Table of Content
- Introduction BeyondTrust
- Key features of BeyondTrust PAM
- Gartner Magic Quadrant 2022
- Overview of Password Safe
- Dashboard
- Assets
- Password Safe Configuration
Introduction
BeyondTrust Privileged Access Management (PAM) is a solution that helps organizations to secure, manage, and monitor privileged access to sensitive systems, data, and applications. PAM provides a centralized, secure platform for controlling and monitoring privileged access, which helps organizations to reduce the risk of security breaches, meet regulatory compliance requirements, and improve overall security.
At its core, PAM provides a set of powerful tools for controlling privileged access, including password vaulting, session management, and multi-factor authentication. This makes it easy for organizations to securely store and manage privileged credentials, and to monitor and control access to sensitive systems and applications.
One of the key benefits of BeyondTrust PAM is its ability to integrate with a wide range of systems and applications, including on-premise systems, cloud-based services, and legacy systems. This provides organizations with a single platform for managing and controlling privileged access, and helps to reduce the risk of security breaches.
Another benefit of BeyondTrust PAM is its ability to automate many of the routine tasks associated with managing privileged access, such as password rotation and account provisioning. This helps to reduce the time and effort required to manage privileged access, and enables organizations to focus on more strategic and creative work.
One of the key use cases for BeyondTrust PAM is to secure and manage privileged access to critical systems, such as databases and servers. This helps to reduce the risk of security breaches and to ensure that sensitive data is protected.
Setting up BeyondTrust PAM is straightforward, and can be done in just a few steps. First, organizations need to install the PAM solution on their systems and configure it to meet their specific needs. Next, they need to define the policies and procedures for managing privileged access, including setting up roles and permissions, and configuring authentication methods.
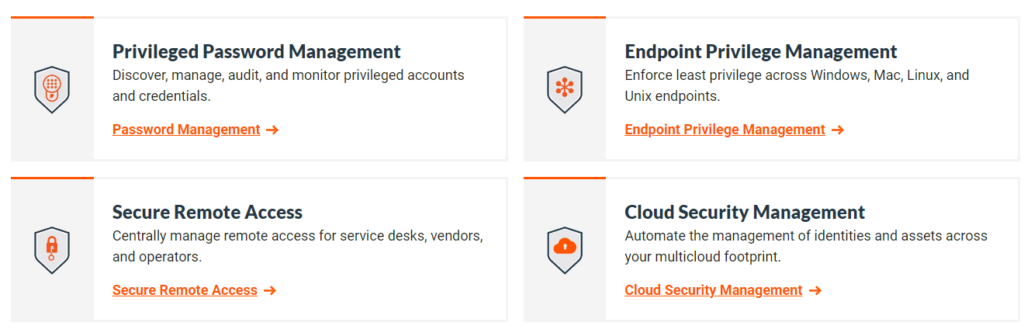
Key features of BeyondTrust PAM
BeyondTrust PAM (Privileged Access Management) is a comprehensive security solution that provides organizations with a wide range of features to manage and secure privileged access effectively. Some of the key features of BeyondTrust PAM include:
- Password Management: BeyondTrust PAM offers a centralized password management solution that ensures all privileged accounts have strong and unique passwords that are rotated regularly.
- Session Recording: The platform records all privileged sessions, including keystrokes and commands, providing complete visibility and accountability of all activities.
- Privileged Session Management: BeyondTrust PAM provides granular control over privileged sessions, including real-time monitoring, session termination, and advanced access controls.
- Multi-Factor Authentication: BeyondTrust PAM supports multiple authentication methods, including biometrics, smart cards, and one-time passwords, to ensure secure access to privileged accounts.
- Privileged Elevation: BeyondTrust PAM allows users to request temporary elevated privileges for specific tasks, providing just-in-time access to privileged accounts.
- Application Control: BeyondTrust PAM enables organizations to control and monitor the use of applications by privileged users, ensuring only authorized applications are used.
- Threat Analytics: The platform provides advanced analytics and reporting capabilities, enabling organizations to identify and respond to potential threats in real-time.
Overall, BeyondTrust PAM offers a comprehensive suite of features that enables organizations to manage and secure privileged access effectively, reducing the risk of data breaches and cyber-attacks.
Gartner Magic Quadrant 2022
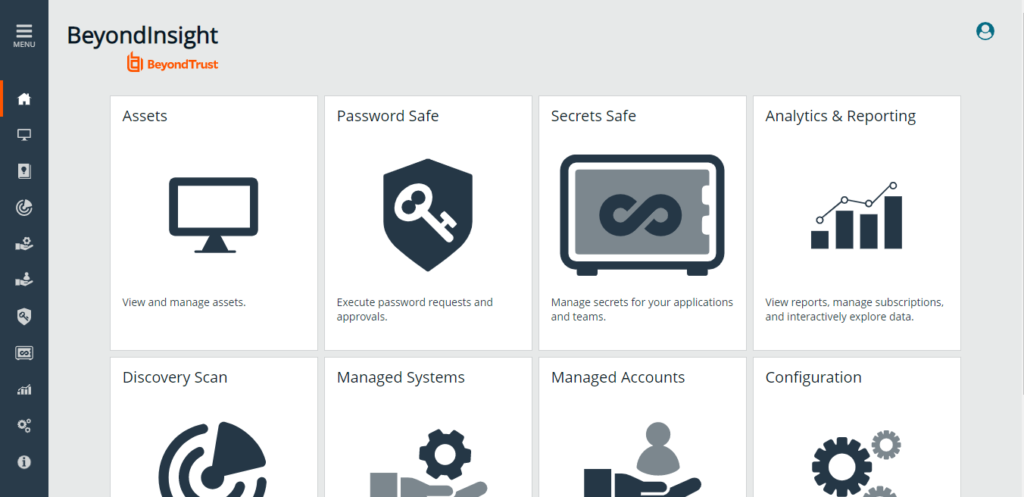
Overview of Password Safe
Dashboard
The dashboard provides an overview of the current status of the organization’s privileged access and vulnerability management, allowing users to monitor and track key performance indicators, such as the number of privileged accounts, the number of vulnerabilities, and the status of security patches.
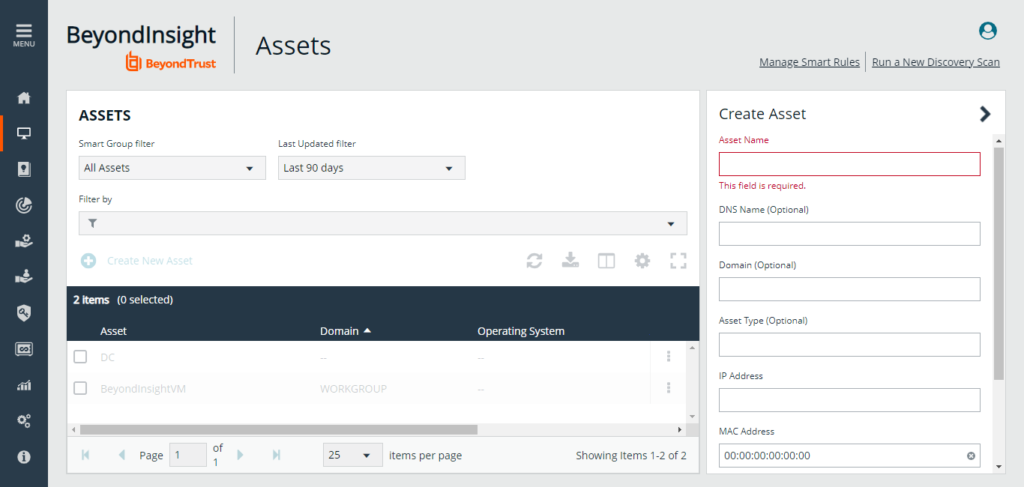
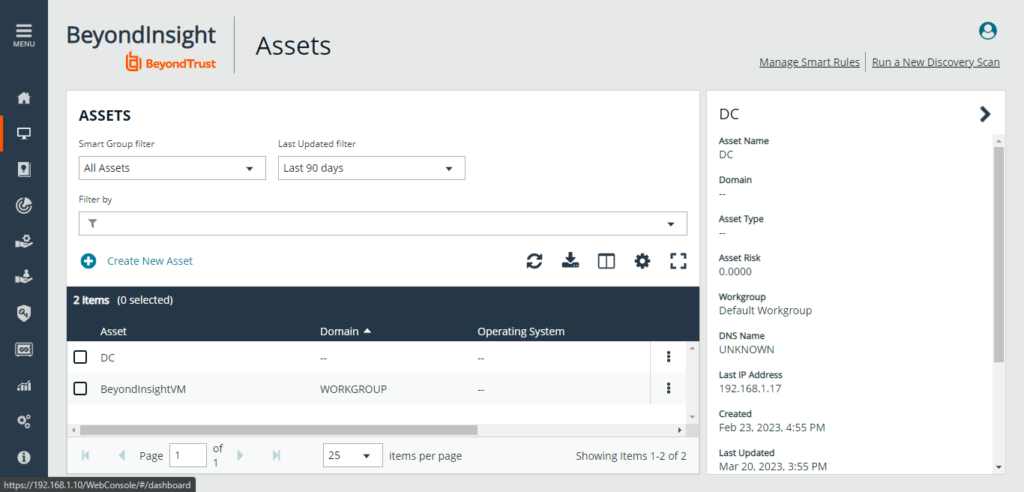
Assets
On this page, administrators can add, remove, or modify assets, such as servers, workstations, and network devices, as well as define asset groups for easier management. They can also assign specific users or groups with privileged access to those assets, define access rules, and configure automated workflows for asset management tasks.
The Assets Configuration page also enables administrators to configure various asset-related settings, such as asset discovery schedules, asset scanning options, and vulnerability assessment settings. Additionally, it provides real-time visibility into the status of asset scans and vulnerability assessments, allowing administrators to identify and remediate vulnerabilities quickly and efficiently.
Password Safe
Password Safe is a password management solution available in the BeyondTrust Dashboard. It allows you to securely store and manage passwords for different applications, systems, and websites, as well as share passwords with authorized users.
Some key features of Password Safe include:
- Secure password storage: Password Safe encrypts and stores passwords in a centralized location, so you don’t have to remember them or write them down.
- Password sharing: Password Safe allows authorized users to share passwords with each other without revealing the password itself.
- Password rotation: Password Safe can automatically change passwords on a regular basis to ensure maximum security.
- Role-based access control: Password Safe allows you to control who has access to specific passwords based on their role or permissions.
- Audit trail: Password Safe provides a detailed audit trail of all password activity, including who accessed passwords and when.
Secrets Safe
Secrets Safe is a secure vault available in the BeyondTrust Dashboard that allows you to store and manage sensitive data, such as API keys, certificates, and other secrets. It provides a centralized location to store secrets and manage access to them, reducing the risk of unauthorized access or data breaches.
Analytics & Reporting
Analytics & Reporting is a feature available in the BeyondTrust Dashboard that allows you to generate reports and analyze data related to privileged access and identity management. It provides insights into user activity, access requests, and other key metrics, helping you to identify potential security risks and compliance issues.
Some key features of Analytics & Reporting include:
Discovery Scan
Discovery Scan is a feature available in the BeyondTrust Dashboard that allows you to discover and inventory devices and systems across your network. It provides a comprehensive view of your network assets, including servers, workstations, and network devices, helping you to identify potential security risks and ensure compliance with regulations and standards.
Managed System
Managed System is a feature available in the BeyondTrust Dashboard that allows you to manage and control access to privileged accounts on your systems and applications. It provides a centralized location to manage and monitor privileged access, reducing the risk of unauthorized access or data breaches.
Managed Accounts
Managed Accounts is a feature available in the BeyondTrust Dashboard that allows you to manage and control access to privileged accounts. It provides a centralized location to manage and monitor privileged access, reducing the risk of unauthorized access or data breaches.
Configuration
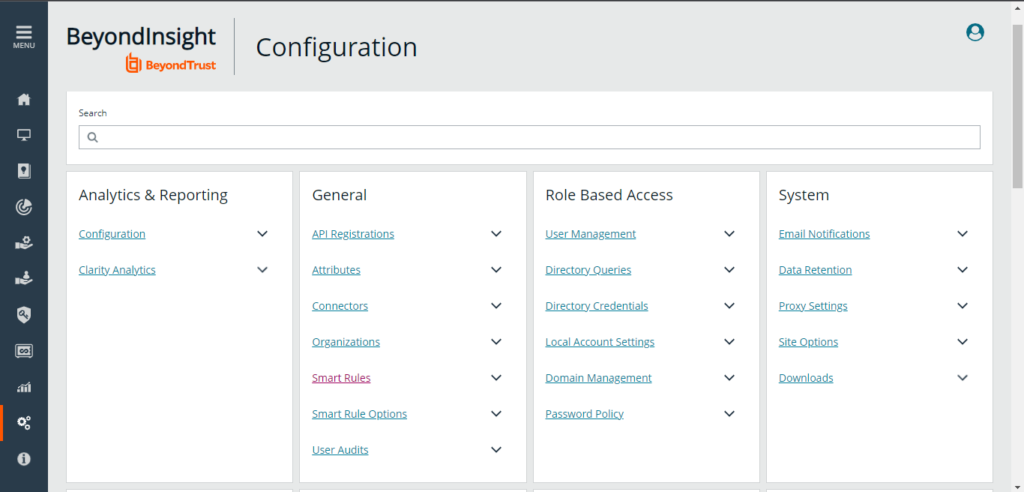
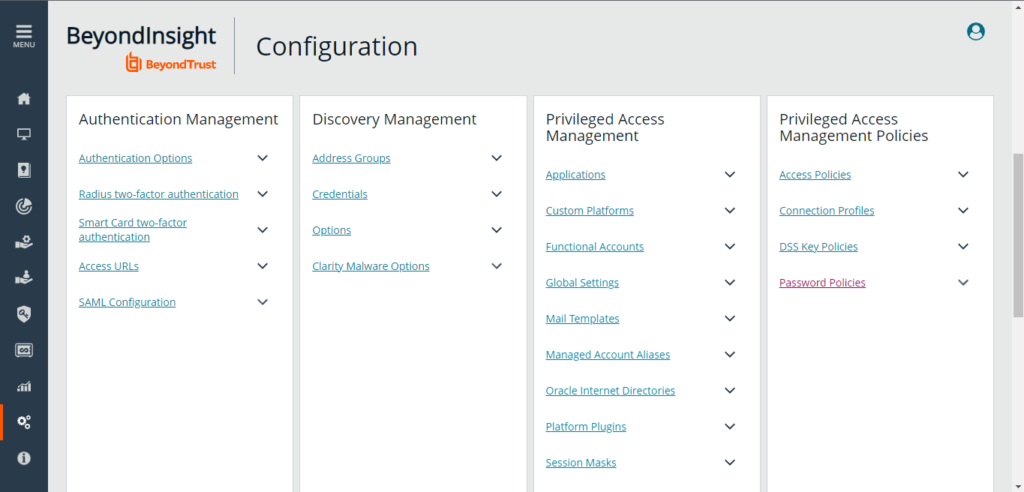
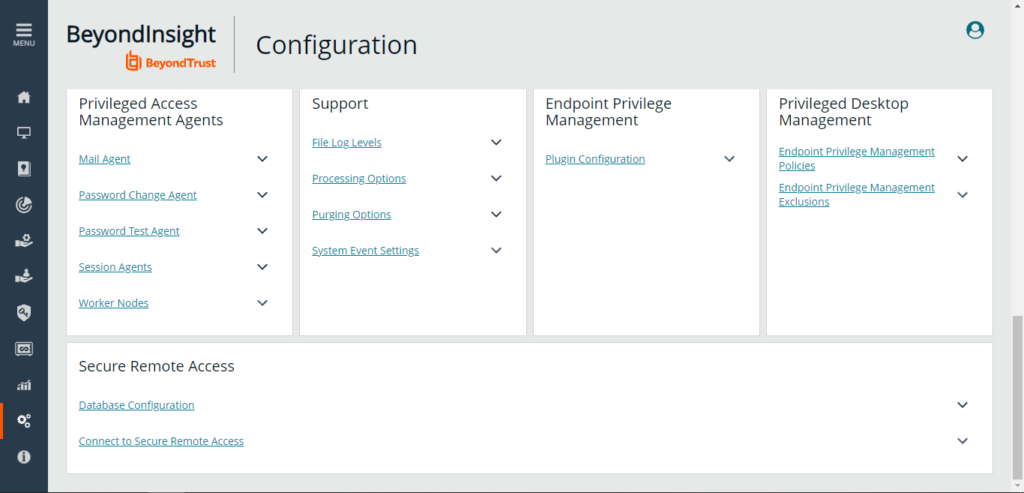
Conclusion
In conclusion, BeyondTrust is a comprehensive security solution that provides organizations with the tools to manage and secure their digital assets effectively. The platform offers a range of features such as privileged access management, vulnerability management, and endpoint protection, all of which are crucial in today’s rapidly evolving threat landscape.
BeyondTrust’s unified approach to security allows businesses to streamline their security operations, reduce complexity, and mitigate risks effectively. Additionally, the platform is highly customizable and can be tailored to meet the specific needs of each organization.
Overall, BeyondTrust is a powerful tool that enables organizations to secure their critical assets and minimize the risk of data breaches and cyber-attacks. As businesses continue to rely more on technology to drive growth, BeyondTrust is a valuable investment in ensuring the safety and security of their digital ecosystem.