Table of Content
- Introduction Cynet
- Installation
- Dashboard Overview
- Alerts
- Cynet EDR Remediation
- Alerts on email
- Integration
- Conclusion
Introduction
Cynet is a cybersecurity company that provides a comprehensive platform for threat detection, incident response, and threat prevention. The company’s platform integrates with various security tools and technologies to provide organizations with a unified view of their security posture.
Cynet’s platform uses artificial intelligence and machine learning algorithms to automatically detect and respond to security threats in real-time. The platform can also be configured to prevent attacks before they occur, reducing the risk of data breaches and minimizing the impact of security incidents.
With its user-friendly interface and intuitive workflows, Cynet’s platform is designed to make it easy for security teams to manage and respond to security incidents. The company also offers 24/7 support and expert services to help organizations maximize the effectiveness of their security strategies.
Endpoint security based on SaaS refers to a type of cybersecurity solution that is delivered and managed remotely through a software as a service (SaaS) model. This means that the software is hosted on remote servers and accessed through the internet, rather than being installed on local devices or networks. The main objective of endpoint security SaaS is to protect endpoint devices such as laptops, smartphones, and tablets from various types of cyber threats such as malware, viruses, and hacking attempts. It typically includes features such as antivirus and anti-malware protection, firewall, intrusion detection and prevention, and device control. This type of solution can be particularly beneficial for organizations that have a large number of remote workers or that have limited IT resources.
Installation
There’s certain deployment option available. Let’s install Single Agent on Windows 10.
Cynet Distribution Tool
The Cynet agent can be installed using the Cynet installer, using MSI Installer, or via the Command Line.
- From the bottom of the left navigation pane, click Install.
- Select Cynet Distribution Tool.
An installation file is downloaded to your computer. - Click the downloaded file.
- Follow the instructions in the Installation Wizard.
The Cynet agent is installed on the endpoint, which is added to the default Group – Manually Installed Agents.
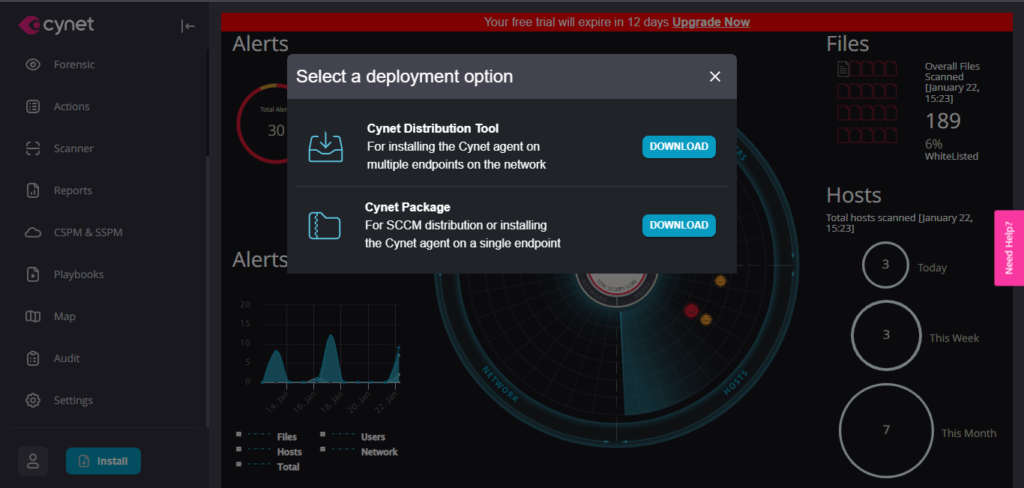
Cynet Package
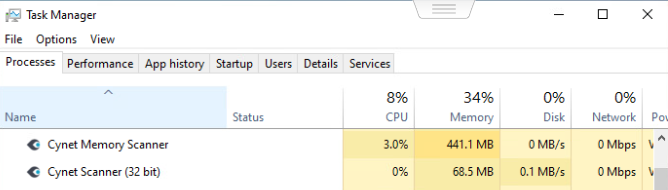
And to make sure the agent is running you can check through the task manager
Dashboard Overview
Cynet is a SaaS XDR which has – NGAV, EDR, NDR and DECEPTION with affordable Licensing prices.
Cynet configurations are managed per Scan Group. Use Scan Groups to separate scan settings between subnets, computer types, and departments. Every host in your network must be associated to a Scan Group.
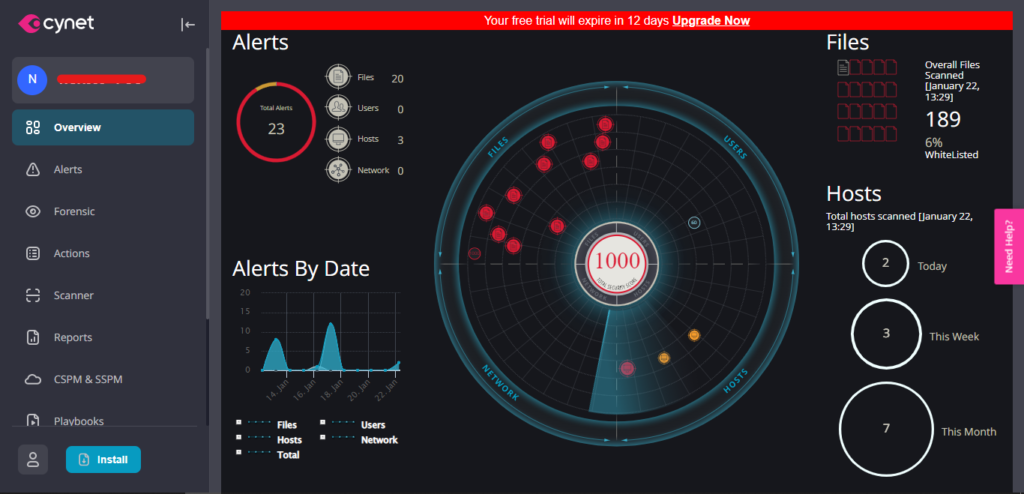
Alerts
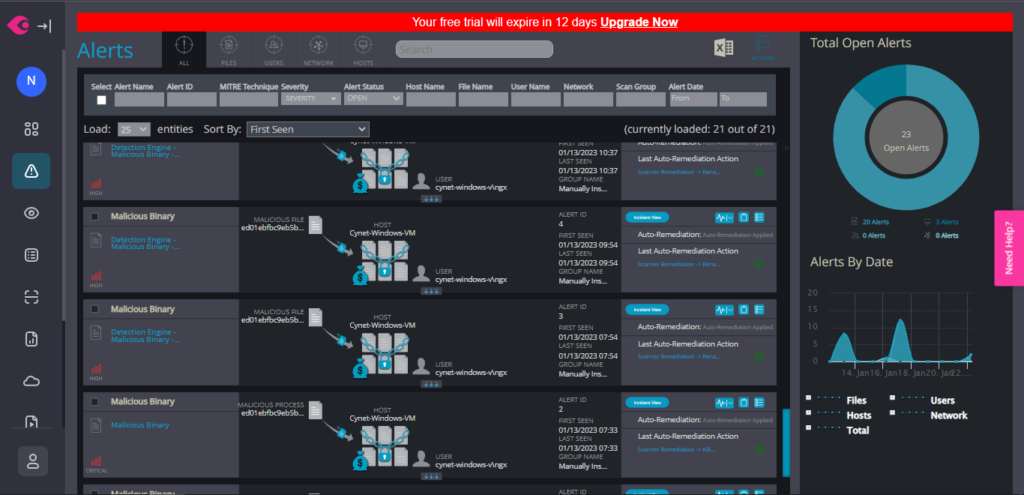
An important component of an EDR system is the ability to generate alerts when it detects suspicious activity. These alerts can be used to notify security personnel of potential threats, so they can take action to investigate and mitigate them. Alerts can be generated based on various types of events, such as unusual network traffic, changes to files or registry keys, or the execution of malicious code.
Here we have executed malware in windows 10 Virtual Machine and the alerts has been triggered.
Windows 10 PC
Malware can cause a range of problems, including data loss, system crashes, and unauthorized access to sensitive information.
For testing purpose or education purpose you can download free malware in google. It’s on your own risk to you those malwares, so please be careful when playing with them.
Now Let’s execute the malware .exe file.
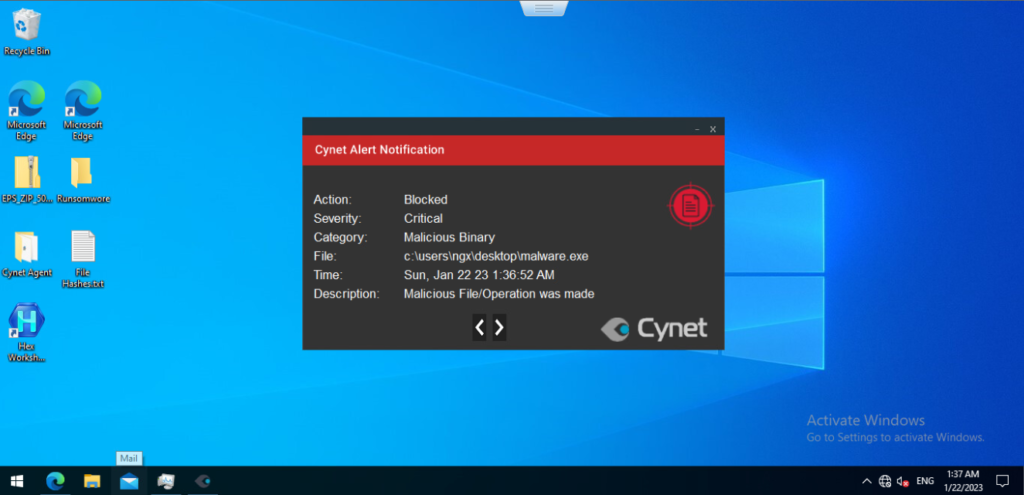
After Executing the file we can see the Cynet Alert Notification dialog box appears.
The Action has been BLOCKED and few more information regarding the execution process.
Since we used Openly available malware which can be detected as we know. So that I even changed the hashes of those malware but the Cynet has blocked it.
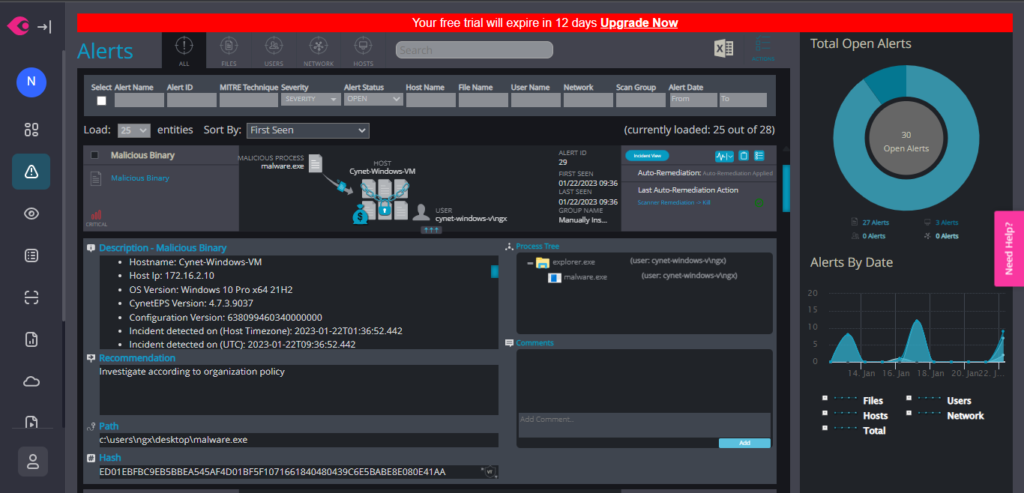
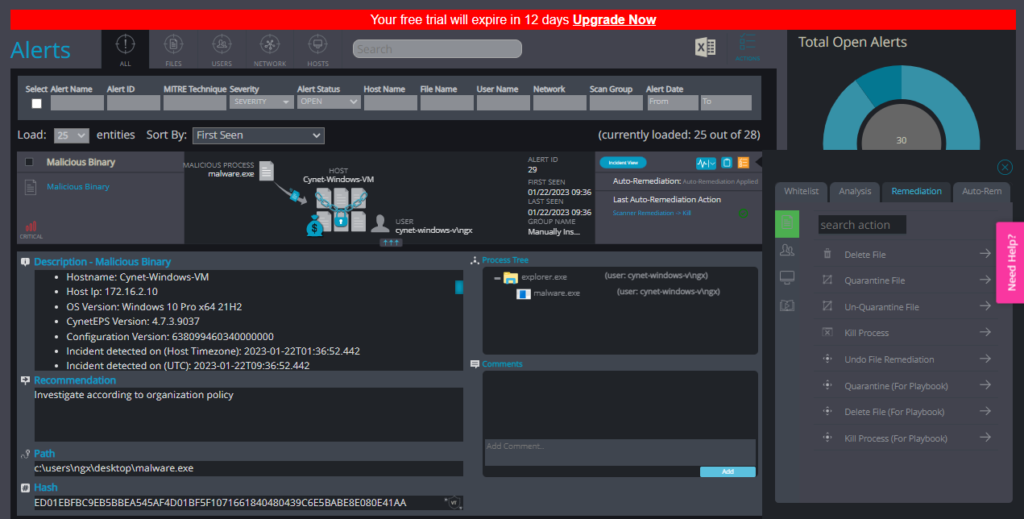
Now we can get a full view of the malware in the Alerts.
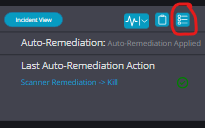
Cynet EDR Remediation
Cynet EDR can be used to remediate malware and other types of security threats on a computer or network. Once an EDR system generates an alert indicating that a threat has been detected, security personnel can use the system’s built-in tools to investigate and take action to remove the threat.
Remediation actions can include:
- Quarantine or isolating the infected endpoint to prevent further spread of the malware
- Killing or terminating the malicious process
- Uninstalling or removing the malware from the endpoint
- Restoring the endpoint to a previous, clean state using a backup or snapshot
- Updating the endpoint software and security configurations to prevent future infections
It’s important to note that EDR systems may require a combination of different remediation actions to completely remove malware from a system. Additionally, it’s important to investigate the cause of the infection, so the same vulnerabilities won’t be exploited again in the future.
Alerts on email
Email alerts are notifications that are sent to one or more email addresses when a specific event or condition occurs. These alerts can be used to notify individuals or teams of important information, such as security breaches, system failures, or critical thresholds being met.
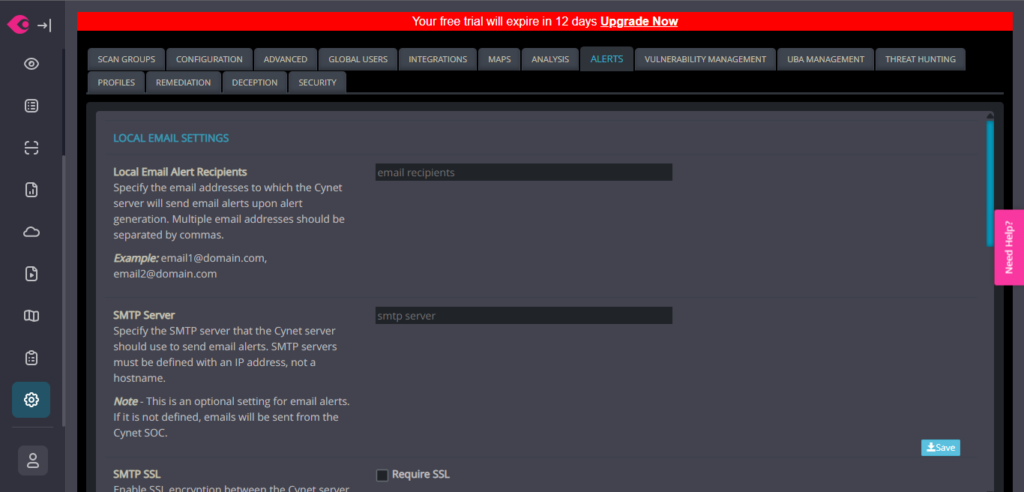
- Navigate to Settings > Alerts > Local Email Settings.
- Enter the email addresses, separated by a comma, to which Cynet 360 must forward alerts.
- Enter the IP address of the SMTP server from which to send the emails. If you do not specify an SMPT server, the emails are sent from the Cynet SOC.
- If you specified an SMTP server, you can enable SSL encryption between Cynet and SMTP servers. To do so, select the Require SSL check box.
- Enter an email address that will appear as the sender.
- Navigate to Email Alert Filter Settings at the bottom of the page.
- Select the minimum alert severity level for sending it by email. Alerts with severity level lower than specified are not sent.
- Click Save.Alert emailing is configured.
It’s important to note that Email alerts should be configured carefully, to avoid overloading the recipients with too many notifications. Also, the alerts should be specific, actionable, and include enough information to help recipients understand the cause of the alert and take appropriate action.
Integration
Cynet’s integration with apps and SaaS (Software as a Service) solutions allows organizations to protect their data and systems in the cloud. The Cynet 360 platform can integrate with popular SaaS applications, such as Office 365 and G Suite, to provide comprehensive protection for email and other cloud-based services.
The platform can also integrate with popular apps and services, such as AWS, Azure and Google Cloud, to provide visibility and protection for cloud infrastructure and workloads. This includes identifying and blocking malicious activity, monitoring user behavior, and protecting against data exfiltration.
Additionally, Cynet can also integrate with many endpoint security solutions, such as antivirus, EDR (Endpoint Detection and Response), and Mobile Device Management (MDM) solutions. This integration allows Cynet to gather data from endpoints and provide advanced threat detection and response capabilities across the entire organization.
Overall, Cynet’s integration capabilities allow organizations to protect their entire environment, from endpoints to cloud infrastructure, with a single, unified platform.

Conclusion
In conclusion, endpoint security based on SaaS is a cost-effective and efficient solution for protecting endpoint devices from cyber threats. It allows organizations to have a centralized management and control over the security of their endpoints, which is especially important for organizations with a large number of remote workers or limited IT resources. By using SaaS endpoint security, an organization can be sure that their endpoint devices are protected against the latest threats, and that security patches and updates are applied in a timely manner. Additionally, SaaS endpoint security can also help organizations to comply with regulatory requirements and industry standards, which can be vital in certain industries. Overall, SaaS endpoint security is a valuable tool for any organization looking to protect their endpoint devices and data from cyber threats.

