Table of Content
- Introduction DAM
- Key features of DAM
- Architecture Imperva Data Security Fabric
- Deployment Environments
- Configuration Guide
- Dashboard
- Initial Configs
- Data Masking Configs
- Conclusion
Introduction
Imperva DAM is an advanced solution specifically designed to safeguard and monitor sensitive data within organizations. DAM, short for Data Activity Monitoring, acts as a protective shield against unauthorized access, misuse, and theft of valuable information. By implementing Imperva DAM, businesses gain a comprehensive view of data usage, enabling them to track user activities and swiftly identify any suspicious or malicious behavior in real-time. This solution offers robust security controls such as access management, encryption, and activity auditing, ensuring data confidentiality, integrity, and compliance with regulatory standards. With Imperva DAM, organizations can confidently shield their data assets, maintain a secure environment, and protect their operational integrity and reputation.
Key features of Imperva DAM
- Strong Data Protection: Imperva DAM keeps your sensitive data safe by preventing unauthorized access, leaks, and insider threats.
- Real-Time Monitoring and Alerts: It watches over your data activities in real-time, quickly alerting you if anything suspicious or harmful happens.
- Tracking User Actions: Imperva DAM keeps track of what users are doing with your data, helping you understand their behaviors, spot risky actions, and enforce rules.
- Control Access Levels: You decide who can access specific data and what they can do with it. Imperva DAM lets you set precise rules to ensure only authorized people can access your information.
- Compliance and Auditing: It helps you meet regulatory requirements by creating detailed reports and keeping a record of data access and activities for audits.
- Data Encryption: Imperva DAM adds an extra layer of protection by encrypting your data, making it unreadable to unauthorized parties.
- Integration with Existing Systems: It works seamlessly with your current security tools, so you can make the most of your existing investments and keep everything working together.
- Easy to Use: Imperva DAM has a user-friendly interface with simple dashboards and visuals, making it easy for you to monitor and manage data activities.
- Scalability and Performance: It can handle large amounts of data and work well even in high-traffic environments, ensuring it performs reliably as your needs grow.
- Stay Ahead of Threats: Imperva DAM integrates with threat intelligence sources, so you stay updated on the latest security risks and can take proactive measures to protect your data.
Architecture of Data Security Fabric
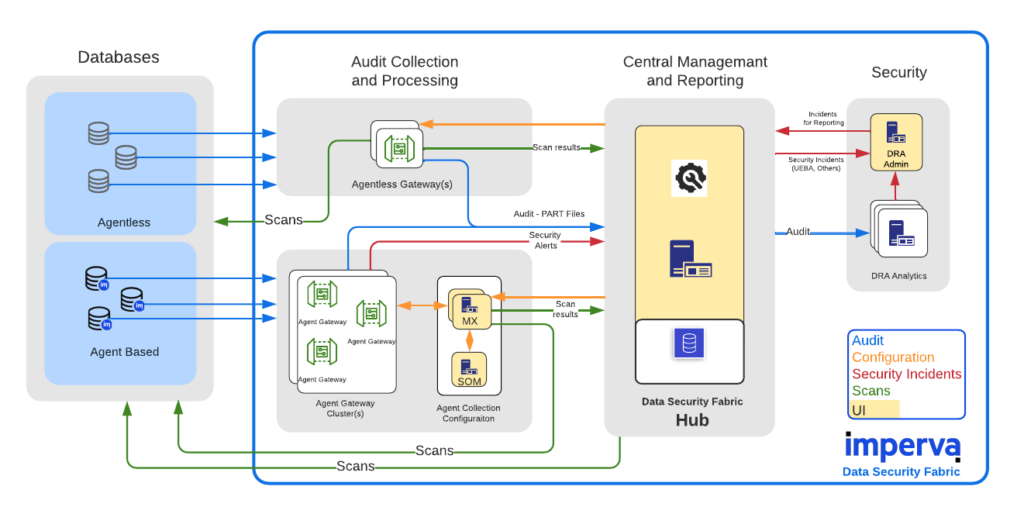
| PRODUCT | ROLE | MAIN COMPONENTS |
|---|---|---|
| DSF Hub (previously Sonar Warehouse) | A robust platform for analysis, compliance, data security, risk management, and reporting. DSF Hub stores audit data that was sent from both Agent and Agentless Gateways. The warehouse enables (through the USC = Unified Settings Console) the configuration of asset monitoring on both the Agent and Agentless Gateways. | DFP Hub |
| Agentless Gateway | ||
| Agentless Gateway (previously Sonar Gateway) | Responsible for collecting raw audit from agentless data sources, parsing, normalizing, aggregating and enriching the incoming audit information, preparing Sonar Warehouse compatible files, and sending them for ingestion on the Sonar Warehouse. | Agentless Gateway |
| Agent Gateway (previously DAM Gateways) | Responsible for collecting audit from agents that are installed on database servers, parsing, normalizing, aggregating and enriching the incoming audit information, preparing DSF Hub compatible files, and sending them for ingestion on the DSF Hub. Also responsible for discovering and assessing databases, classifying data, applying default and custom audit and security policies to protect data | Management Server (MX) |
| Agent Gateway | ||
| Database Agents | ||
| Management Server Manager (Optional) | ||
| Data Risk Analytics (DRA) | Runs advanced Analytics on audit data that is sent from the Sonar Warehouse, and provides rich actionable security incidents. | DRA Admin Server |
| DRA Analytics Server |
Deployment Environments
| PRODUCT | MAIN COMPONENTS | SUPPORTED DEPLOYMENT ENVIRONMENTS |
|---|---|---|
| Sonar | DSF Hub Agentless Gateway | Runs on any environment. For details regarding the operating system, see Supported OS in the Sonar Installation and Setup Guide. |
| DAM/DAS (Database Activity Monitoring / Discover and Assessment Server) | Management Server (MX) Agent Gateway Database Agents SOM (Optional) | Physical VMWare Hyper-V KVM Google Cloud Platform (GCP) Amazon Web Services (AWS) Microsoft Azure |
| DRA | DRA Admin Server DRA Analytics Server | VMWare Hyper-V KVM Google Cloud Platform (GCP) Amazon Web Services (AWS) Microsoft Azure |
Configuration
Let’s take a look at some configuration screenshots to get a better understanding of how Imperva DAM can be set up and customized to meet your specific needs.
Initial Configs
Setup External Authentication
Configure Site Tree
- DC Name
- Server Group
- Service object (MS SQL) = All MSSQL Servers in specific server group
- Application object = Single DB
Install Agent on Servers
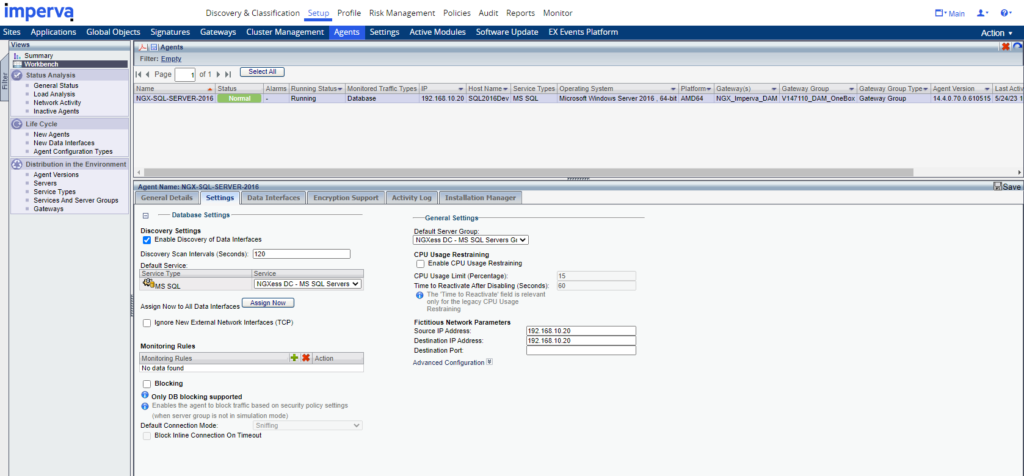
Check agent connectivity
Map Agent to site tree Service Object
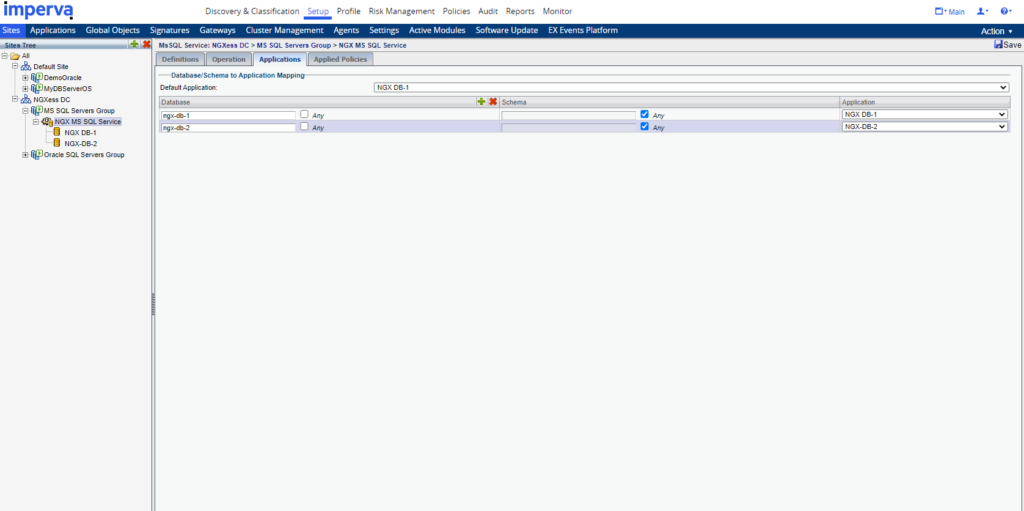
Create Application objects to represent DBs. Then configure the database to application mapping.
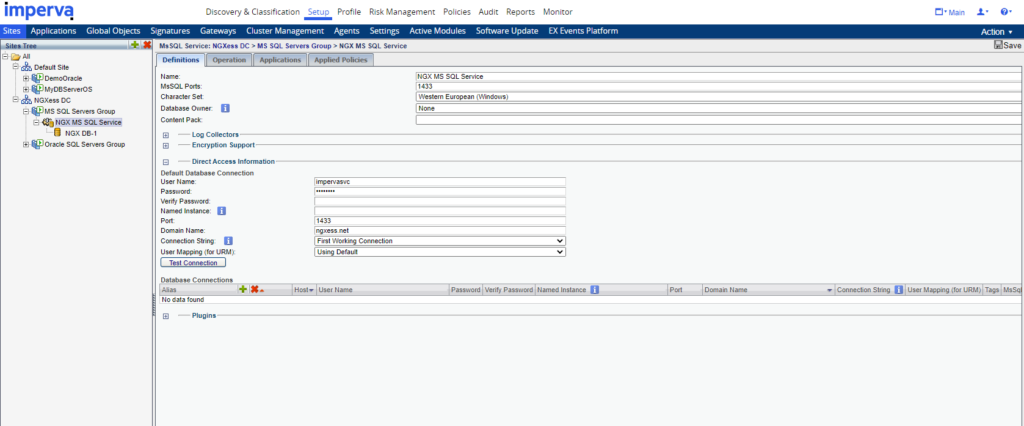
Add “Direct Access Information” to Service Object. Securesphere uses these info to access databases.
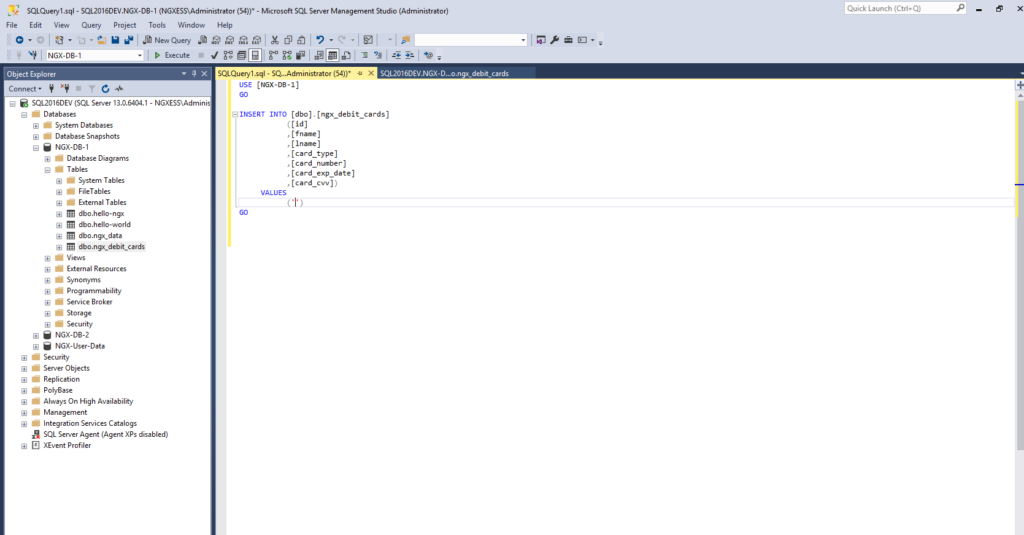
MS SQL Server
Data Masking Configs
Discovery & Classification → Scan Management → Select Scope to “Data Type Configuration”
- Configure any custom data types for our environment.
Data Masking Steps
- Configure any custom data types for our environment. [If needed]
- Create a Scan profile using one or more above data types
- Create a New Scan using above profile and schedule it
Results will appears in “Classified Database Data” window. We have to accept the results manually.
Classified tables are grouped into something called “Table Groups”. These TGs are automatically attach to Application Objects(DBs) (as sensative TGs) in site tree after we accept them.
Now SecureSphere knows which DBs contains which sensative tables.
We can check which tables are in a specific TG using Global Objects → Table Groups
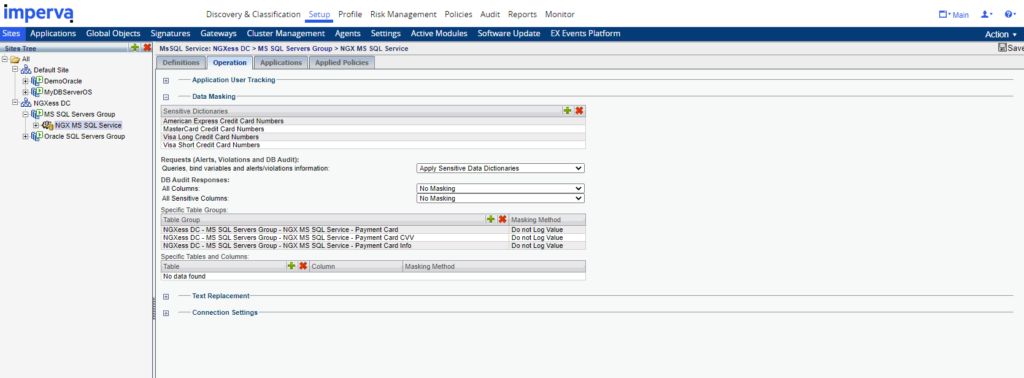
Data Masking Configs in “Operations” Tab
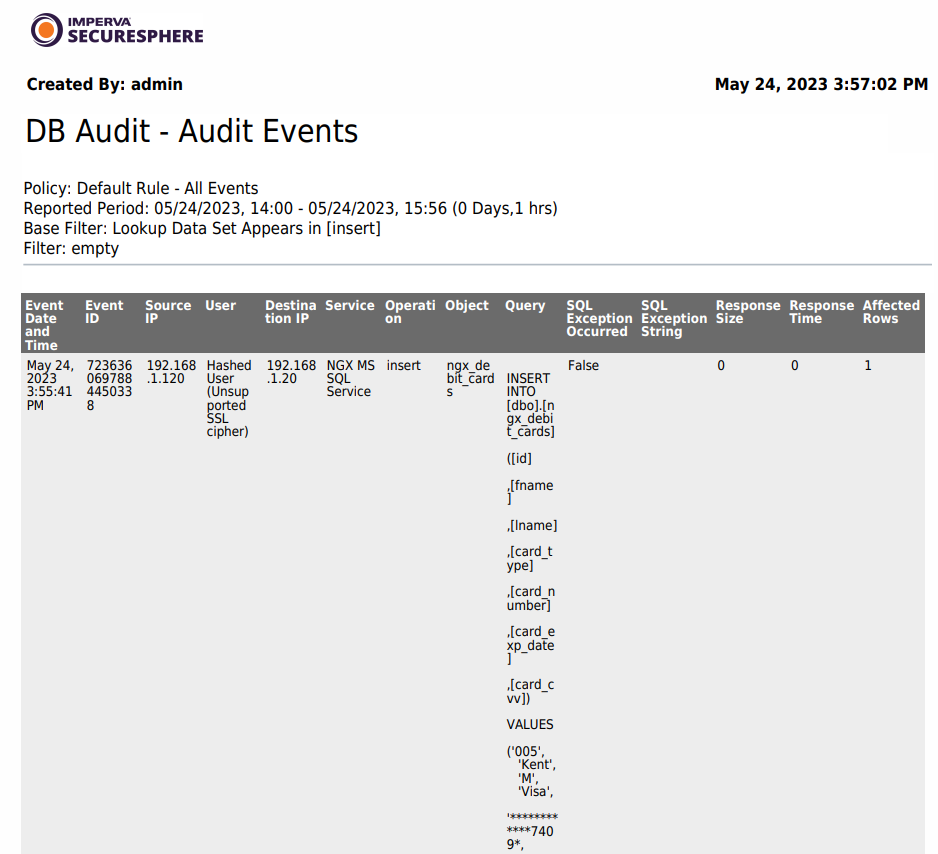
Database Audit Report after enabling Data Masking
Conclusion
In conclusion, investing in Imperva DAM is crucial for your organization’s data security and protection. By implementing Imperva DAM, you can ensure the safety of your sensitive information and prevent unauthorized access, leaks, and insider threats. With real-time monitoring and alerts, you can stay on top of any suspicious activities and take immediate action to mitigate risks. The solution allows you to track user actions, control data access levels, and meet compliance requirements, providing peace of mind and ensuring regulatory adherence. The integration with existing systems makes it easier for you to leverage your current investments and maintain a cohesive security infrastructure. With Imperva DAM, you can confidently safeguard your data, maintain a secure environment, and protect your organization’s reputation from potential data breaches and security incidents.