Multi-Factor Authentication (MFA) provides an additional layer of security to your Microsoft Azure tenant, safeguarding your sensitive data and resources. By implementing MFA, you add an extra step to the authentication process, ensuring that only authorized individuals can access your Azure services.
In this guide, we will explore the steps involved in configuring multi-factor authentication in your Azure tenant. We will explain the concept of MFA and its significance in protecting your account. By following these simple instructions, you will be able to enhance the security of your Azure environment and reduce the risk of unauthorized access.
Methods to Configure
- Conditional Access Policy
- Per User MFA
- Security Defaults
- Azure Identity Protection
Configuring Conditional Access Policy
AZURE AD PREMIUM P2
With Azure Active Directory Premium P2 you can gain access to advanced security features, richer reports and rule based assignments to applications. Your end users will benefit from self-service capabilities and customized branding.
If you haven’t already used the trial, you may consider activating Azure AD Premium P2 test this feature as well.
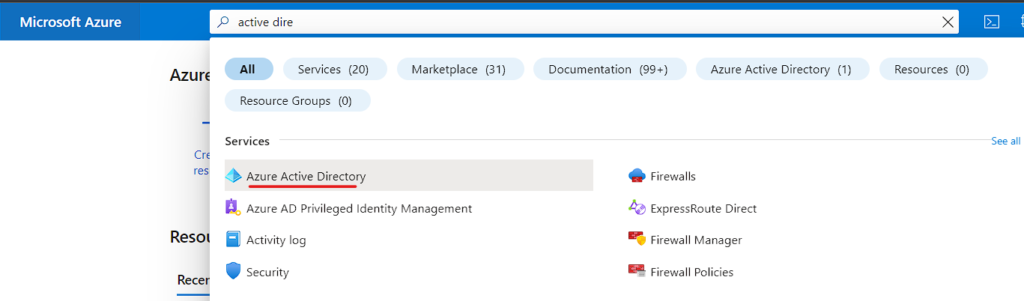
- In Azure portal search for Active Directory.
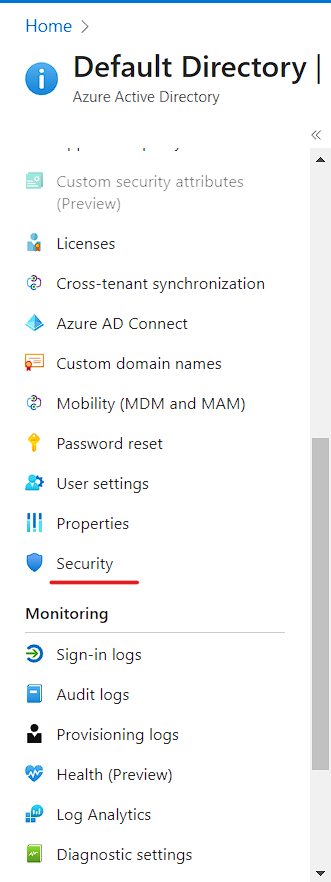
- Then scroll down and click on security option, which will navigate to the Security Dashboard.
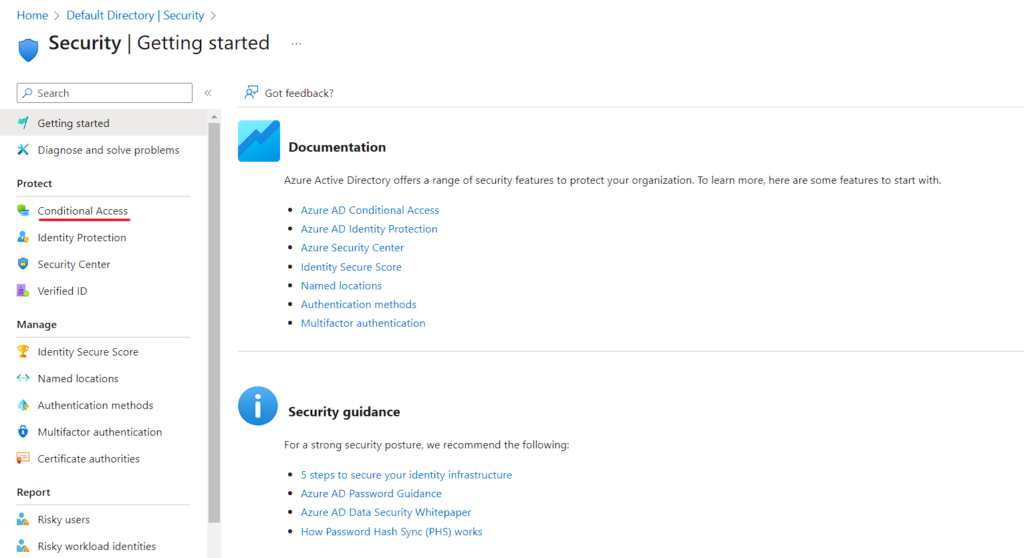
- In Security Dashboard, Scroll down and click on Conditional Policy. Which will take to the Conditional Policy Dashboard
- Conditional Policy Dashboard
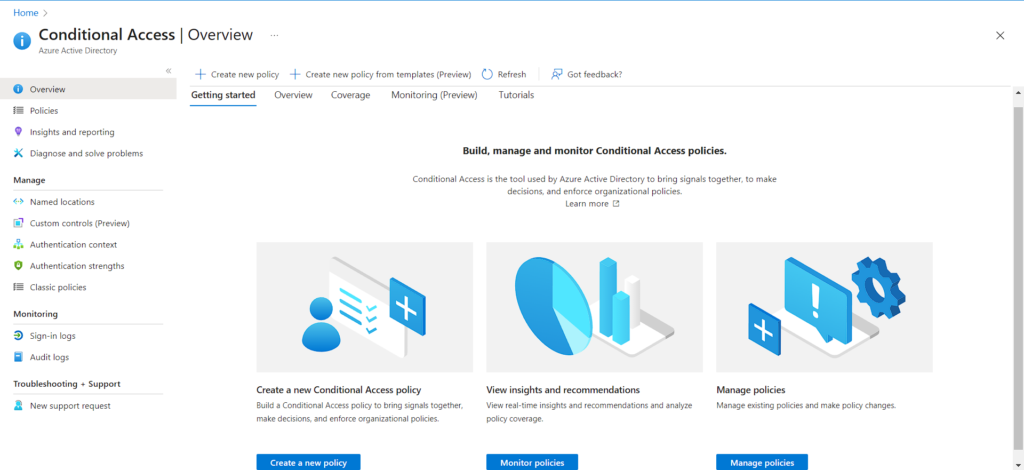
- Navigate to the Policies Tab and click on New Policy
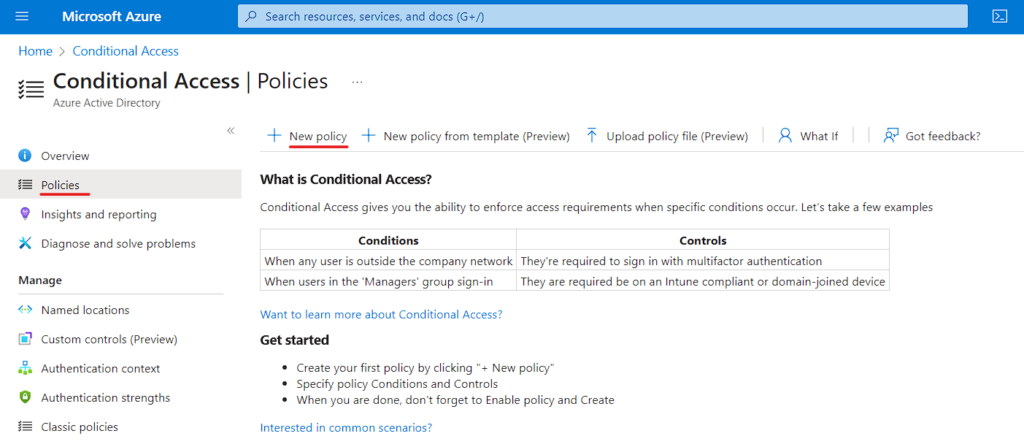
- Give an Appropriate Name to the Policy.
- Navigate to the Assignments section and Click Users -> Include-Select User and Group -> Users and Group. Then Select it in the right panel.
- This user list usually comprises the individuals that an organization intends to include in a Conditional Access policy.
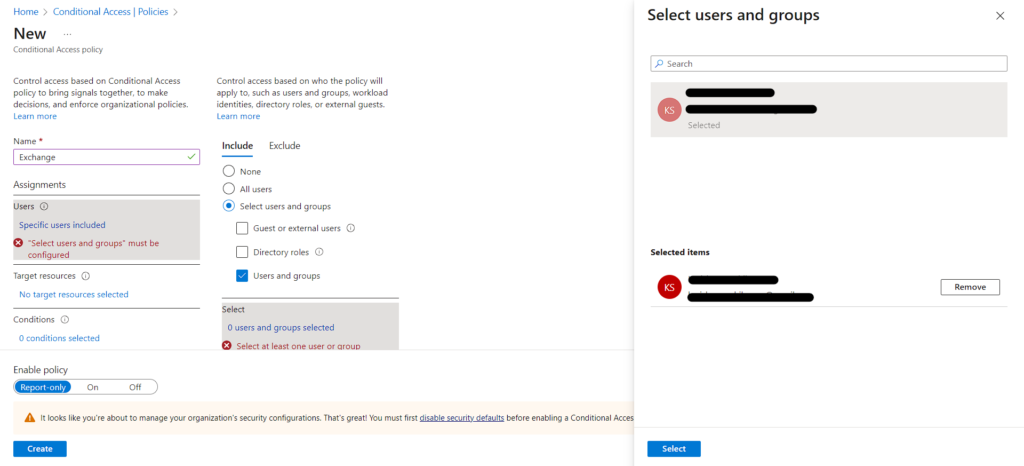
- Proceed to the Cloud apps > Include section and choose Exchange (for this Lab)to enforce MFA on Exchange.
- Under Exclude, identify and exclude any applications that do not require multifactor authentication.
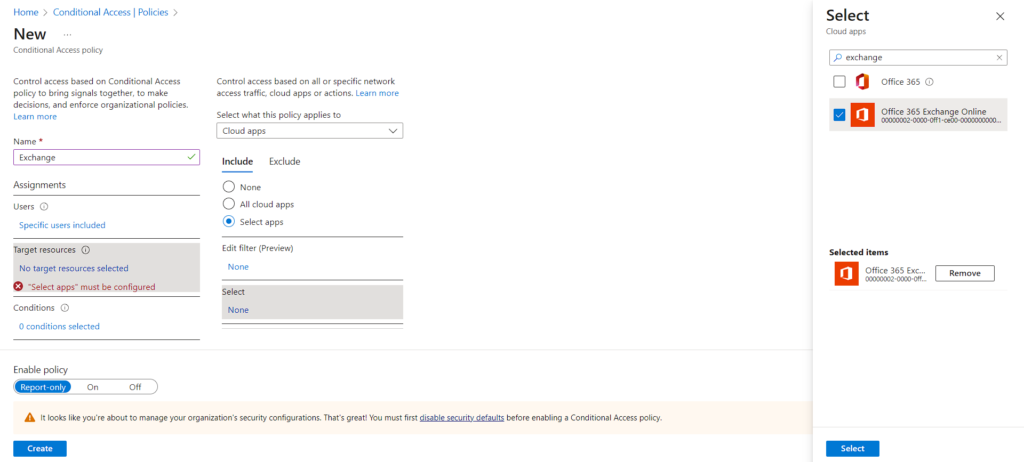
- Conditions that you can configure to apply for the user or groups.
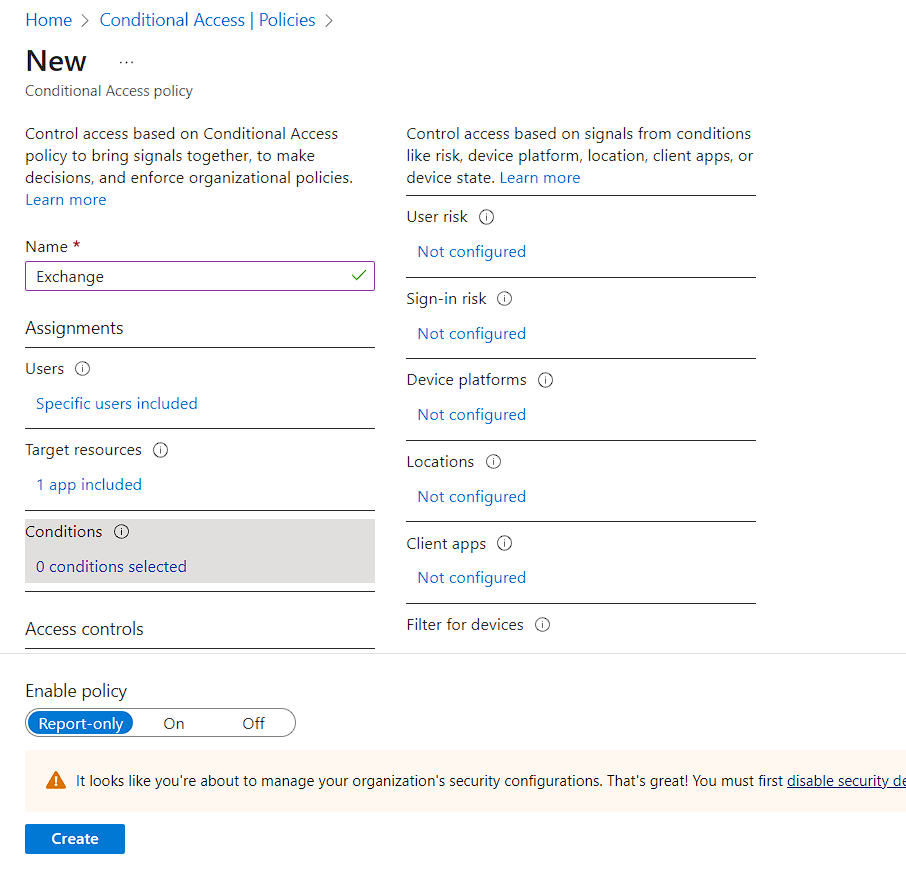
- For example if you want certain devices to apply this policy, you can select the Device Platform and this box will prompt to select.
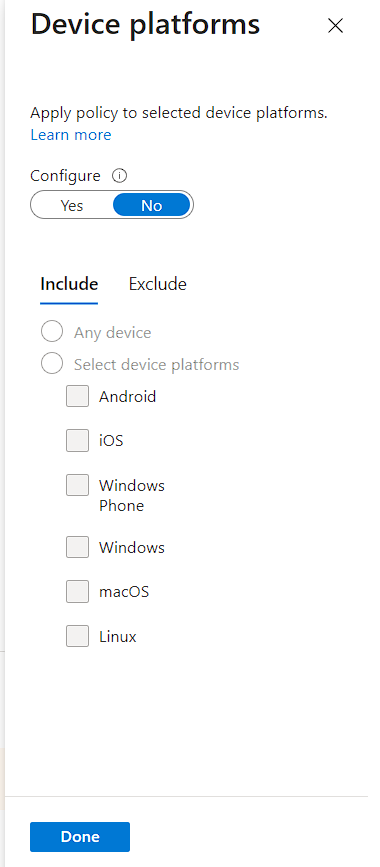
- In the Access controls > Grant section, select “Grant access” and enable “Require multifactor authentication” by selecting it.
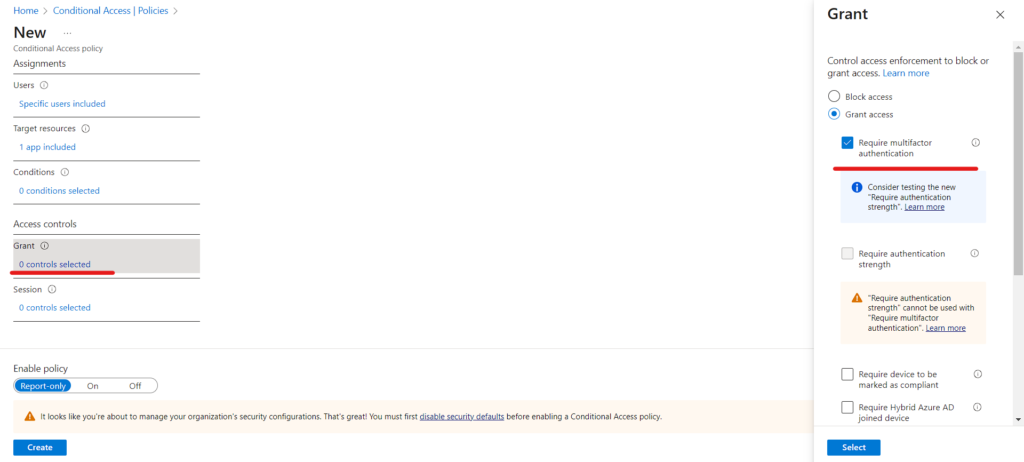
- Confirm your configuration and set the Enable policy option to “ON” for initial testing and evaluation.
- Finally, click on “Create” to enable the policy and enforce MFA according to the defined settings.
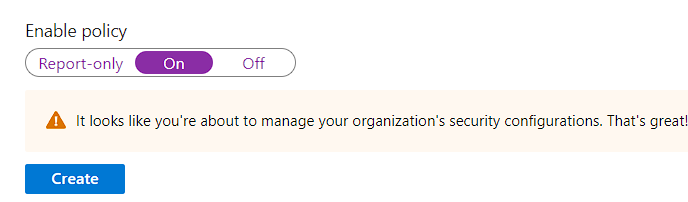
Note: It looks like you’re about to manage your organization’s security configurations. That’s great! You must first disable security defaults before enabling a Conditional Access policy.
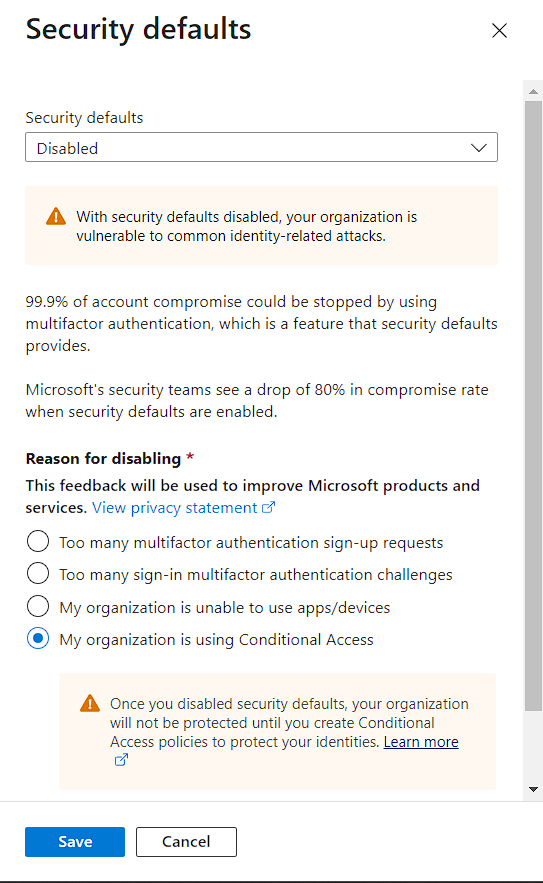
Now the MFA will be on for the selected users, group, apps or conditions.
Configuring Per User MFA
MFA will be used whenever that particular user accesses any cloud services. The license comes with Office 365 E3 and E5
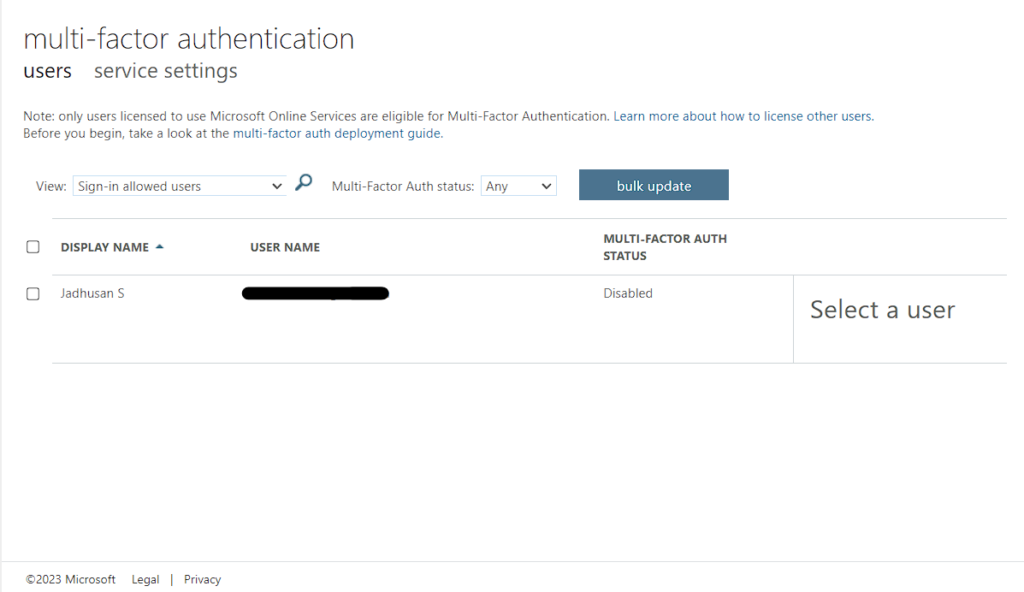
In Azure Activity Directory Select Users.
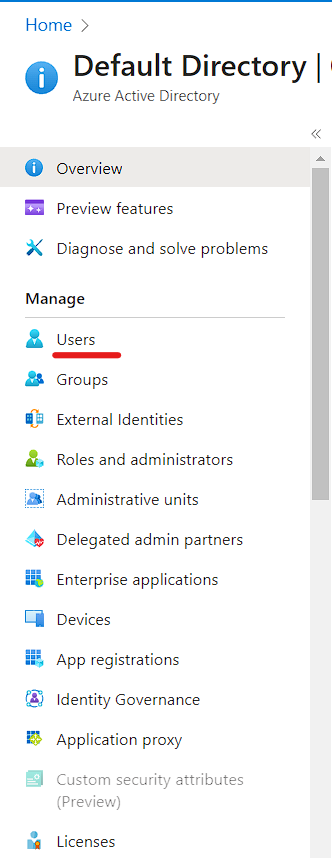
Click on Per-User MFA and it will redirect to multi-factor authentication users service settings
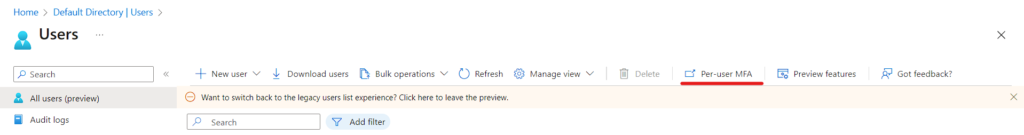
In this panel you can configure per User who needs to be assigned MFA
Configuring Security Defaults
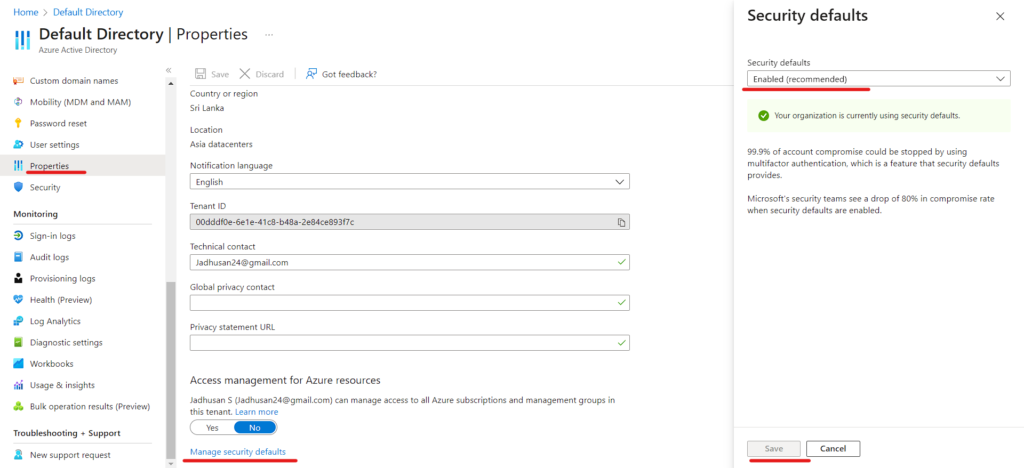
All Users in Tenant will have 14 days to register for MFA by using the Microsoft Authenticator
In Azure Activity Directory click Properties, Select Manage Security Defaults and Enable it.
Conclusion
By implementing Multi-Factor Authentication (MFA) in Microsoft Azure, you can add an extra layer of security to your tenant, protecting your sensitive data and resources. Following the steps outlined in this guide, you can configure MFA and enhance the security of your Azure environment, reducing the risk of unauthorized access.
Methods such as Azure Identity Protection, Conditional Access Policy, Security Defaults, and Azure AD Premium P2 offer advanced security features and customizable options. In the Conditional Access Policy configuration process, the user list is typically comprised of individuals targeted by the organization for inclusion in the policy. By specifying the appropriate users, selecting the relevant cloud apps, and setting access controls to require multifactor authentication, you can enable MFA for the selected users, groups, apps, or conditions.
For more undestanding – Azure Docs

