Introduction
Managing user and computer accounts in Active Directory is crucial for maintaining an organized and secure network environment. There are various methods to accomplish this, such as using the Active Directory Users and Computers (ADUC) tool or the Active Directory Administrative Center (ADAC). ADUC provides a graphical user interface (GUI) for configuring user and computer accounts, while ADAC utilizes PowerShell commands in the background to automate these tasks.
Automating the creation of Active Directory accounts can significantly streamline the process. PowerShell commands like New-ADUser and Remove-ADUser allow for easy user and computer account management. By leveraging the CLI (Command-Line Interface), administrators can quickly configure and automate AD accounts based on various parameters, such as name, path, attributes, and password.
Performing bulk Active Directory operations is made possible by using tools like csvde, which facilitates exporting and importing data in Active Directory using CSV files. Other commands like dsadd and dsmod enable adding and modifying existing objects, while PowerShell scripts can be utilized to add multiple users to Active Directory simultaneously.
Managing inactive and disabled accounts is crucial for network security and resource optimization. PowerShell commands like Get-ADUser and Search-ADAccount provide valuable insights into user information, last logon dates, password status, and account disablement. These commands allow administrators to identify and take appropriate actions on inactive or disabled accounts, such as disabling accounts, resetting passwords, or unlocking accounts.
Create, Copy, Configure, and Delete Users and Computers
There are two methods to do this,
– ADUC (Active Directory Users and Computers)
– ADAC (Active Directory Administrative Center)
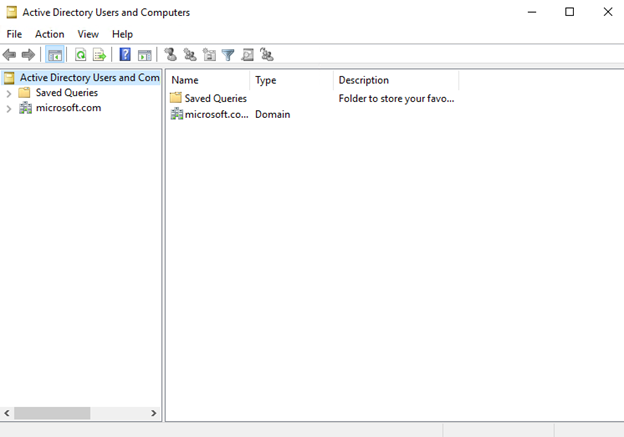
ADUC
Using GUI you can configure the user and computer accounts.
ADAC
ADAC does all the work using PowerShell in the background
For example, every action you do in ADAC GUI it is performing a POWERSHELL command to run without direct access to AD
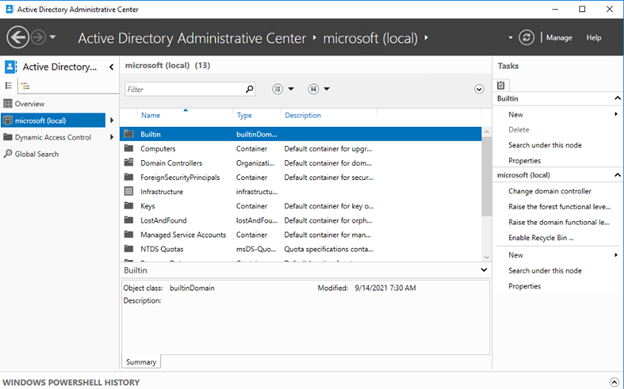
ADAC- This is how it’s done.
Automate the Creation of Active Directory Accounts
Get-ADUser
New-ADUser | Remove-ADUser
Get-ADComputer
New-ADComputer | Remove-ADComputerGet-ADUser: This command helps you get information about user accounts in Active Directory. You can find details like usernames, display names, email addresses, and group memberships.
New-ADUser: This command allows you to create new user accounts in Active Directory. You can specify usernames, passwords, display names, and where the accounts should be placed in the directory.
Remove-ADUser: This command helps you delete user accounts from Active Directory. It permanently removes the specified user accounts.
Get-ADComputer: This command helps you get information about computer accounts in Active Directory. You can find details like computer names, operating systems, IP addresses, and last logon times.
Using CLI to configure or automate AD accounts
Just an account with a name
new-aduser -Name userLDAP QUERY to put in OU
new-aduser -Name user -Surname test -Path “OU=Company Users,DC=company, DC=pri”further information
new-aduser -Name user -Surname test -Path “OU=Company Users,DC=microsoft, DC=com” -OtherAttributes@{‘title’=”user”; ‘mail’=’[email protected]’}adding password
$password=”123456A!” | ConvertTo-SecureString =AsPlaintText -Forcenew-aduser -Name user -Surname test -Path “OU=Company Users,DC=microsoft, DC=com” -OtherAttributes@{‘title’=”user”; ‘mail’=’[email protected]’} -AccountPassword $password -ChangePasswordAtLogon $true -Enabled $truePerform Bulk Active Directory Operations
OBJECT = COMPUTERS,GROUPS,USERS and more
ATTRITUBTES = DETAILS ON THOSE OBJECTS
csvde = tool used to export and import in Active Directory
csvde -f output.csvThis will acc generate a csv file that contents all the objects and attributes in active directory
ldifde = responds and work on idif, format LDIF directory exchange
dsadd = to add in computers, groups and more
dsmod = to adjust existing objects
Use can use CSV file to add users to active directory
You can get my source code in GitHub
$import = Import-csv -Path”c:\import.csv”
$import
$ou = “OU=Company Users,DC=microsoft, DC=com”
foreach ($user in $import) {
$password = $user.password | ConvertTo-SecureString =AsPlaintText -Force
New-ADUser -Name $user.name -GivenName $user.firstname -Surname $user.lastname -path $ou -AccountPassword $password -OtherAttributes@{{‘title’=$user.title; ‘mail’= $user.mail}} -ChangePasswordAtLogon $true -Enabled $true}New Users will be CREATED
We can even do Changing accounts or disabling accounts or even settings passwords
- Get-ADUser -Filter {title -eq ‘engineer’} | set-aduser -company “New Company”
- Get-ADUser -Filter {title -eq ‘engineer’} | Disable-ADAccountWe can even filter to identify set of users and then pipe that information into an entire diff cmdlet to perform some tasks.
Manage Inactive and Disabled Accounts
To get all the information about the user
- Get-ADUser -filter*
To get the last logon date
- Get-ADUser -filter* -Properties lastlogondate | ft name, lastlogondate
Even you can get the last time the password was reset
- Get-ADUser -filter* -Properties lastlogondate,passwordlastset | ft name, lastlogondate,passwordlastset
To check the disable accounts
- Get-ADUser -filter{enabled -ne $true}
To get the names of accounts
- Get-ADUser -filter{enabled -ne $true} | ft name
Shows all the information about disabled accounts
- Search-ADAccount -AccountDisabled
Only shows the name list of disabled accounts
- Search-ADAccount -AccountDisabled | ft name
Filter it with only user accounts not any other accounts like computers
- Search-ADAccount -AccountDisabled -usersonly| ft name
More PowerShell commands.
Inactive accounts period of 30days and pipe into names
- Search-ADAccount -AccountInactive -TimeSpan 30.00:00:00 | ft name
Abouts PASSWORDS
- Search-ADAccount -PasswordExpired
- Search-ADAccount -PasswordNeverExpire
- Search-ADAccount -LockedOut | ft name
Automate Unlocking of Disabled Accounts
To unlock accounts
– help Unlock-ADAccount
Select Group Policy Management
Domains
microsoft.com
Default Domain Policy — right click EDIT
Select Computer Configuration
Windows Settings
Security Settings
Account Policies
Account Lockout Policies
So Basically, These Three means,
- Account Lockout Duration means when a user enters a wrong password for specific times and how many minutes will they be logout from domain.
- Account lockout threshold means the times a user can enter wrong password and the account will be logon
- Reset account is like if user types incorrect password for 5 times in 30mins then they will be logout
For Automate Password Resets
Select Group Policy Management
Domains
microsoft.com
Default Domain Policy — right click EDIT
Select Computer Configuration
Windows Settings
Security Settings
Account Policies
Password Policy
Implement Offline Domain Join
This is a rare activity to attach a computer to active directory that doesn’t have network access to that active directory.
first you must create a file in the server which has AD
- djoin /provision /domain company.pri /machine server1 /savefile c:\server1.txt
we now have to transfer this file to the machine
now in machine
- djoin /requestodj /loadfile c:\server1.txt /windowspath c:\windows /localos
- shutdown /r /t 0
Manage Default Active Directory Containers
To delete OUs, you must go ADUC and VIEW and ADVANCED FEATURES
and go to properties of OU you want to delete and select objects
To create OUs
– New-ADOrganizationalUnit “microsoft Computers”
This will now redirect all new users into that location
– redirusr /?
– redirusr “OU=Company Users, DC=microsoft, DC=com”
Redirects new computers into that location
– redircmp “OU=Company Users, DC=microsoft, DC=com”
(ONLY WORK WITH NEWLY CREATED USERS AND COMPUTERS)
Understand Group Types and Scopes
GROUP TYPES
- Security Groups
- Distribution Groups
Security groups are used for granting access to resources such as SharePoint sites.
Distribution groups are used for sending email notifications to a group of people.
GROUP SCOPES
- Global Groups
- Domain Local Groups
- Universal Group
- Domain Local groups accept user accounts from any domain
- Universal groups accept user/computer accounts from any domain
- Global group can also be nested within a Universal group
- A Universal group can be nested within another Universal group or Domain Local group in any domain
- Universal Groups are visible throughout the forest and can contain accounts global groups and another universal group from any domain forest
Group Membership Management Using Windows PowerShell
Get-ADGroup | Set-ADGroup
New-ADGroup | Remove-ADGroup
Get-ADGroupMember
Add-ADGroupMember
New-ADGroup -Name “Untrust Users” -GroupScope Global -Path”OU=Company Users, DC=microsoft, DC=com”
Add-ADGroupMember “Untrust Users” djones,john
Get-ADGroupMember “Untrust Users”
Managed by Tab gives convolutes to update the membership list of existing groups to manage the group and give user to permission.
Group Nesting
Users go in Global Groups
Global Groups go in Domain Local Groups
Assign Permissions to Domain Local Groups
we do this because presents a way in multi domain environment to provide access to users outside the domain
In single DC you don’t need these domain local groups or global groups nesting’s
Global Groups can contain
Global Groups from their domain
Domain Local Groups can contain
Domain Local Groups From their domain
Global Groups from trusted domains and any domain in the forest
Universal Groups from trusted domains and any domain in the forest
Universal Groups can contain
Global Groups from any domain in the forest
Universal Groups from any domain in the forest
Enumerate Group Membership
situation where wrong people get access to wrong groups
to check the group what has inside
– Get-ADGroupmember “Highly Sensitive Access” | ft name
To check where the user in which groups
– Get-ADcomncipalGroupMembership john | ft name
This will provide a list of all the users through their group membership who have access to this highly sensitive information
– Get-ADUser -Filter ‘memberof -recursivematch’ “ cn=Highly Sensitive Access, ou=company users,dc=microsoft,dc=com”’ |ft name
Convert Groups
You can do this using GUI
Domain local groups and global groups can be converted to universal groups.
Universal groups can be converted to domain local groups or global groups.
Domain local groups cannot be converted to global groups.
Global groups cannot be converted to domain local groups.
WITH POWERSHELL
- New-ADGroup “My Universal Distribution Group”
paremeter — global - Get-ADGroup “My Universal Distribution Group” | Set-ADGroup -GroupScope Universal
- Get-ADGroup “My Universal Distribution Group” | Set-ADGroup -GroupCategory 0
0 means Distribution
Delegate Active Directory Groups and OUs
If you don’t want to be the only person managing groups in your Active Directory Domain.
ADUC
Using Delegation of control wizard
BY VIEW
ADVANCED FEATURE
And select the OU you want to Delegate then abilities to add and remove groups for the special users
Right click and select delegation control
AND USING THE WIZARD YOU CAN DO THE DELEGATION
YOU CAN CHECK IT THROUGH PROPERTIES OF OU.
Conclusion
In conclusion, efficiently managing user and computer accounts in Active Directory is essential for maintaining a well-organized and secure network. By utilizing tools like ADUC and ADAC, administrators can easily create, configure, and delete accounts. Additionally, PowerShell commands enable automation and bulk operations, streamlining the management process. By effectively managing accounts, organizations can enhance security, optimize resource allocation, and ensure smooth network operations.

