Displaying possible routes across an IP network.
DESCRIPTION
Basically, you need to have the knowledge of OSI model in networking and familiar with python language working with ICMP protocol.
Traceroute and tracert are computer network diagnostic commands for displaying possible routes and measuring transit delays of packets across an Internet Protocol network.
Ping is used to test connectivity between two hosts but does not provide information about the details of devices between the hosts. Traceroute (tracert) is a utility that generates a list of hops that were successfully reached along the path. This list can provide important verification and troubleshooting information. If the data reaches the destination, then the trace lists the interface of every router in the path between the hosts. If the data fails at some hop along the way, the address of the last router that responded to the trace can provide an indication of where the problem or security restrictions are found.
Round Trip Time (RTT)
Using traceroute provides round-trip time for each hop along the path and indicates if a hop fails to respond. The round-trip time is the time a packet takes to reach the remote host and for the response from the host to return. An asterisk (*) is used to indicate a lost or unreplied packet.
This information can be used to locate a problematic router in the path or may indicate that the router is configured not to reply. If the display shows high response times or data losses from a particular hop, this is an indication that the resources of the router or its connections may be stressed.
IPv4 TTL and IPv6 Hop Limit
Traceroute makes use of a function of the TTL field in IPv4 and the Hop Limit field in IPv6 in the Layer 3 headers, along with the ICMP Time Exceeded message.
ICMP
Although IP is only a best-effort protocol, the TCP/IP suite does provide for error messages and informational messages when communicating with another IP device. These messages are sent using the services of ICMP. The purpose of these messages is to provide feedback about issues related to the processing of IP packets under certain conditions, not to make IP reliable. ICMP messages are not required and are often not allowed within a network for security reasons.
ICMP is available for both IPv4 and IPv6. ICMPv4 is the messaging protocol for IPv4. ICMPv6 provides these same services for IPv6 but includes additional functionality. In this course, the term ICMP will be used when referring to both ICMPv4 and ICMPv6.
The types of ICMP messages, and the reasons why they are sent, are extensive. The ICMP messages common to both ICMPv4 and ICMPv6 and discussed in this module include:
- Host reachability
- Destination or Service Unreachable
- Time exceeded
Time Exceeded
An ICMPv4 Time Exceeded message is used by a router to indicate that a packet cannot be forwarded because the Time to Live (TTL) field of the packet was decremented to 0. If a router receives a packet and decrements the TTL field in the IPv4 packet to zero, it discards the packet and sends a Time Exceeded message to the source host.
ICMPv6 also sends a Time Exceeded message if the router cannot forward an IPv6 packet because the packet has expired. Instead of the IPv4 TTL field, ICMPv6 uses the IPv6 Hop Limit field to determine if the packet has expired.
Note: Time Exceeded messages are used by the traceroute tool.
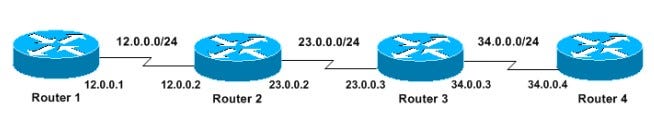
This illustrates the use of traceroute command
Background Information
TTL stands for Time To Live. When a TCP packet is sent, its TTL is set, which is the number of routers (hops) it can pass through before the packet is discarded. As the packet passes through a router the TTL is decremented until, when the TTL reaches zero, the packet is destroyed and an ICMP “time exceeded” message is returned. The return message’s TTL is set by the terminating router when it creates the packet, and decremented normally.
Trace Route works by setting the TTL for a packet to 1, sending it towards the requested destination host, and listening for the reply. When the initiating machine receives a “time exceeded” response, it examines the packet to determine where the packet came from — this identifies the machine one hop away. Then the tracing machine generates a new packet with TTL 2, and uses the response to determine the machine 2 hops away, and so on.
Unfortunately not all TCP stacks behave correctly. Some TCP stacks set the TTL for the ICMP “time exceeded” message to that of the message being killed. So if the TTL is 0, the packet will be killed by the next machine to which it is passed. This can have two effects on a trace. If the computer is an intermediate machine in the trace, the entry will remain blank. No information is returned to the machine conducting the trace because the “time exceeded” message never makes it back. If the machine you are doing a trace to has this bug in its TCP stack, return packets won’t reach the originating machine unless the TTL is high enough to cover the round trip. So Trace Route will show a number of failed connections equal to n (the number of hops to the destination machine) minus 1.
Example
Router 1# traceroute 34.0.0.4
Type escape sequence to abort.
Tracing the route to 34.0.0.4
1 12.0.0.2 4 msec 4 msec 4 msec
2 23.0.0.3 20 msec 16 msec 16 msec
3 34.0.0.4 16 msec * 16 msec
PACKAGES
import socket : socket() I used socket to capture the traffics. so created a socket connection to listen for packets.
try:
# Create the socket
icmp_socket = socket.socket(
socket.AF_INET, socket.SOCK_RAW, icmp_proto)
except socket.error as e:
print(f”Error {e}”)
exit(1)
# increase the ttl and id to the hop number
time_to_live = hop
id = hop
# Ping the host, and if ping is successful then break
if(ping(dest_addr, icmp_socket, time_to_live, id, timeout)):
icmp_socket.close()
break
# if ping timed out and returned false close socket and restart with a longer ttl and a new id
icmp_socket.close()
exit(0)
import struct : I used struct for two ways struct.unpack() and struct.pack() for the headers.
initial_header = struct.pack(“bbHHh”, 8, 0, initial_checksum, id, 1)
And after all the debugging and using the oop the program was ready. You can find the source code in my Github.
TESTED WITH ;
W I N D O W S
Excute this program using WSL
- open CMD
- navigate to file path
- type the following command
python tracert.py www.google.com
python tracert.py 8.8.8.8
L I N U X
- open terminal
- navigate to file path
- type the following command
sudo python3 tracert.py www.google.com
sudo python3 tracert.py 8.8.8.8
REQUIRMENT
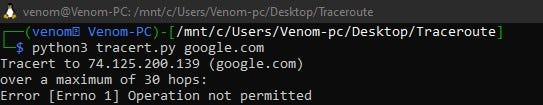
- Run using Sudo privilege — LINUX
- Run using Administration privilege — WINDOWS
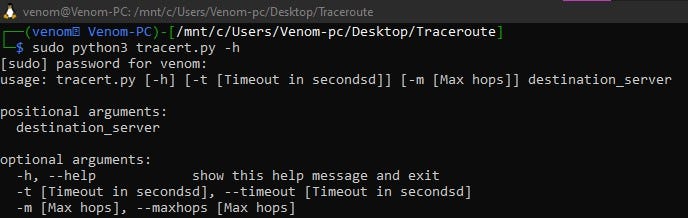
- Use -h for help
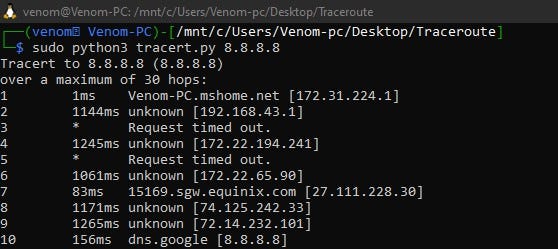
Output
- Domain name
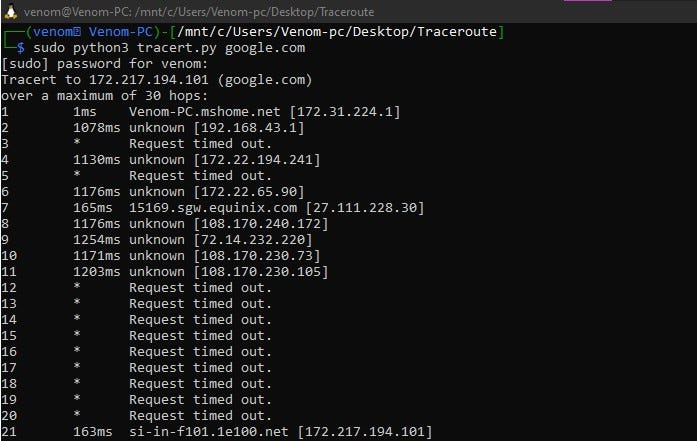
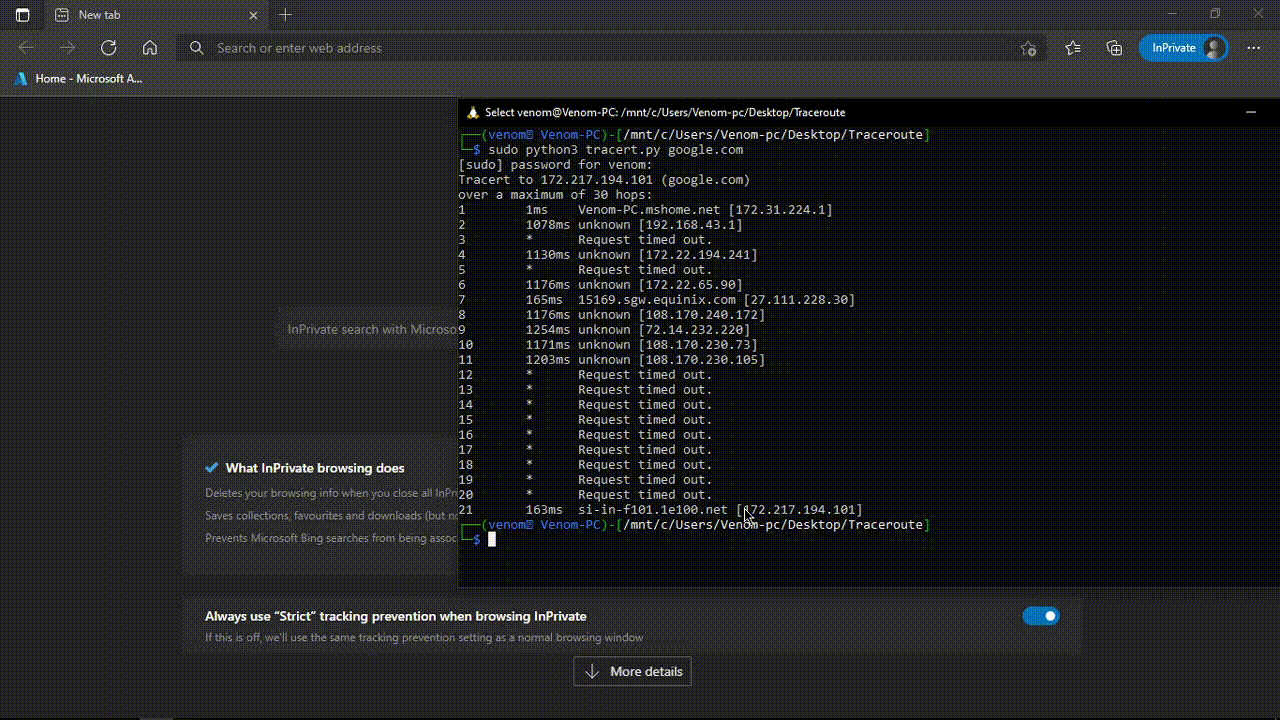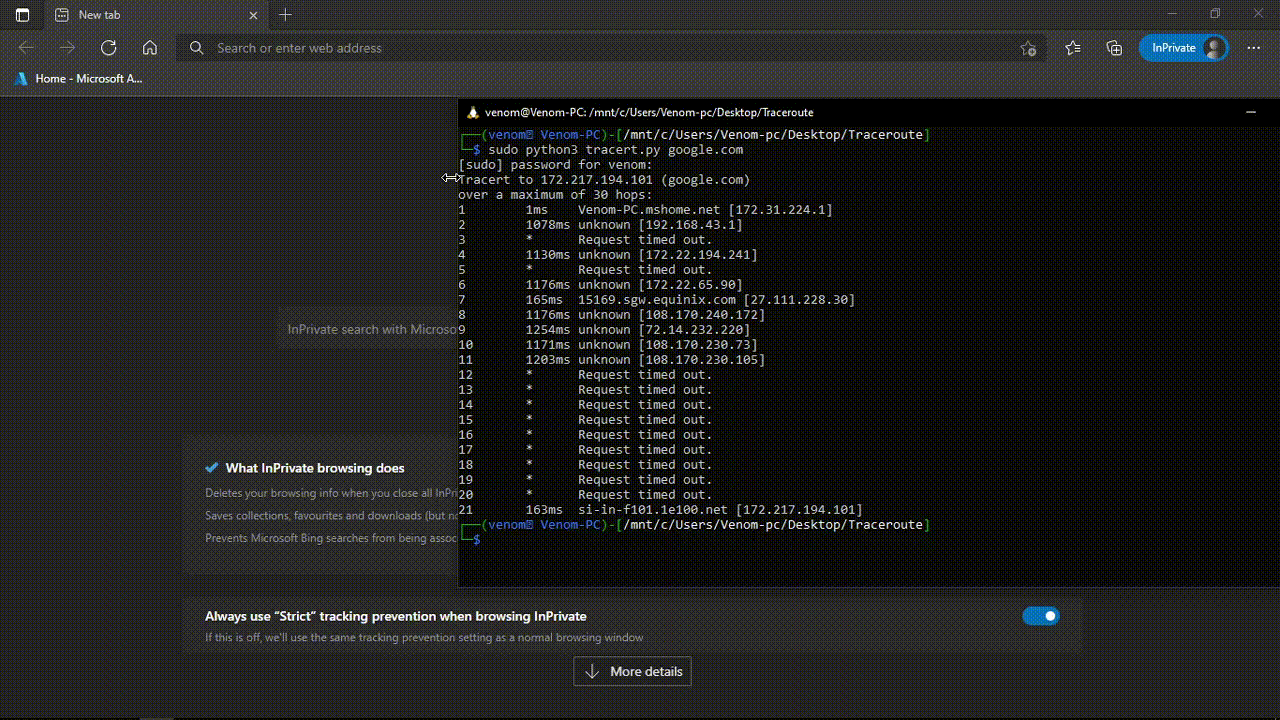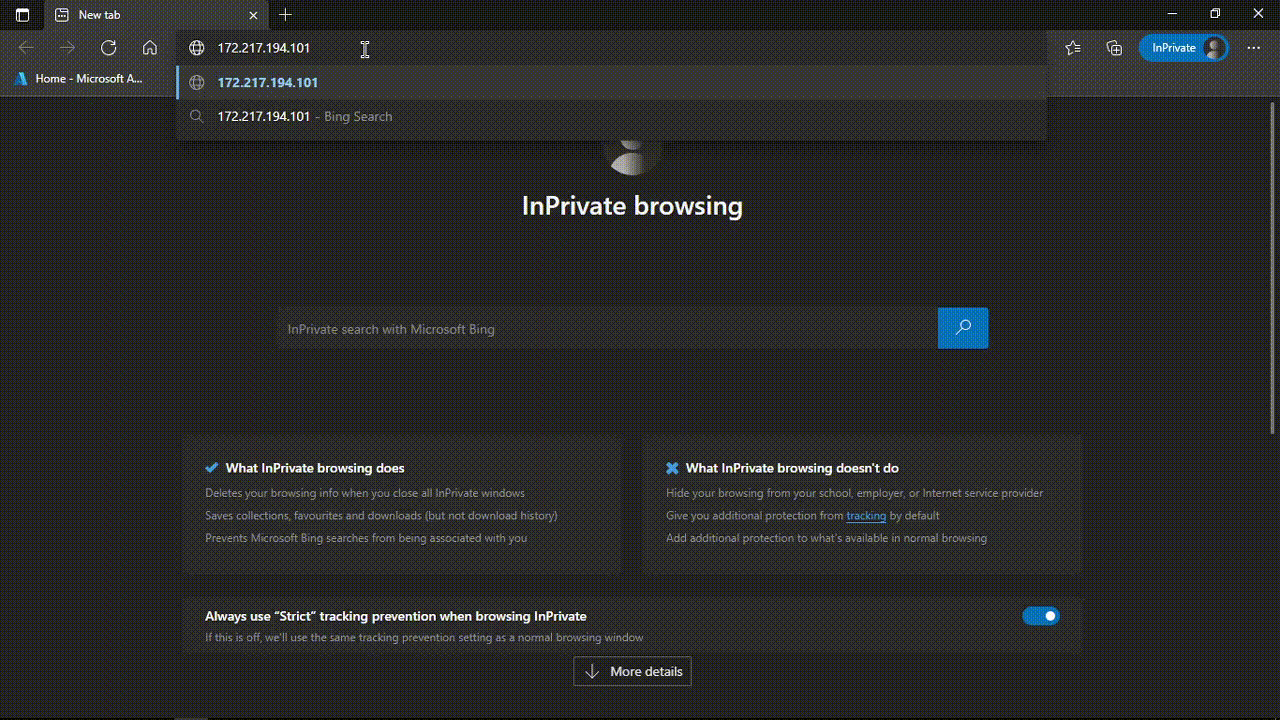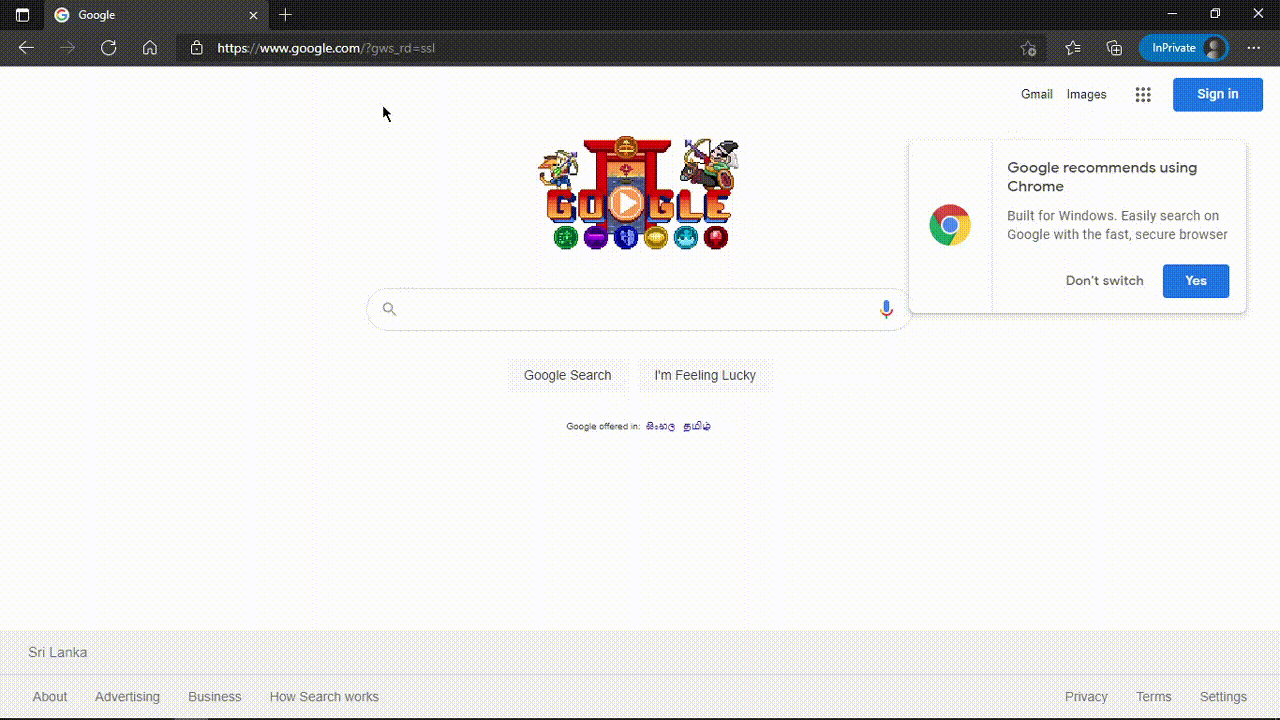
- Ip Address
- root permission
- Help
Originally published at https://github.com.

