Table of Content
- Introduction Osirium
- Architecture and Component
- Key features of Osirium PAM
- Benefits of Osirium PAM
- Technical details of Osirium PAM
- Dashboard
- My Access
- My Requests
- Manage Approvals
- Change Password
- Configuration
- Manage -> User
- Manage -> Device
- Manage -> Active Directory
- Manage -> Accounts
- Conclusion
Introduction
Osirium PAM (Privileged Access Management) is a security solution that helps organizations to secure, control, and monitor access to sensitive systems and data. PAM solutions like Osirium provide a secure way to manage and control access to privileged accounts and credentials, which are often targeted by cyber attackers. It helps to reduce the risk of unauthorized access, data breaches, and cyber attacks by providing an additional layer of security around privileged accounts and credentials. Osirium PAM allows organizations to manage and monitor privileged access to systems, networks, and applications, it also allows to delegate access to privileged accounts to authorized personnel and automatically rotate credentials to reduce the risk of compromise. Osirium PAM can be integrated with other security solutions, such as SIEMs, SOCs, and MDMs, making it a versatile and flexible solution for organizations of all sizes and types.
Architecture and Component
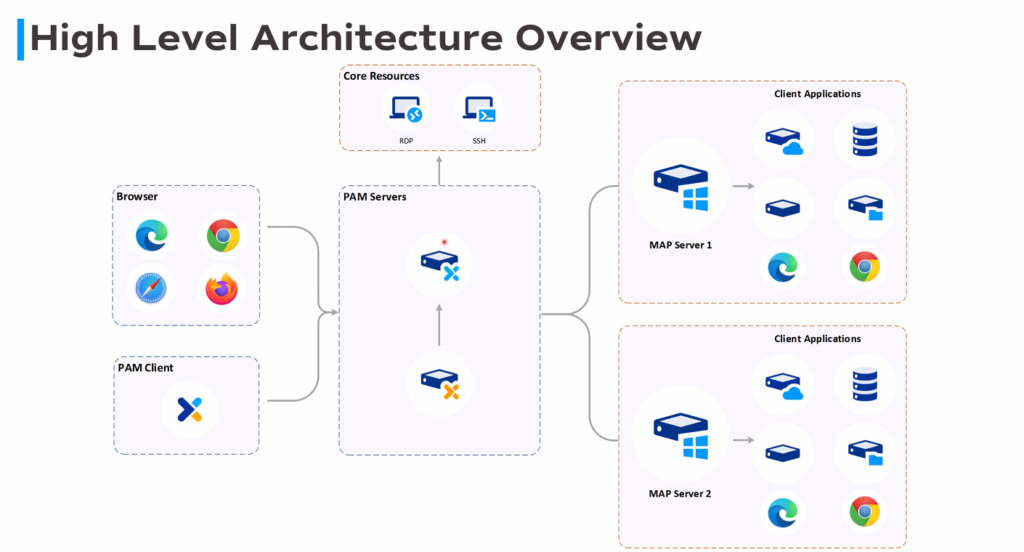
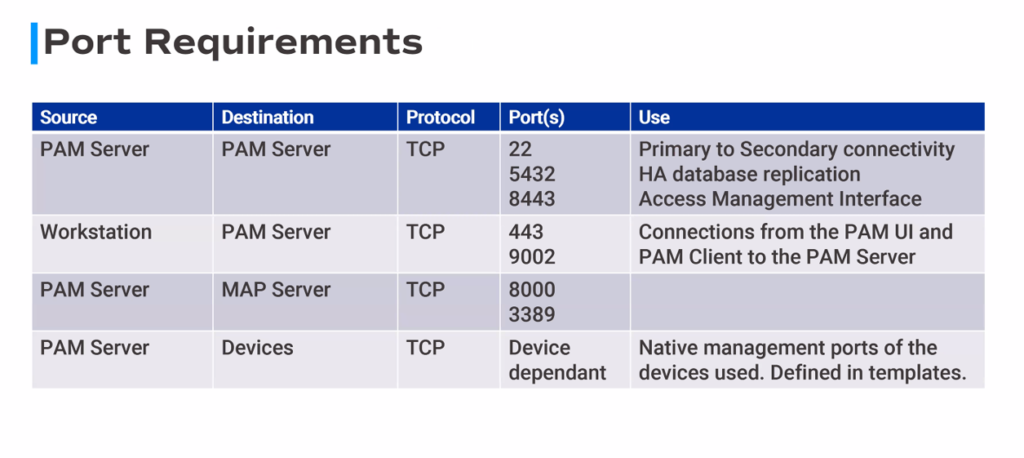
Key features of Osirium PAM
- Multi-factor authentication: Supports multiple authentication methods to ensure secure access to privileged accounts.
- Password vaulting: Securely stores and manages privileged passwords to eliminate the use of shared or static passwords.
- Session recording: Records and audits privileged sessions for compliance and security purposes.
- Role-based access control: Allows administrators to define and enforce role-based access policies.
- Single sign-on: Provides a single sign-on solution for privileged access to reduce the number of passwords that users need to remember.
- Least privilege: Implements the principle of least privilege to reduce the risk of privilege escalation and unauthorized access.
- Automated provisioning: Automates the provisioning of privileged accounts to reduce the time required for manual setup.
- Integration: Integrates with existing infrastructure and tools to streamline the management of privileged access.
- Reporting: Provides reporting and analytics to track and monitor privileged access activity.
- Threat detection: Detects and alerts on suspicious activity to quickly identify and respond to potential security threats.
Benefits of using Osirium PAM
- Enhanced security: Reduces the risk of data breaches and unauthorized access by implementing multi-factor authentication and password vaulting.
- Compliance: Supports compliance with industry regulations and standards by providing session recording and reporting.
- Streamlined access management: Simplifies the management of privileged access by providing a single sign-on solution and automated provisioning.
- Improved efficiency: Reduces the time required for manual setup and management of privileged access through automation.
- Reduced risk: Implements the principle of least privilege to reduce the risk of privilege escalation and unauthorized access.
- Integration: Integrates with existing infrastructure and tools to streamline the management of privileged access.
- Threat detection: Detects and alerts on suspicious activity to quickly identify and respond to potential security threats.
- Increased visibility: Provides reporting and analytics to track and monitor privileged access activity.
- Customization: Allows administrators to customize access policies and authentication methods to meet specific organizational requirements.
- Scalability: Scalable solution that can be deployed across a large enterprise with multiple systems and platforms.
Technical details of Osirium PAM
- Architecture: Osirium PAM is a cloud-based or on-premise solution that can be deployed in a variety of environments, including virtual, physical, and hybrid.
- Deployment: Osirium PAM can be deployed quickly and easily, with a choice of deployment models, including standalone, distributed, and high availability.
- Integration: Osirium PAM integrates with a wide range of systems and platforms, including Windows, Unix/Linux, network devices, and cloud services.
- APIs: Osirium PAM provides APIs for integration with other systems and tools, enabling custom development and automation.
- Protocols: Supports a range of protocols, including SSH, RDP, and Telnet, to provide secure access to a wide range of systems and platforms.
- Authentication: Supports a variety of authentication methods, including password, public key, and biometric, to ensure secure access to privileged accounts.
- Session recording: Records and audits privileged sessions to provide a complete record of activity for compliance and security purposes.
- Reporting: Provides detailed reporting and analytics on privileged access activity, including who accessed what systems, when, and from where.
- Threat detection: Detects and alerts on suspicious activity to quickly identify and respond to potential security threats.
- Scalability: Osirium PAM is a highly scalable solution that can be deployed across a large enterprise with multiple systems and platforms.
Dashboard
This provides an overview of the most important information and metrics related to the system and its usage
Logins

My Access
This tab is used to manage the access and permissions for a specific user
My Requests
This tab is used to manage and track access requests made by a specific user
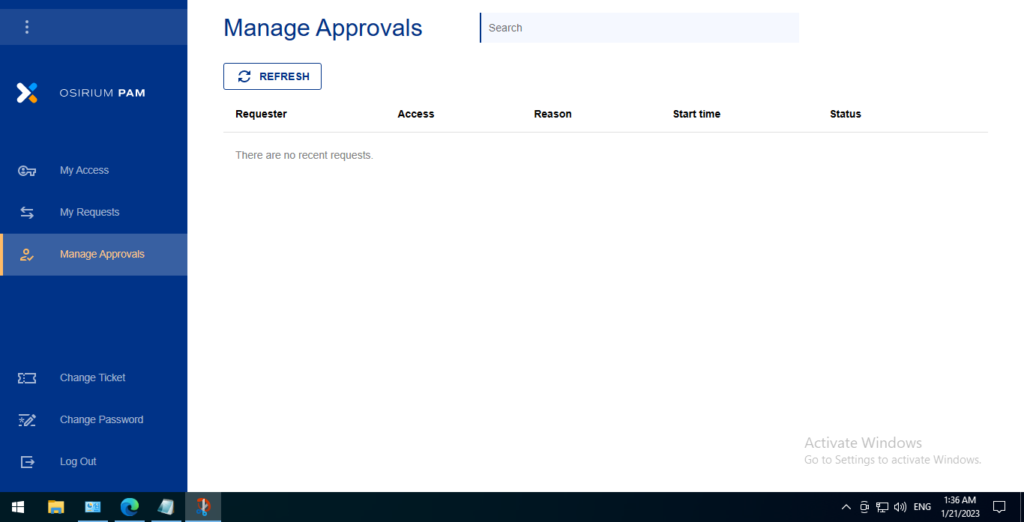
Manage Approvals
This tab is used to manage and approve access requests made by users.
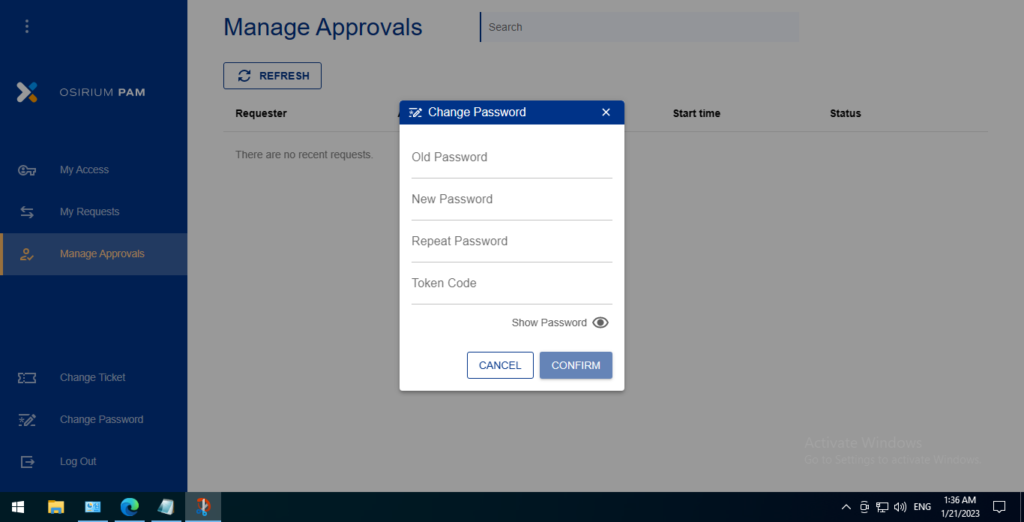
Change Password
Configuration
Navigate to My Access and choose Browser.
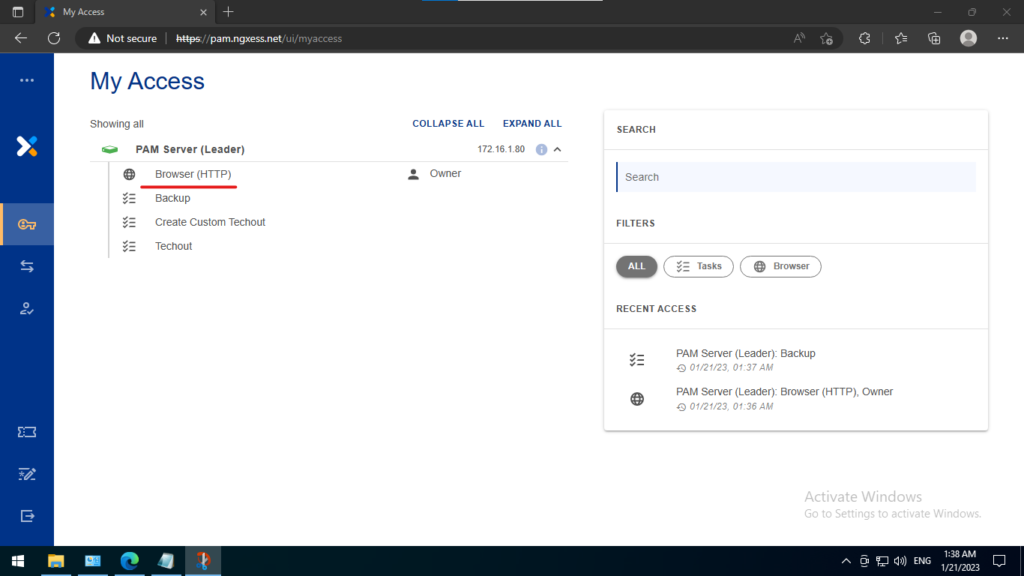
Recommended settings will be shown.
Manage -> User
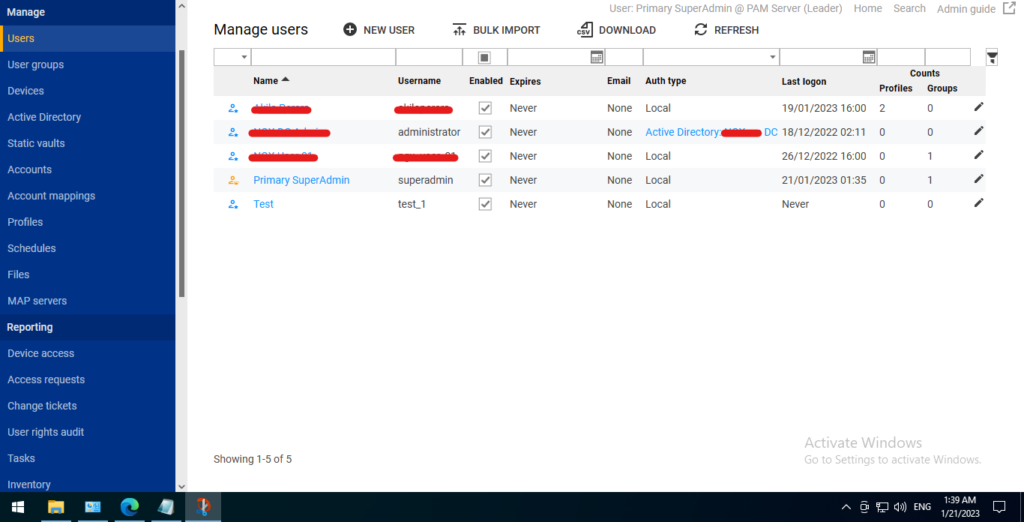
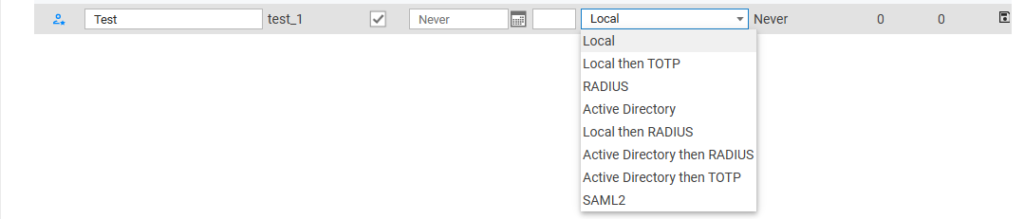
The “Manage Users” tab in Osirium PAM is used to manage and configure user accounts within the system. This tab provides features such as:
- User creation: Ability to create new user accounts and assign roles and permissions.
- User management: Ability to manage existing user accounts, including modifying user information, changing passwords, and disabling accounts.
- Role assignment: Ability to assign roles and permissions to users, defining what systems and applications they can access and what actions they can perform.
- User groups: Ability to create and manage user groups, making it easier to manage large numbers of users.
- Delegated administration: Ability to delegate administration to other users, allowing them to manage users and permissions within specific parts of the system.
- User activity reporting: Ability to view and report on user activity, including what systems and applications users have accessed and what actions they have performed.
Manage -> Device
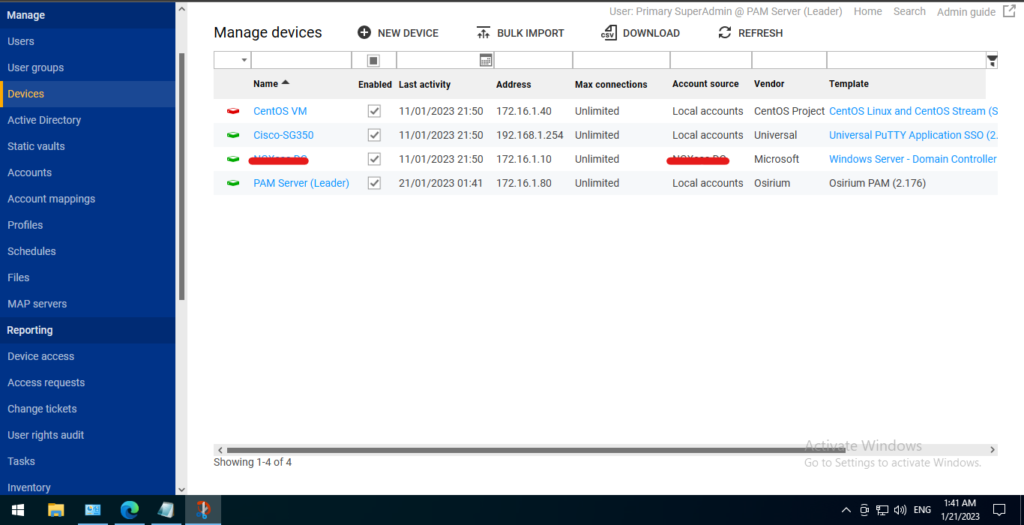
The “Manage Devices” tab in Osirium PAM is used to manage and configure the devices that are connected to the system. This tab provides features such as:
- Device discovery: Ability to automatically discover and add new devices to the system.
- Device management: Ability to manage existing devices, including modifying device information and updating firmware.
- Device grouping: Ability to group devices together, making it easier to manage and access large numbers of devices.
- Role-based access: Ability to assign roles and permissions to devices, defining which users can access and manage specific devices.
- Session management: Ability to manage and control user sessions, including logging in and logging out of devices.
- Device activity reporting: Ability to view and report on device activity, including what users have accessed and what actions they have performed.
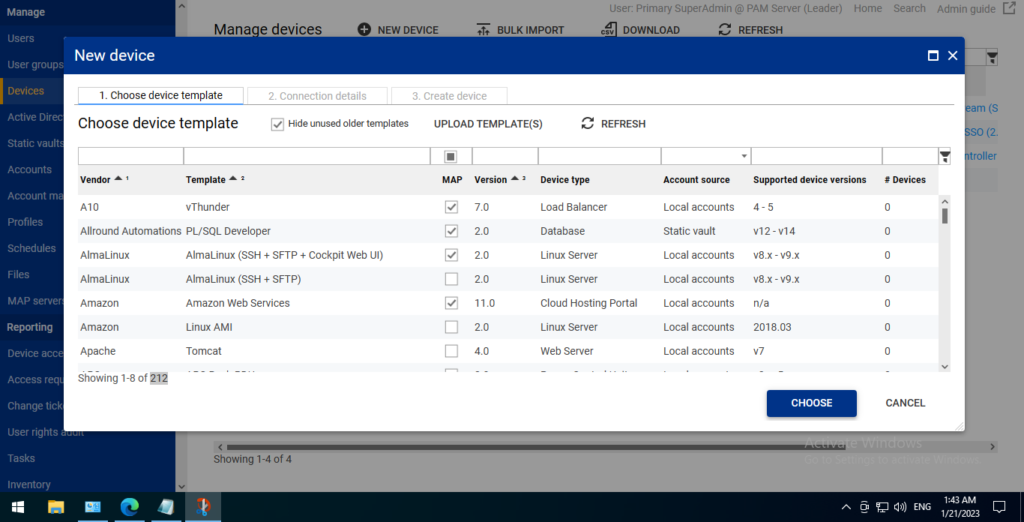
By clicking NEW DEVICE, we can configure the template and add.
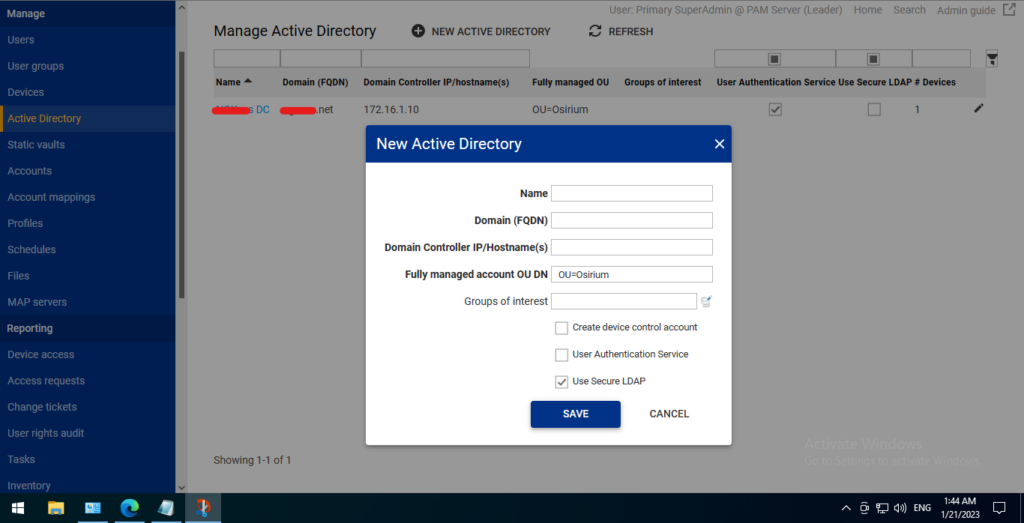
Manage -> Active Directory
The “Manage Active Directory” tab in Osirium PAM is used to manage and integrate the system with Microsoft Active Directory (AD). This tab provides features such as:
- AD Integration: Ability to integrate Osirium PAM with Microsoft Active Directory, enabling users to authenticate using their AD credentials.
- AD User Import: Ability to import users and user groups from Active Directory, making it easier to manage large numbers of users.
- AD Role Mapping: Ability to map Active Directory roles and permissions to Osirium PAM roles and permissions, ensuring that users have the correct access to systems and applications.
- AD Password Management: Ability to manage and control password policies for Active Directory users, ensuring that passwords are secure and compliant with security standards.
- AD Activity Reporting: Ability to view and report on Active Directory activity, including what users have accessed and what actions they have performed.
Manage -> Accounts
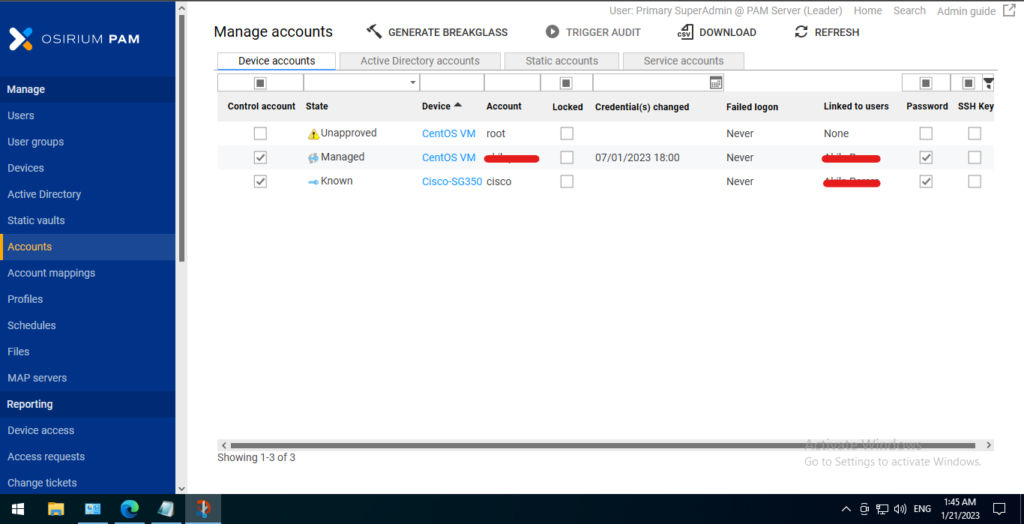
The “Manage Accounts” tab in Osirium PAM is used to manage and configure the accounts that are used to access systems and applications. This tab provides features such as:
- Account Discovery: Ability to automatically discover and add new accounts to the system.
- Account Management: Ability to manage existing accounts, including modifying account information and updating passwords.
- Password Vaulting: Ability to securely store and manage passwords for accounts, reducing the risk of password-related security breaches.
- Role-based Access: Ability to assign roles and permissions to accounts, defining which users can access and manage specific accounts.
- Session Management: Ability to manage and control user sessions, including logging in and logging out of accounts.
- Account Activity Reporting: Ability to view and report on account activity, including what users have accessed and what actions they have performed.
Conclusion
In conclusion, Osirium PAM (Privileged Access Management) is a powerful security solution that can help organizations to secure, control, and monitor access to sensitive systems and data. It provides an additional layer of security around privileged accounts and credentials, which are often targeted by cyber attackers, thus reducing the risk of unauthorized access, data breaches, and cyber attacks. Osirium PAM allows organizations to manage and monitor privileged access to systems, networks, and applications, and also allows to delegate access to privileged accounts to authorized personnel and automatically rotate credentials to reduce the risk of compromise. The solution can be integrated with other security solutions, such as SIEMs, SOCs, and MDMs, making it a versatile and flexible solution for organizations of all sizes and types. Implementing a PAM solution like Osirium can help organizations to comply with regulatory requirements and industry standards, and can provide peace of mind that their sensitive systems and data are protected from cyber threats. Overall, Osirium PAM is an essential tool for any organization looking to secure and control access to privileged accounts and credentials.
For more information check out their official website – Osirium Pam