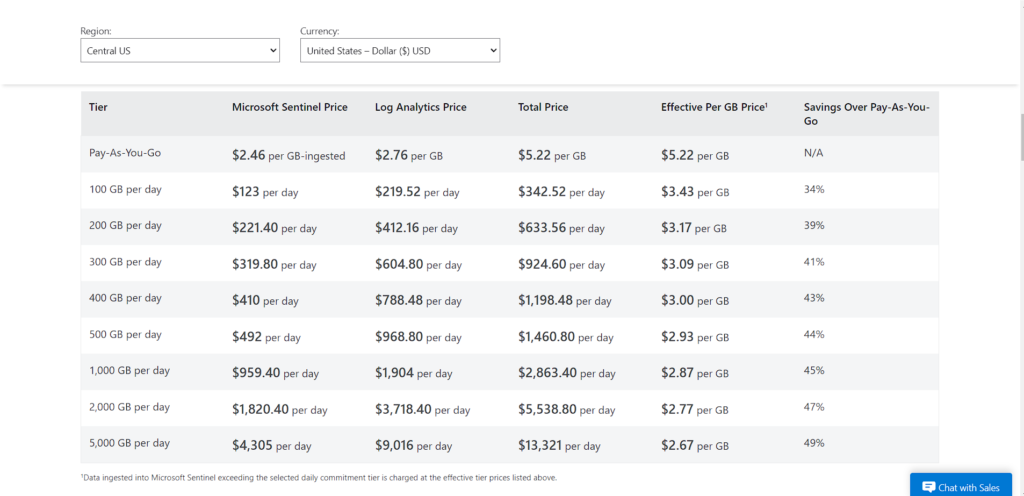
See Microsoft Sentinel pricing for more details.
Configuration Guideline
Configuration Guideline to setup the Microsoft Sentinel Workspace
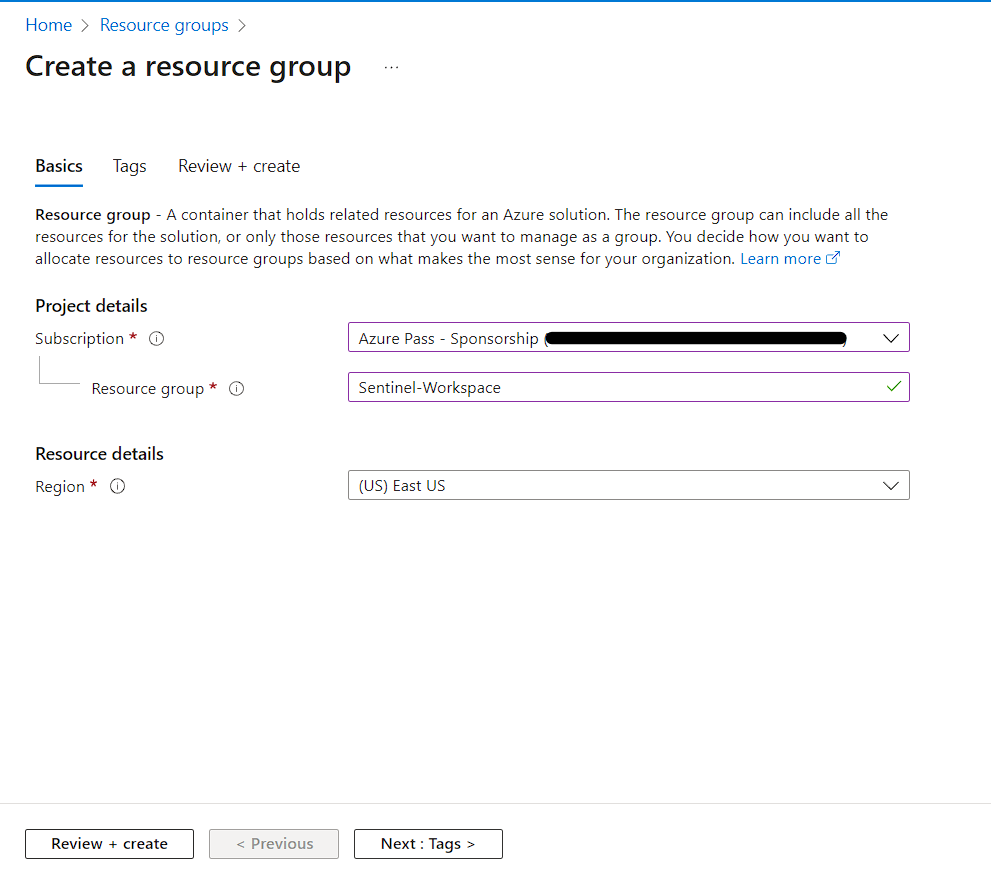
Resource Group
Let’s create Resource Group
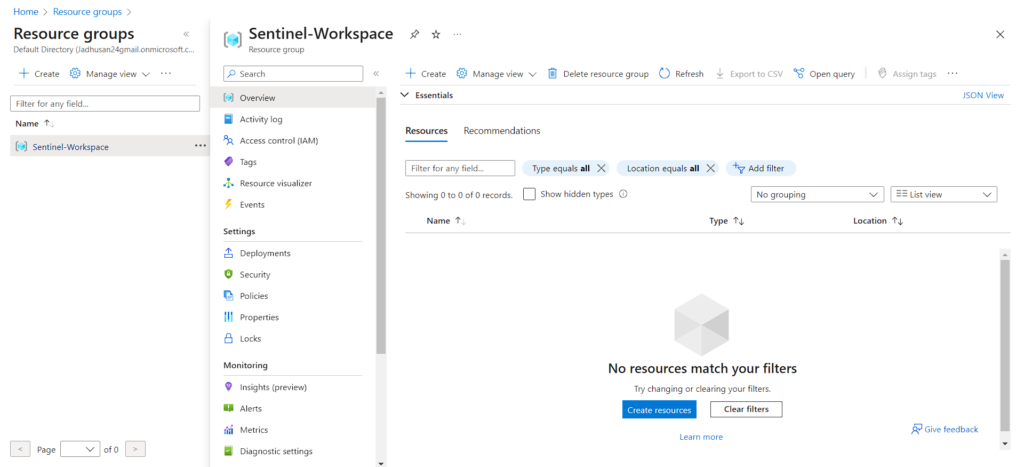
Deploy Log Analytics & Microsoft Sentinel
- Sign-in to the Azure portal using your credentials
- Navigate to the Microsoft Sentinel service by searching for “Sentinel” in the search bar.
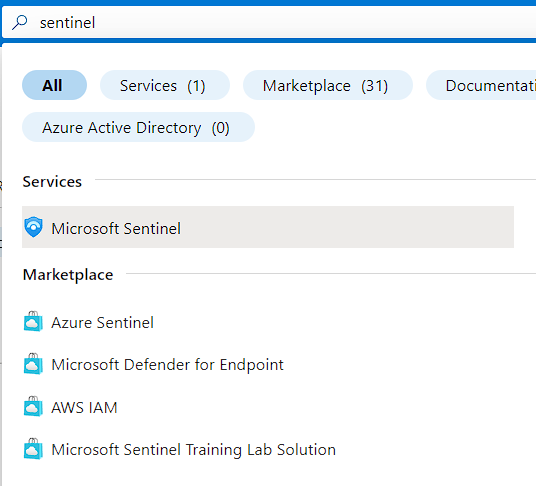
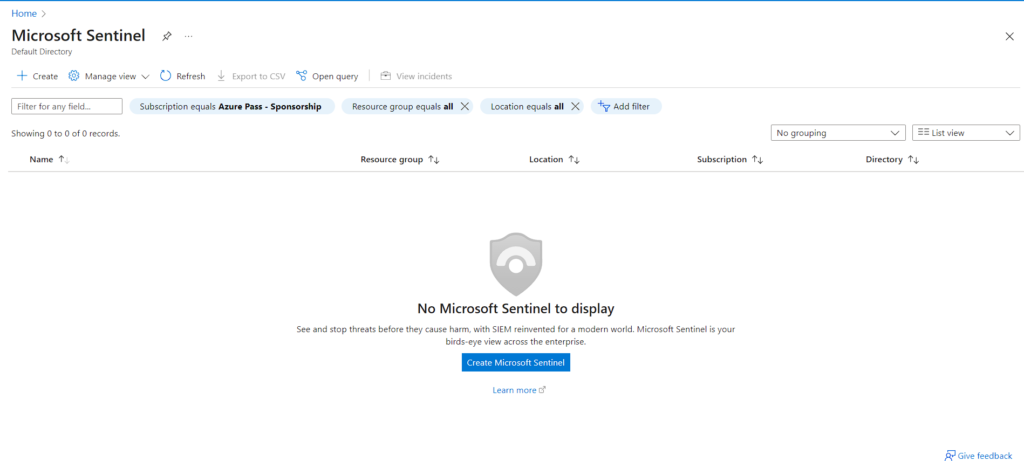
3. Create new Workspace
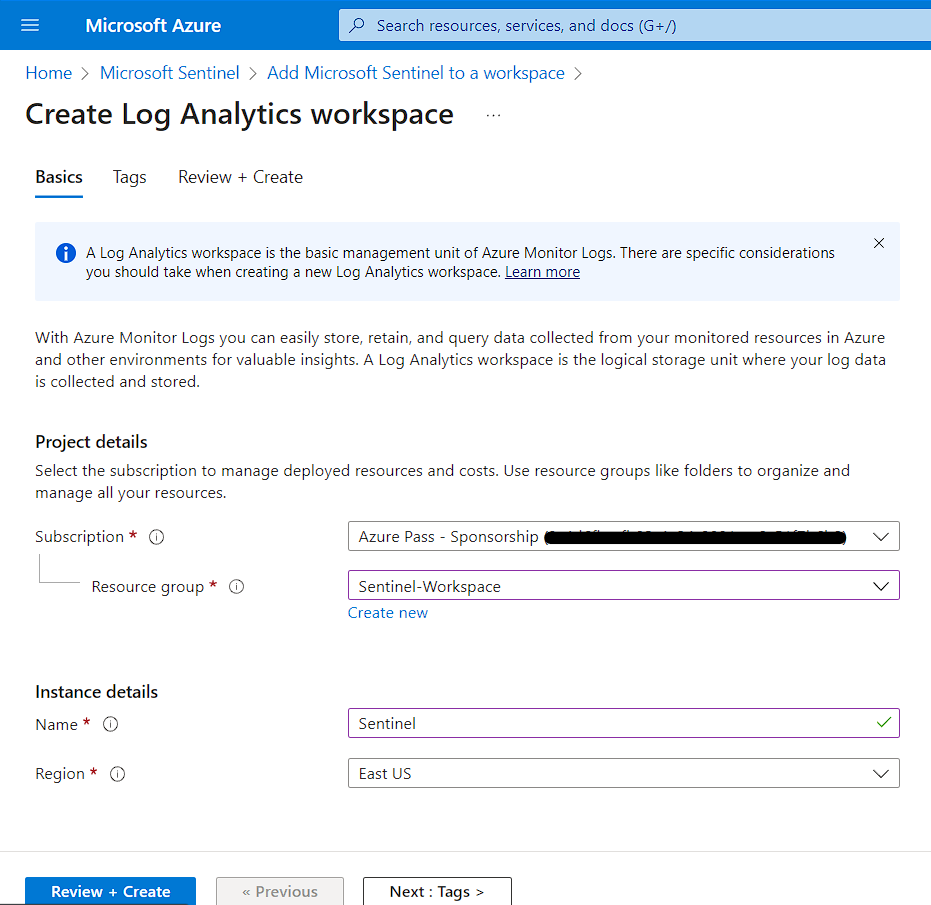
4. Navigate to the Sentinel after deployment is completed
The Log Analytics agents (MMA.OMS) used to collect logs from virtual machines and servers will no longer be supported from August 31, 2024. Plan to migrate to Azure Monitor Agent before this date. Learn more about migrating to Azure Monitor Agent
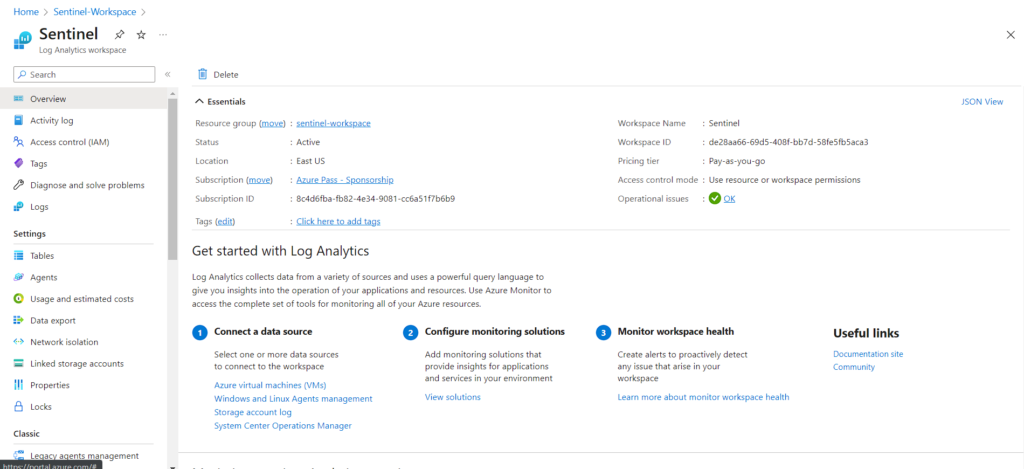
5. Now, click to select the workspace and then click on “Add” button.
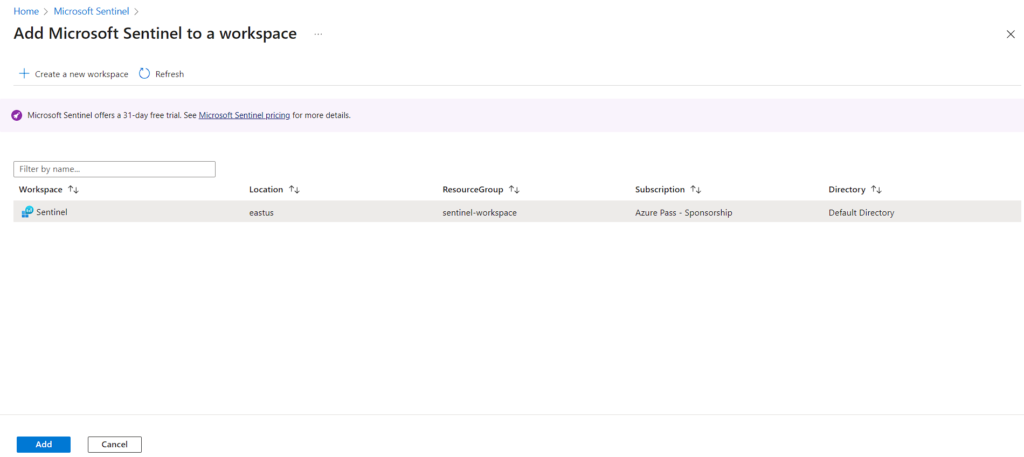
After Added, You will be navigated to the Microsoft Sentinel. Since I’m using Microsoft Sentinel Free Trial it got activated.
Scroll Down and select setting and click Workspace Settings to open the Log Analytics.
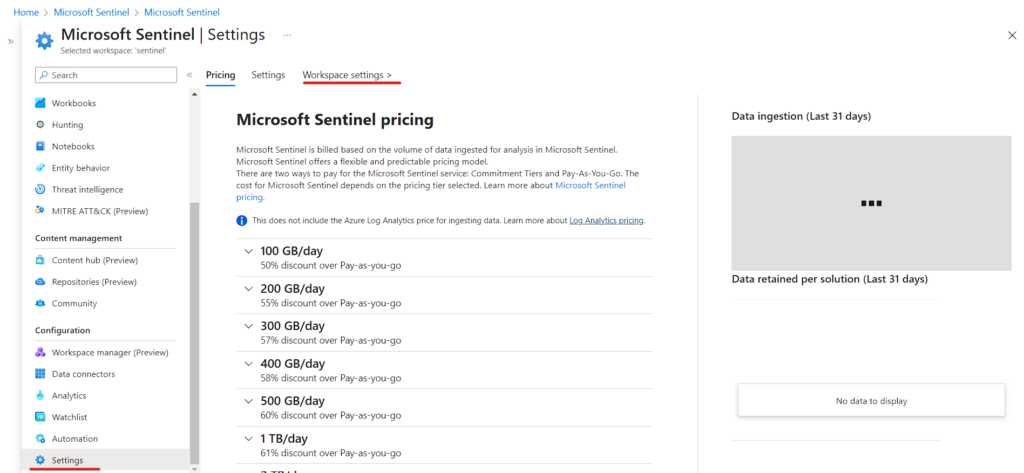
The most important for companies using SIEM is the Retention Period of Data. We can check that on Usage and Estimated Cost.
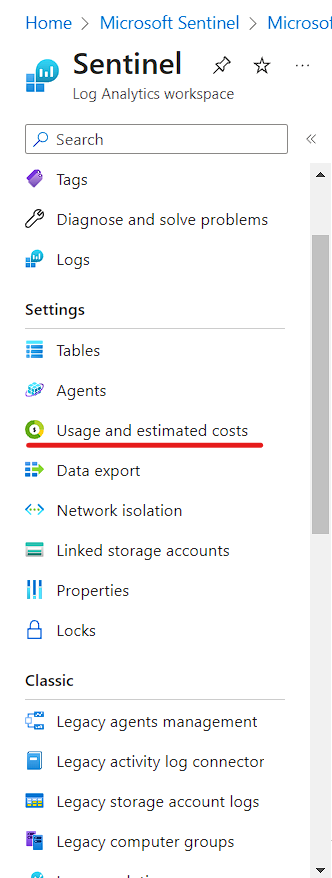
Select Data Retention and customize accordingly
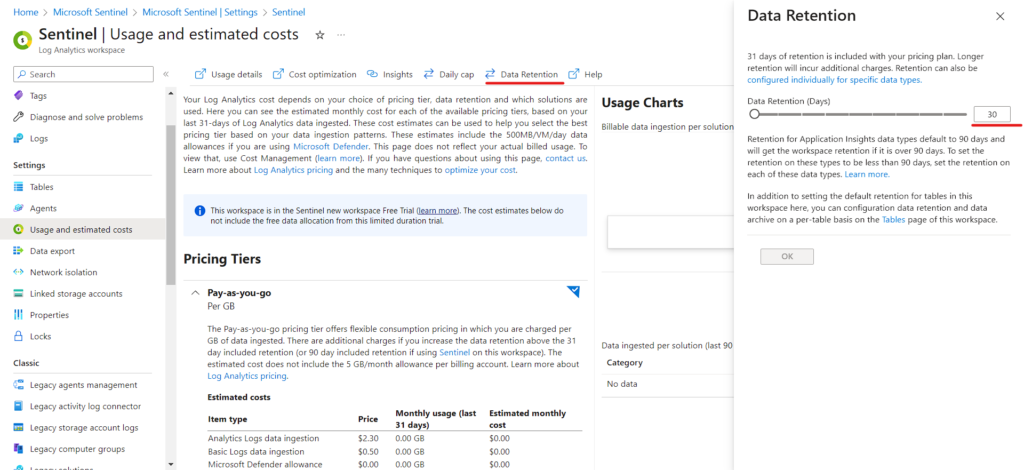
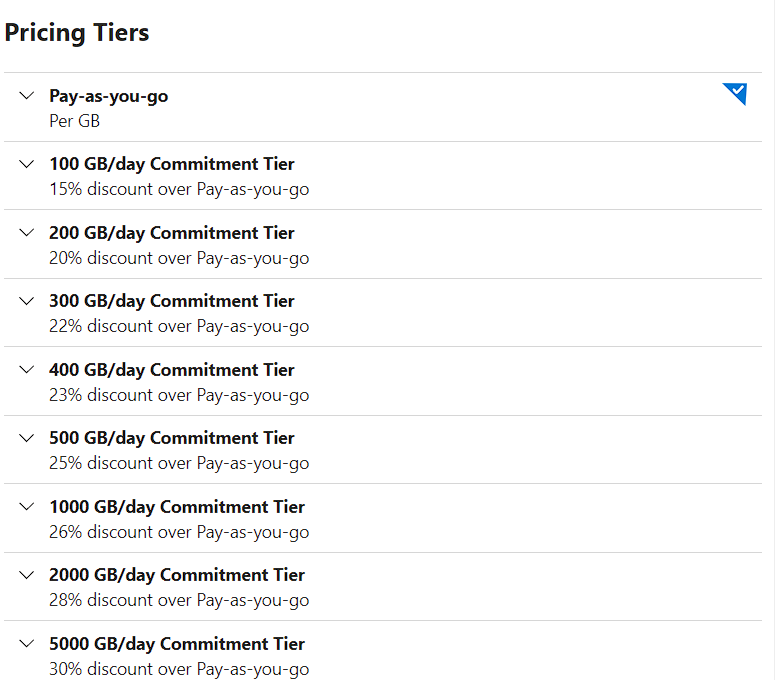
Pricing Tiers for the Companies.
Note: Your Log Analytics cost depends on your choice of pricing tier, data retention and which solutions are used. Here you can see the estimated monthly cost for each of the available pricing tiers, based on your last 31-days of Log Analytics data ingested.
To view that, use Cost Management (learn more).
Learn more about Log Analytics pricing and the many techniques to optimize your cost.
Go back to Microsoft Sentinel and lets configure the Playbook.
Playbooks in Microsoft Sentinel are based on workflows built in Azure Logic Apps, a cloud service that helps you schedule, automate, and orchestrate tasks and workflows across systems throughout the enterprise.
Note: We only need to give permission of Resource Group for sentinel
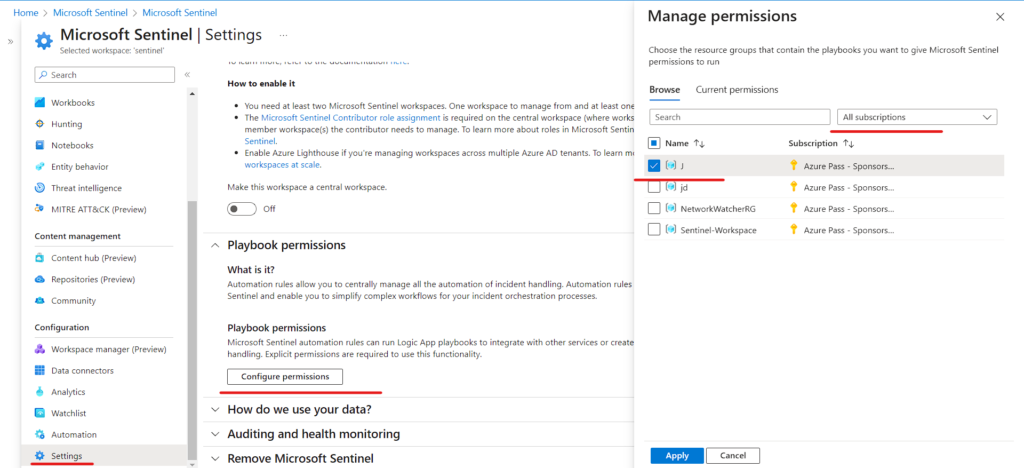
Great job! You have successfully activated Microsoft Sentinel on the portal. Now, you can commence the configuration and customization of your Sentinel workspace to initiate the collection and analysis of security data. This will greatly enhance your ability to detect and respond to potential threats effectively.
Sentinel Agents for Data Collection
Within the Log Analytics realm, a crucial aspect involves establishing agents that effortlessly feed data into your workspaces. The procedure is straightforward: acquire the agent from the designated link in Azure and install it on your desired machines, manually or through automation (we’ll focus on the manual process here). It is vital to meticulously record the Workspace ID and Keys for future use. By following these steps, you’re well on your path to unlocking the complete capabilities of Log Analytics within Microsoft Sentinel.
If your in the Microsoft Sentinel Scroll down, click on “Settings” & then click on “Workspace setings >” to open Log Analytics
Click on “Windows and Linux Agents managemenet”
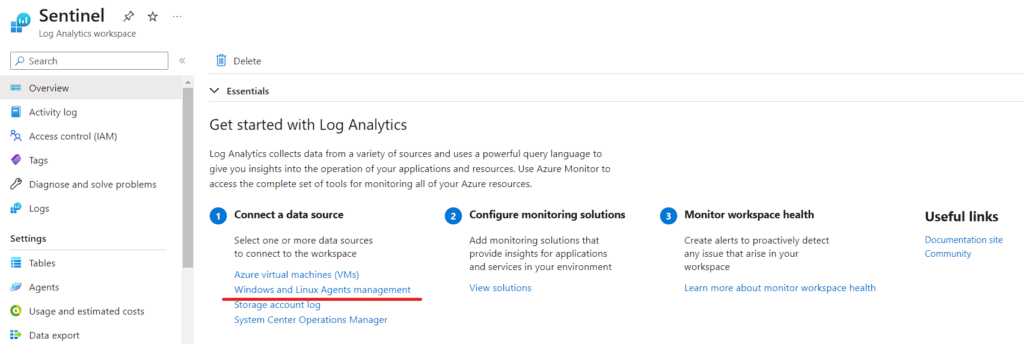
Now, download the agent from the link provided within Azure. Take note of Workspace ID and Keys for future reference.
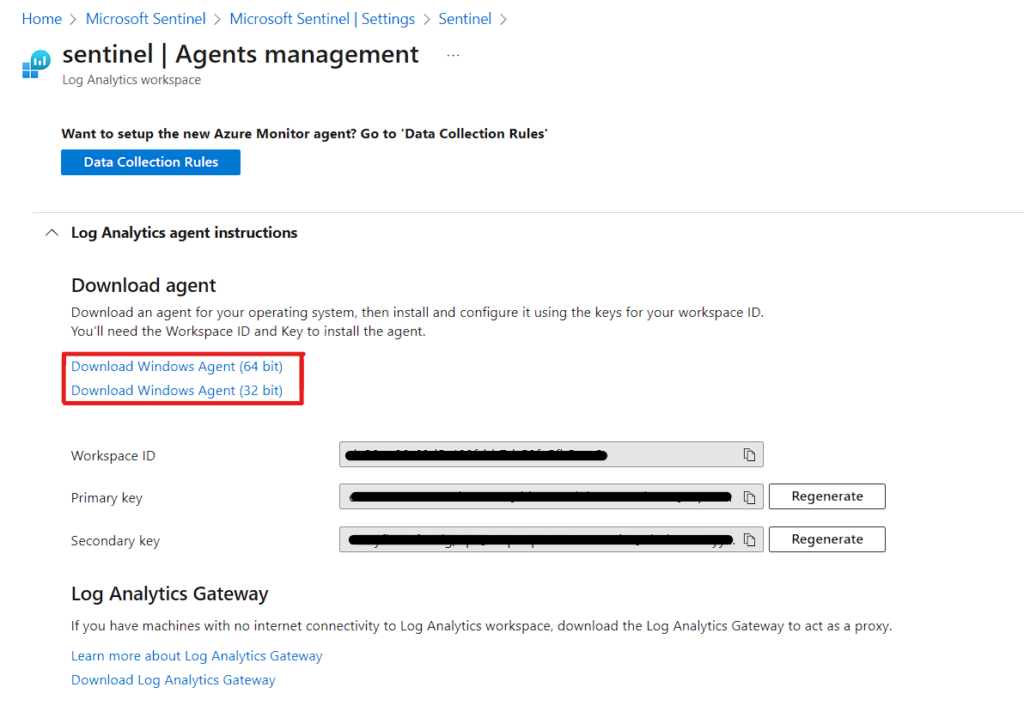
Once downloaded, run the installer on the target machine. To install and set up the agent, you will need the Workspace ID and Primary Key.
Select the checkbox option labeled “Connect the agent to Azure Log Analytics (OMS).”
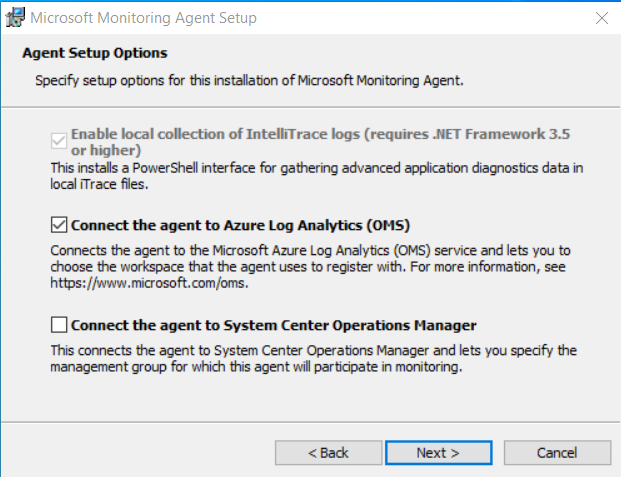
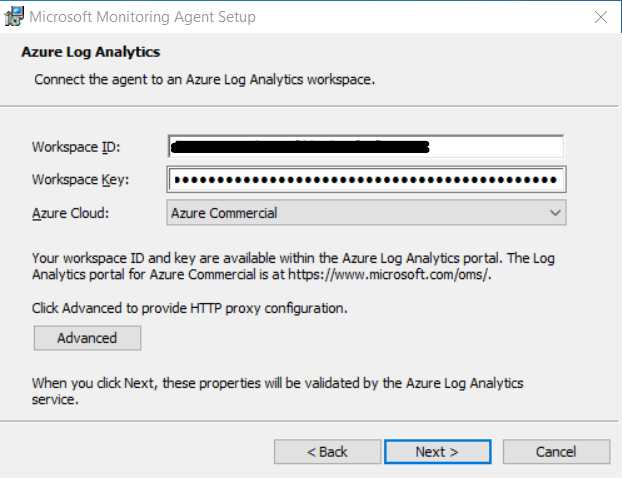
Provide the Workspace ID and Primary Key when prompted. Ensure that you accurately enter the Workspace ID and Primary Key to establish the correct connection.
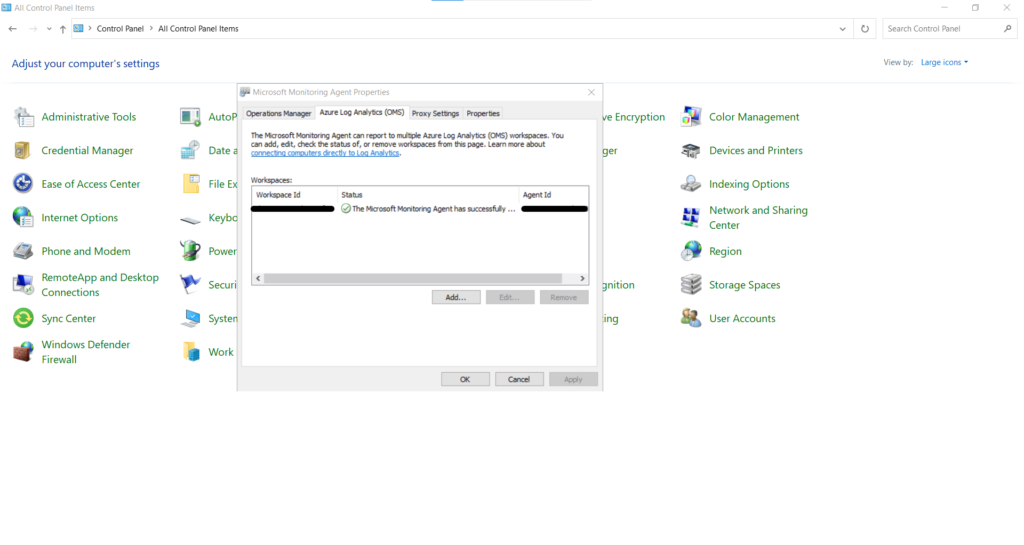
After successfully installing the agent, you can easily configure its options from Control Panel.
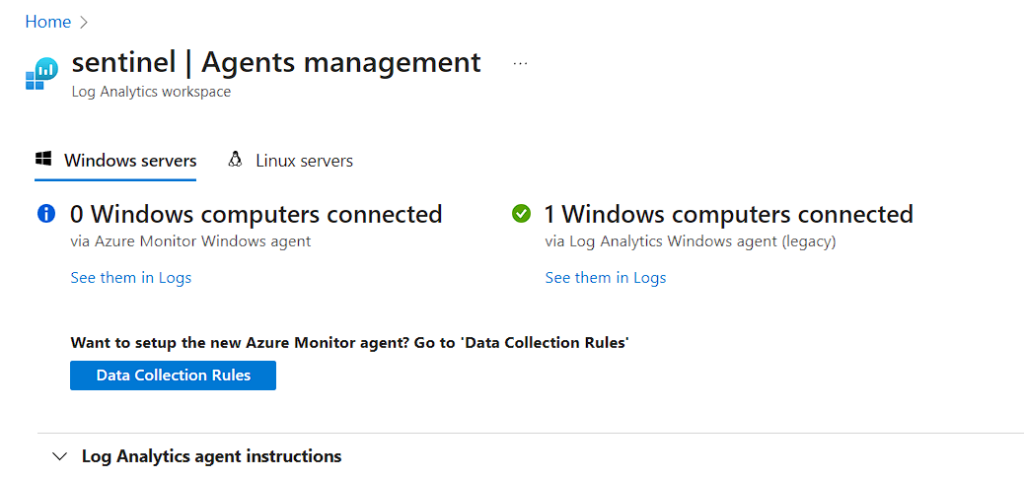
Now you can see the Windows computers connected via Log Analytics
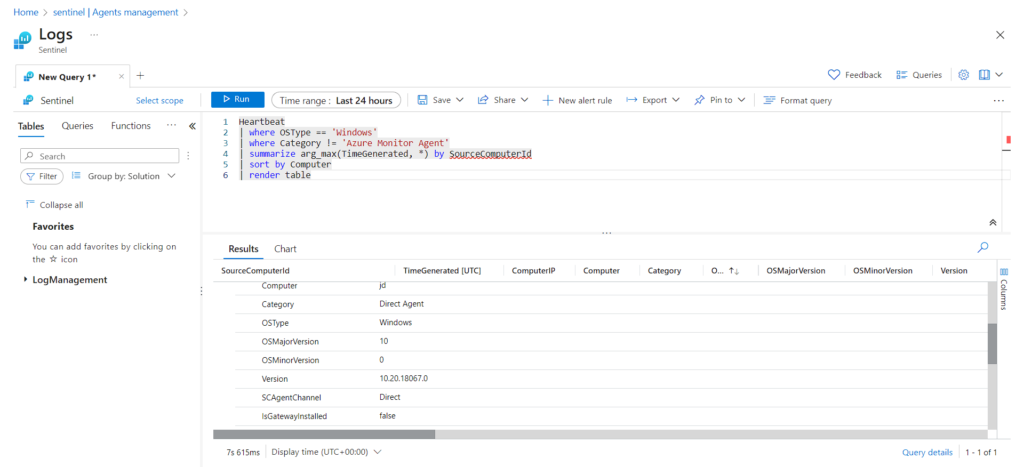
In the Logs, You can do the queries and see the results
Conclusion
In conclusion, Microsoft Sentinel, also known as Azure Sentinel, is a powerful tool designed by Microsoft to enhance the security of computer systems. It collects and analyzes security information from various sources, providing organizations with a comprehensive view of potential threats. Key features of Microsoft Sentinel include its seamless integration with other Microsoft services, scalability for handling large amounts of security data, smart technology for proactive threat detection, and automation capabilities for quick issue resolution. By following configuration guidelines, such as creating a Log Analytics workspace and deploying Microsoft Sentinel, organizations can effectively utilize the tool to detect, investigate, and respond to security incidents. Installing Sentinel agents on machines further enables effortless data collection for comprehensive security analysis. Microsoft Sentinel empowers organizations to keep their systems safe, identify and resolve security issues efficiently, and leverage the full potential of Log Analytics for robust threat management.
To learn more about Microsoft Security solutions, see:
- Microsoft Sentinel: Azure Sentinel – Cloud-native SIEM Solution | Microsoft Azure
- Microsoft Pricing: Azure Sentinel Pricing | Microsoft Azure
- SEIM & XDR: Integrated Threat Protection with SEIM & XDR
- Accelerate migration to Microsoft Sentinel: Plan your migration to Microso ft Sentinel | Microsoft Docs
- Learn More: Microsoft Sentinel documentation | Microsoft Docs
- Customer Success Stories: https://customers.microsoft.com/

