Introduction
AlienVault OTX is a platform that provides threat intelligence capabilities. Before establishing a connection between AlienVault OTX and Microsoft Sentinel using the Data Connector, it is necessary to obtain API access from AlienVault OTX. By following the steps outlined below, you can seamlessly connect the two platforms and enhance your organization’s threat intelligence capabilities.
AlienVault OTX
We need to obtain API access from AlienVault OTX before connecting both via Data Connector
- Create an Account on the AlienVault and Log in using your Credentials
- Navigate to the API Integration

- Right Side of the page you can see Direct Connect API Usage.
- Copy the “Your OTX Key”
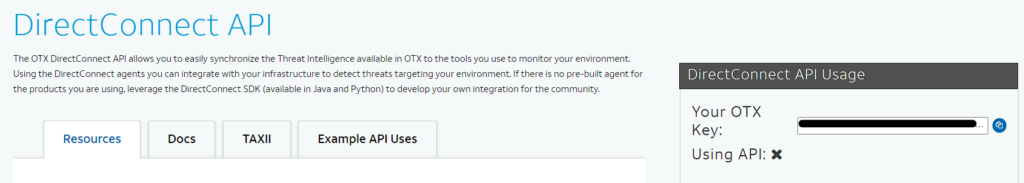
Make sure to securely store the generated API key or access token as it will be required during the configuration steps in Microsoft Sentinel.
Once you fulfill this prerequisite and acquire the required API access from AlienVault OTX, you will be prepared to establish a smooth connection between AlienVault OTX and Microsoft Sentinel, enhancing your threat intelligence capabilities.
Data Connectors
After successfully integrating Microsoft Sentinel with a Log Analytics Workspace, the subsequent essential task is to set up a data feed. Microsoft Sentinel provides a range of options for transmitting data into the platform, offering flexibility and adaptability. These options encompass:
- Service-to-Service Connectors
- Out-of-the-Box Connectors
By utilizing these various approaches, you can establish a consistent and dependable data stream into Microsoft Sentinel, enabling comprehensive threat detection and response capabilities within your organization. All these options can be accessed from the Data connector section of Sentinel’s dashboard.
All Data Connectors and additional out-of-the-box (OOTB) content are now centrally available in Content hub. Starting Q2 2023 only in-use Data Connectors will be available in this gallery. The “Next steps” tab in the Data Connectors experience is removed and replaced with Content hub “Manage” experience. Learn more about the OOTB content centralization changes.
Service-to-Service Connectors:
The Service Connector is specifically designed to provide convenience for users. To establish a connection, three essential parameters are necessary: a target service instance, the authentication type between the compute service and the target service, and your application client type. Developers have the option to create connections using either the Azure CLI or the guided experience offered by the Azure portal.
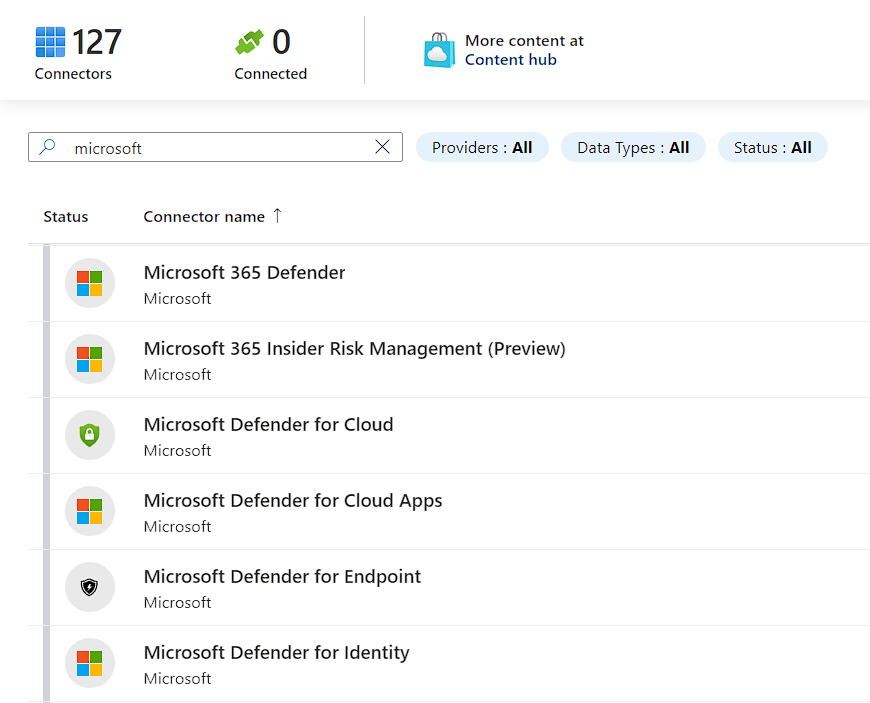
Out-of-the-Box Connectors:
The Microsoft Sentinel content hub enables discovery and on-demand installation of out-of-the-box (OOTB) content and solutions in a single step. Previously, some of this OOTB content existed only in various gallery sections of Microsoft Sentinel. Now, all of the following gallery content templates are available in the content hub as standalone items or as part of packaged solutions.
Soon this page will only show the list of in-use data connectors. For more information on this upcoming change, see Out-of-the-box content centralization changes
Enable a data connector
On the Data connectors page, choose or search the desired active or custom connector you wish to connect with, and click on “Open connector page.”
If the desired data connector is not visible, you can install the associated solution from the Content Hub.
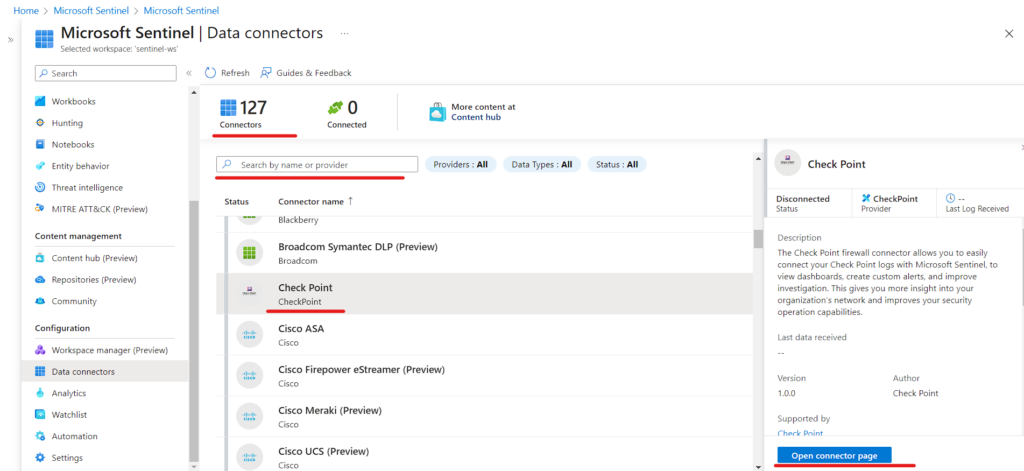
You have completed all the prerequisites mentioned in the Instructions tab, the connector page will provide instructions on how to ingest the data into Microsoft Sentinel. Please note that it may take some time for the data to begin arriving.
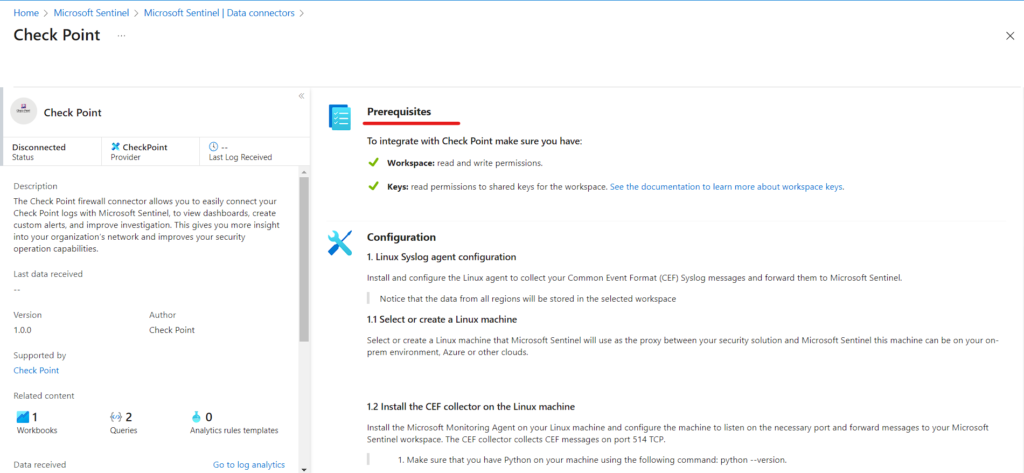
Upon successful connection, you will be able to view a summary of the data in the “Data received” graph, along with the connectivity status of the data types.
Prerequisites
- You must have read and write permissions to the Microsoft Sentinel workspace to store your threat indicators.
- You must have a TAXII 2.0 or TAXII 2.1 API Root URI and Collection ID.
TAXII server API Root and Collection ID
TAXII 2.x servers advertise API Roots, which are URLs that host Collections of threat intelligence. You can usually find the API Root and the Collection ID in the documentation pages of the threat intelligence provider hosting the TAXII server.
Threat intelligence — TAXII connector for Microsoft Sentinel
- Discover TAXII server collections
- Enable TAXII data connector in Azure Sentinel for each collection
Microsoft Sentinel provides seamless integration with TAXII 2.0 and 2.1 data sources, enabling advanced functionalities in monitoring, alerting, and threat hunting utilizing your threat intelligence. With the utilization of the TAXII connector, effortlessly transmit threat indicators from TAXII servers to Microsoft Sentinel. These essential threat indicators encompass a diverse array of data, including IP addresses, domains, URLs, and file hashes.
To activate the TAXII data connector for Threat Intelligence in Microsoft Sentinel, adhere to the following instructions:
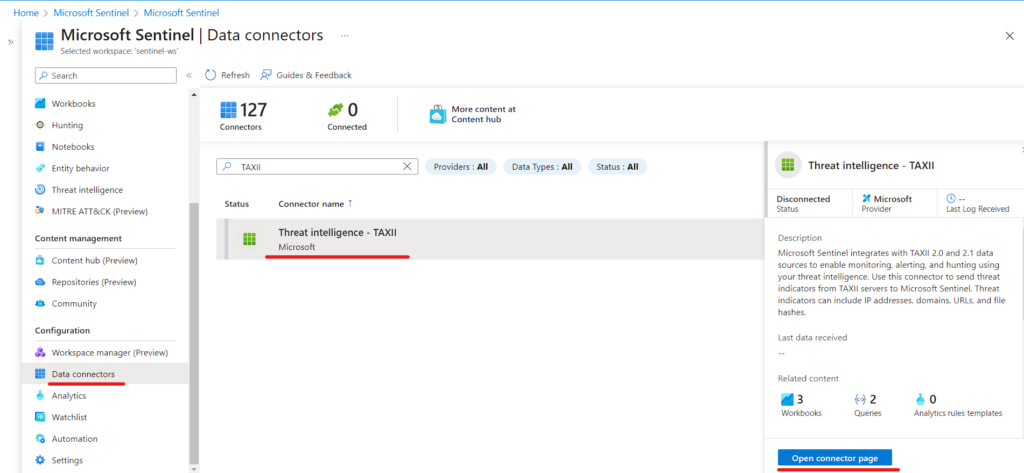
- Access the available connectors by clicking on “Data connectors”.
- Locate and select the “Threat intelligence — TAXII” connector by scrolling down or using the search function.
- Proceed with the configuration by clicking on the “Open connector page” button. Scroll down to reach the configuration section.
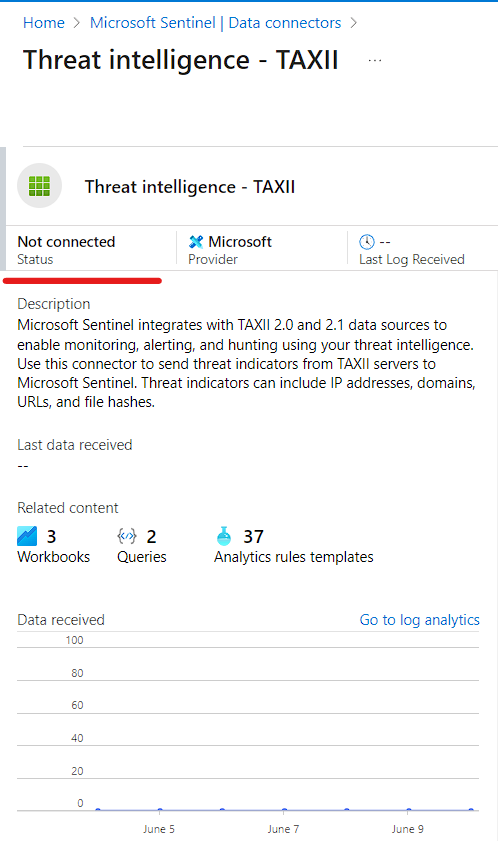
- The TAXII is not connected and check the Prerequisites
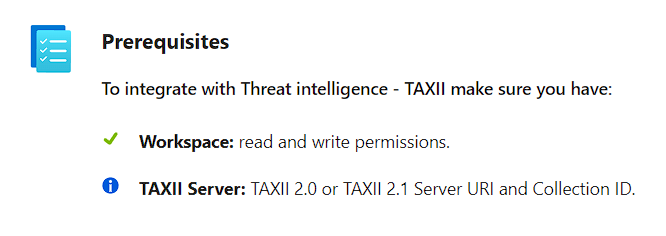
- Fill in the required details, such as the connector name and description.
- Enter a friendly name for this TAXII server Collection, the API Root URL, the Collection ID, a Username (if required), and a Password (if required), and choose the group of indicators and the polling frequency you want. Select the Add button.
Friendly name (for server): Give a Suitable Name
API root URL: Default URL -> https://otx.alienvault.com/taxii/root
Collection ID: Default ID -> user_AlienVault
Username: Leave it blank
Password: Leave it blank
Indicators: To import the Data
Note: If you subscribed to API usage, please use them to fill the collection ID and Username.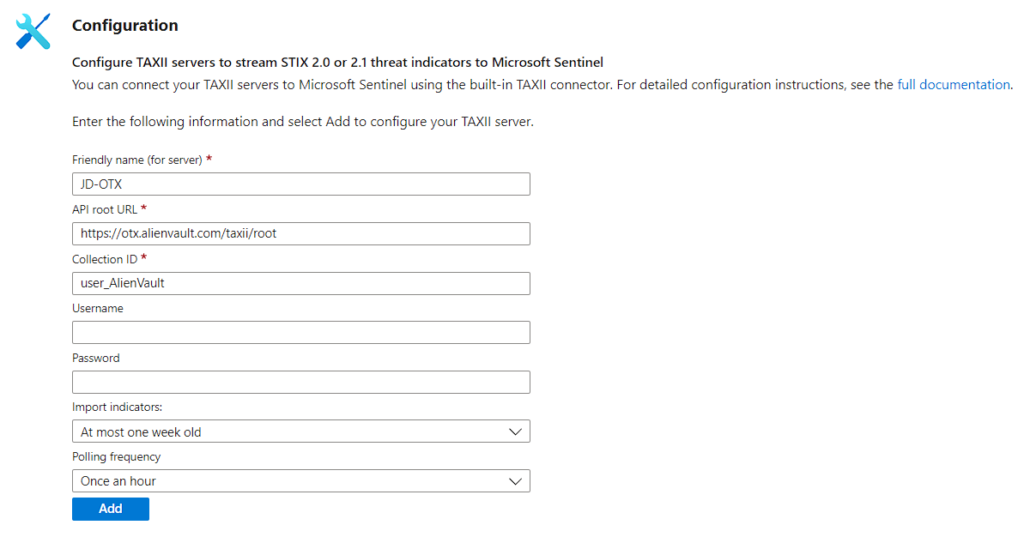
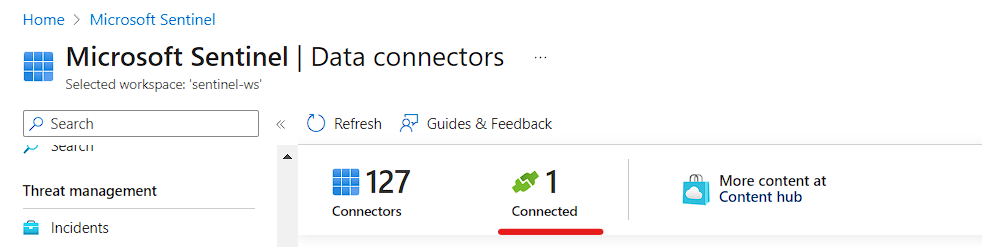
- In the Data Connectors you can see the Connected has been 1

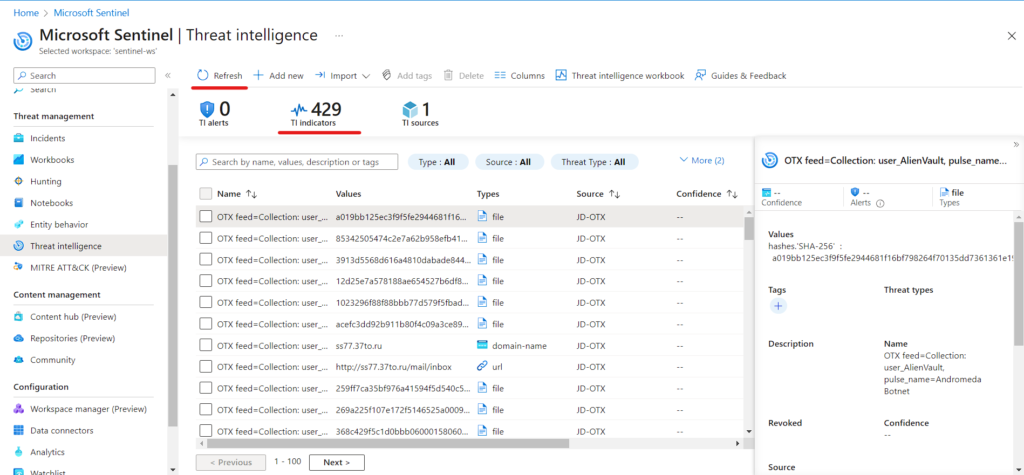
- Now let’s visit to Threat management → Threat Intelligence and click “refresh” to see indicators data loaded.
Understand threat intelligence in Microsoft Sentinel
Conclusion
Microsoft Sentinel provides different ways to bring in data and improve threat intelligence capabilities. These include Service-to-Service Connectors and Out-of-the-Box Connectors that you can find in the Data connector section of the Sentinel dashboard. By using these options, you can make sure that data flows smoothly into Microsoft Sentinel, helping you detect and respond to threats effectively. Just follow the instructions given to enable and set up the connectors you need. Once they’re connected, you can keep an eye on the data you receive and check if the connection is working well through the Sentinel dashboard. It’s worth mentioning that Microsoft Sentinel can also work seamlessly with TAXII 2.0 and 2.1 data sources. This means you can send important threat indicators from TAXII servers to make your threat intelligence even stronger.

